https://xakep.ru/2016/08/29/ripper-atm-malware/

Researchers at FireEye discovered malware, which, according to them, involved in recent robberies of ATMs in Thailand and Taiwan. Malware called RIPPER, because the source code has been detected ATMRIPPER ID. FireEye experts reported they had never seen anything like it.
This summer in Thailand and Taiwan loud robbery took place , during which the attackers abducted from ATMs of various financial institutions more than 12.3 million dollars. Criminals have acted very strange according to law enforcement officials , the attackers used malware, which infects machines and forced them to give all the money.
FireEye researchers write that they found the malware is most likely associated with these incidents. Separately, analysts emphasize the fact that a few minutes before the first article in the edition of Bangkok Post, which reported massive robbery of ATM Thailand, an unknown person has uploaded to VirusTotal sample RIPPER. Loading was carried out with the Thai IP- address.
Malware analysis showed that, among other things, the RIPPER demonstrates the same techniques previously used malware Padpin (Tyupkin), SUCEFUL and GreenDispenser. As SUCEFUL, RIPPER can control the operation of the card reader and able to command him to read information from the card, or return it. RIPPER can disable the ATM network interface, as did Padpin. Для удаления всех следов своей работы, malware применяет инструмент sdelete, который был замечен в арсенале GreenDispenser. Also, malware is able to bypass the limits set by the manufacturer of ATMs , and can cause the machine to issue more than 40 notes at a time.
But there are differences RIPPER. The researchers report that RIPPER aimed at ATMs of three well-known manufacturers. Their names have not been disclosed for security reasons, but the report said that the robbery of ATMs in Taiwan and Thailand just touched the machine vulnerable producers. Recall that according to reports the data of the authorities of countries affected ATMs were manufactured by the German company Wincor Nixdorf and the US by NCR.
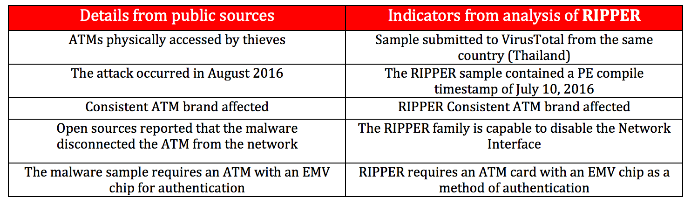
RIPPER infects the machine immediately, as soon as the ATM bank card is inserted (created by hackers with the EMV- chip). Although malicious programs resemble tactics showed family Skimmer, it's not a very common technique.
"Besides the fact that this method requires a high degree of technical ingenuity, attacks like the one that fell on the Thai ATM, require the coordination of physical and virtual operations. This shows an impressive preparation robbers", - experts say.
With detailed technical analysis of malware can be found in the company's blog.
Photo : William Grootonk
ultratech
EEW
Congratulations @ultratech! You have received a personal award!
Click on the badge to view your own Board of Honor on SteemitBoard.
For more information about this award, click here
Congratulations @ultratech! You have received a personal award!
Click on the badge to view your Board of Honor.
Do not miss the last post from @steemitboard:
SteemitBoard World Cup Contest - Play-off for third result
Participate in the SteemitBoard World Cup Contest!
Collect World Cup badges and win free SBD
Support the Gold Sponsors of the contest: @good-karma and @lukestokes
Congratulations @ultratech! You received a personal award!
You can view your badges on your Steem Board and compare to others on the Steem Ranking
Vote for @Steemitboard as a witness to get one more award and increased upvotes!