Hackers at Def Con's voting machine village made quick work of showing just how vulnerable 'secure' voting machines really are.
At Def Con’s hacker voting machine village, where 30 pieces of election equipment sat waiting, hackers were given a deliciously wicked goal. John Hopkins computer scientist Matt Blaze said, “We encourage you to do stuff that if you did on election day they would probably arrest you.”](https://www.forbes.com/sites/thomasbrewster/2017/07/29/def-con-hacking-election-voting-machines)
And they did. Most of the voting machines were purchased via eBay, but some did come from government auctions. Despite the various different manufacturers of the voting equipment boxes, there was a common theme—they are [“horribly insecure.”
Granted, come election day, officials would likely notice if hackers were physically taking apart the machines. Tinkering with an external USB port on a computerized voting box and using it to upload malicious software may or may not get noticed. Yet those are not the only ways hackers could potentially influence votes and an election’s outcome; there’s the sneaky way of remotely accessing the machine from a laptop.
Hacking WinVote machines
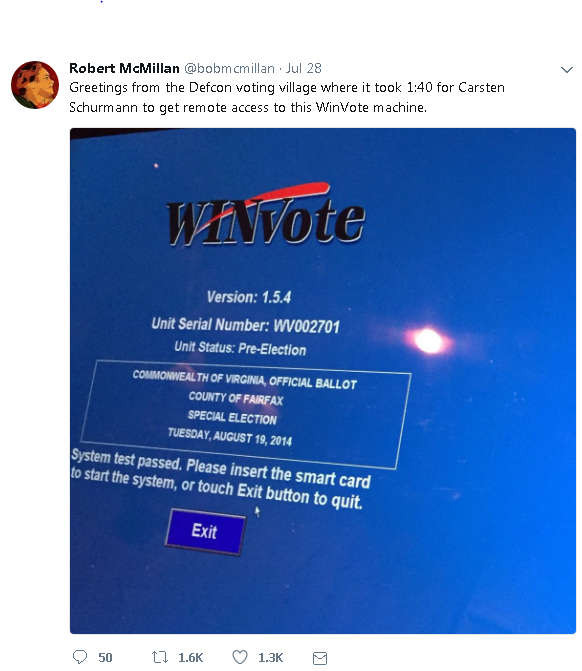
As journalist Robert McMillan pointed out, it took less than two minutes for one participant to get remote access to a voting machine. He tweeted: “Greetings from the Defcon voting village where it took 1:40 for Carsten Schurmann to get remote access to this WinVote machine.”
WINVote boxes have horrific security, according to Victor Gevers. The WINvote machines run Windows XP, have autorun enabled and include a hard-coded WEP Wi-Fi password.
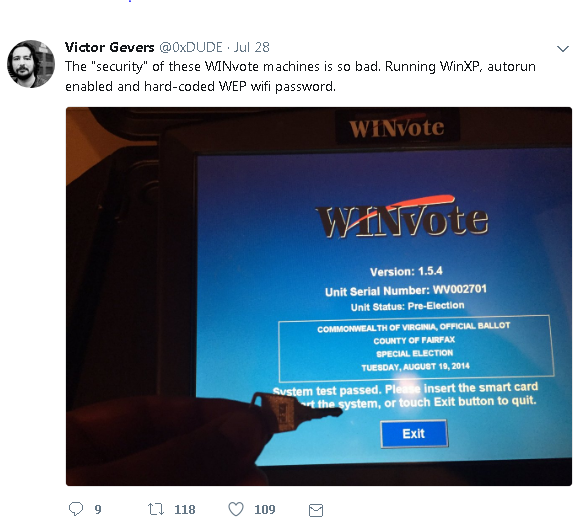
Tweet

Tweet
Can you imagine trying to vote and instead being rickrolled? Yes, hackers were able to load the infamous Rick Astley video onto a WINVote box.
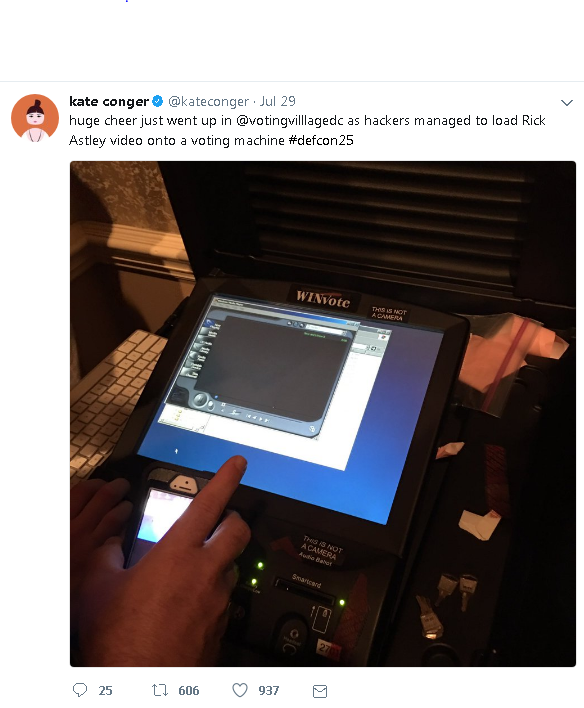
Tweet
Thankfully, WINVote machines are no longer being used. That doesn’t mean all vulnerable voting boxes have been put out to pasture, though.
Hackers “also penetrated the hardware and firmware of a kind of touch-screen voting machine used in hundreds of jurisdictions across the country, and could attack a simulated county voter registration network, like the networks in 21 states that were compromised by attackers last year," McMillan reported in a Wall Street Journal article.
Preventing voting machine hacks
“All of these touch-screen machines are unauditable,” said election technology security specialist Harri Hursti. “You should have paper ballots, and there should be an audit process.”
Barbara Simons, president of Verified Voting, hopes the hacking village helps provide the “momentum for repairing our broken voting systems. There is a solution, and it’s not rocket science.”
“One of the things we want to drive home is that these things are ultimately software-based systems, and we know software-based systems have vulnerabilities. That just comes with the territory,” Blaze told Forbes. “We want to make the problems public, so they can be fixed, so the public will know what the problems are and will be able to demand their systems be improved.”
Jake Braun, one of the organizers of the event, told Reuters, “There’s been a lot of claims that our election system is unhackable. That’s BS. Only a fool or liar would try to claim that their database or machine was unhackable.”
“The scary thing,” Braun told The Register, “is we also know that our foreign adversaries—including Russia, North Korea, Iran—possess the capabilities to hack them, too, in the process undermining principles of democracy and threatening our national security.”
Blaze pointed out, “The stakeholders for voting machines are everyone in the country. So it’s important the problems get !
Written by Ms.Smith at CSO Source

Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
http://www.csoonline.com/article/3211499/security/def-con-hackers-showed-how-easily-voting-machines-can-be-hacked.html
Hi. I am a volunteer bot for @resteembot that upvoted you. Your post was chosen at random, as part of the advertisment campaign for @resteembot. @resteembot is meant to help minnows get noticed by re-steeming their posts
To use the bot, one must follow it for at least 3 hours, and then make a transaction where the memo is the url of the post.
If you want to learn more - read the introduction post of @resteembot.
If you want help spread the word - read the advertisment program post.
Steem ON!