
Introduction
About 44 percent of all security incidents happen due to the exploitation of mobile devices, followed by Phishing at 42 percent, which further suggest vulnerability to threats due to human mistakes or carelessness. Notable compromises also include Employee Error at 37 percent, Social Media and Engineering at 31 percent and Consumer Technology Exploitation like webcam and home automation at 27 percent. NOVAM protects IoT devices and keeps individuals safe by using Distributed Ledger Technology to assist in the monitoring of endpoint device threats that target consumers and enterprise. In 2018, it was estimated that 38 percent of all cybersecurity incidents were caused by human errors which was a 13 percent increase from the previous year. NOVAM alleviates sophisticated cyber attacks aimed at enterprise networks and connected devices, as well as inadvertent incidents, by leveraging Distributed Ledger technology to offer businesses and organizations an automated approach to protection. NOVAM’s Forensic Security Investigation includes proactively identifying and immediately investigating incidents that have the potential to become malicious attacks and/or threats whether intentional or unintentional.
Due to the fact that people and organizations can’t continue to go unprotected against cyber attacks and living in a bubble is not an option, NOVAM draws its inspiration from the inborn flexibility and purging that the human immune system uses to eradicate threats and ensure health. NOVAM supervises entire networks, infrastructures and end points to establish full seamless views of global communications and threats. NOVAM’s machine learning, probabilistic mathematics, patent-pending tactics and methods can enable action without prior knowledge of the threat. Proactively, NOVAM is designed to identify, monitor, alert and in some cases initiate an immune system response that automatically mitigates, removes, replaces or quarantines the threat. The NOVAM Token is a utility software license that provides access to our network and platform for services that include monitoring and mitigating threats, auditing and regulatory compliance. NOVAM leverages biomimicry concepts by marrying artificial intelligence and distributed ledger technology to imitate the human immune system. This is because much like the human body, businesses, organizations and people are constantly under attack, whether they know it or not.
Fortunately, just as the human immune system acts as the body’s own army, shield and counterattack against a constant stream of possible infections and toxins, NOVAM fights to protect clients against cybercrime and breaches. Our focus is on threat detection and analytics for companies that have customers and want the assurance of an immutable record for auditing, compliance, and investigation needs. A NOVAM Token is used as an individual software license to access the distributed ledger capabilities, including but not limited to services of monitoring, mitigation, auditing and compliance. NOVAM intends to target major industries by creating partnerships with security vendors for immutable compliance and investigation. NOVAM will also target hardware and software vendors to integrate the distributed ledger within IoT devices and enterprise networks for monitoring and mitigation services through our patent-pending system health check.
Our market focus breaks down into three distinct categories:
Monitoring IoT devices and systems.
Threat mitigation of IoT devices and systems.
Auditing and compliance for threat monitoring platforms.
Supervised Machine Learning
Supervised machine learning is an approach that maps an input to an output based on example input-output pairs. Traditionally, it allows sanitized training data to be fed into a system to determine an outcome. In the context of information security, an antivirus can recognize ‘known’ malicious threats that have been previously-seen, properly labelled, and uploaded to a database for future cross-reference. The disadvantages of supervised machine learning in information security:
Malicious behaviour that changes shape may become unrecognizable by signature and can compromise a system.
Improperly labelled data prevents a system from accurately classifying malicious behaviour, seriously compromising a system and increasing exposure to undetected threats.
Labelling the training data manually increases time and costs.
Unsupervised Machine Learning
Unsupervised machine learning is unique because it attracts inferences from unlabeled data and determines previously undefined or unrecognized patterns and relationships. The benefit of unsupervised learning is the ability to detect unknown behaviours, without prior knowledge, which helps human security investigators when searching for threats. NOVAM strives to develop and deploy a precise unsupervised machine learning suite, to analyze universal network data and endpoints at scale, embrace the unknown and secure. Without knowing about previous threats, NOVAM empowers autonomous classifications of system normality to spot current cyber-attacks. New behaviours that vary may be a sign of threats, compromise, identification needs, investigation or isolation. The impact of NOVAM’s unsupervised learning on cyber security is imperative:
Insider threats, which would otherwise go undetected, can be identified, investigated and thwarted.
Total network visibility and superior detection levels ensure networks have internal defence mechanisms competent enough to combat against new-age threats.
Autonomous responses facilitate quicker cyber-threat protection and human analysis.
The Immune System
The speedy detection of cyber-threat and attestation in an enterprise is significant to the health of the network and protection of sensitive data. In lieu of pre-defining what a bad actor and malicious behaviour looks like, we aim to build an embryonic, self-adaptive, model of “normal” activity and behaviours to detect and avert abnormalities. A lot of existing security vendors have clouds where information about threats is fed in. Although not obligatory, if all the individual systems are learning individually on the customer network, an AI should take advantage of information from other AI systems in the marketplace. The immune system builds thorough network “vital sign” models of every user, device and network communication, making sure that there is complete network immersion and understanding of “self”. Using machine learning, the immune system is modelled after “self or state” of a device to establish normalized actions and pair signature-less static prevention with behaviour detection. Endpoint and network activity is monitored to detect malicious behaviour perpetrated by any type of threat, from advanced malware, to exploits and insider threats.
Threat Detection and Classification
NOVAM’s strategy towards network and endpoint information security is powered by sophisticated machine learning algorithms, unsupervised learning and autonomous, self-learning defence mechanisms. The understanding of an organization’s rapidly developing network activity and individual device behaviour is crucial to help enterprise security analysts in detecting, investigating and mitigating threats in a noisy network environment. Our algorithmic strategy aims to filter out false-positive threat indicators, identify and alert security analysts and executives of critical perceived threat. Key features include:
Robust: Evolves with your organization and systems environment.
Self-learning: Understands normal user, device and network behaviour.
Probabilistic: Ranks probability of intrusion and threat.
Real-time: Extracts emerging threats.
Data agnostic: Identifies, analyzes and extracts all data.
Relationship Correlation: Models user, device and network behaviour.
Attestation: Executes threat analysis, mitigation, remediation and forensics.
Threats are automatically classified according to risk measurements and security teams will have the ability to assess threats based on the organization’s incident response plan, corporate policies and regulatory compliance. NOVAM’s Immune System Defence applies unsupervised learning, mathematical approaches and autonomous reaction aims to respond rapidly to different cyber-attacks. NOVAM immobilizes, removes and/or slows down threats to prevent network-wide disarray. Security teams will have more time to investigate dangerous cyber-threats as they emerge. This results in user, device and network uptime, and a decline of financial, operational and reputational damage.
The Immune System Defence can provide the following:
Immunizes specific perceived threats.
Quarantines or semi-quarantine users, devices and system files.
Identifies content for additional investigation, tracking and forensics.
Rolls back files that have been manipulated.
NOVAM Immune System
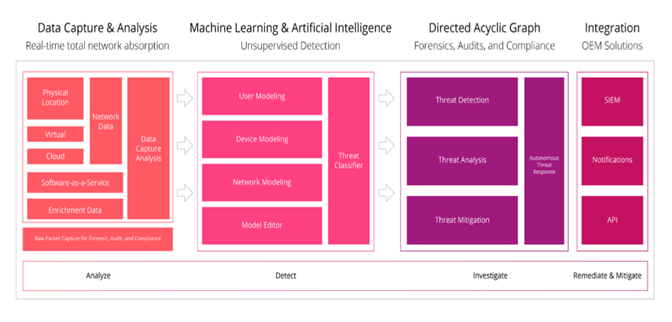
NOVAM can protect all network endpoints against every type of attack, at every stage in the threat lifecycle:
Complete visibility into all endpoint activity with minimal impact on performance.
Dynamic behaviour analysis to detect threats across all major vectors.
Autonomous threat mitigation and remediation.
Novam’s 5 step process device health checks is as follows:
- Initiate a health check for a device. This can occur both in the boot process and during runtime, and include the entire Chain of Trust or an individual statistic like firmware, operating system or applications.
- The state of a device is recorded on an enterprise specific CDN. This can be used as an external element for future device health checks.
- Subsequent health checks compare the internal and external state of a device with NOVAM stored internal and external states, signed by the vendor, to determine if the device is healthy or compromised.
- When a device is considered healthy and unmodified no mitigation occurs.
- If the device is considered unhealthy and compromised, based on the system health check, autonomous mitigation will occur.
System Security
System security is designed to protect both software and hardware, which allows all devices and codes to act in unison across every core component while participating in the network. This includes boot-up process, software updates on various levels and Secure Enclave hardware. This architecture is central to mitigating threats and securing sensitive data in the digital age. The purpose-built integration of hardware, software, and services ensure that each component of the system is trusted and that the system can be validated as a whole. From initial boot-up to software updates to applications, each stage is analyzed securely to ensure that hardware and software are protected. The NOVAM Network includes a secure boot chain, chain of trust, a root of trust verification and user and device authentication health checks to ensure devices are enforced properly.
Novam’s Approach: Directed Acyclic Graph (Dag) Architecture
A Directed Acyclic Graph (DAG) is a data structure that is topologically sorted sequentially. Although it is a distributed ledger, like blockchain technology, DAGs do not integrate blocks or blockchains – rather, DAG transactions are linked from one to another. This works by requiring nodes that wish to submit new transactions to validate multiple existing transactions before they can publish one of their own to the network. This process increases efficiency, lowers latency, and enables greater scale for the solution.
Dag Vs Blockchain
On blockchain networks such as Bitcoin and Ethereum, transactions are mined into blocks which point to the previous block, which creates a chain of blocks that maintains order. It’s common for two miners to create a new block at the same time. In such a situation, one block will have to be orphaned, meaning the power (both processing and electrical) used to validate those transactions are wasted. DAGs replace a standard block with a single transaction. This makes it so that every transaction is directly involved in maintaining the sequence. Several transactions can be created concurrently which contributes to the stability of the network, rather than being discarded. This also eliminates the need for mining, making the overall network more efficient.
Target Market by Industry
Telecommunications: The telecommunications industry plays a significant role in an ever-connected world. In order to create, operate and manage the intricate infrastructure used for voice and data transmission, telecom providers share and store enormous amounts of sensitive data every day. In a quickly-evolving threat landscape, telecommunications organizations are particularly defenceless when it comes to cyber-attacks. Adoption of virtual environments has helped streamline processes throughout remote locations but brings about new challenges to protect and monitor expanding intricate network infrastructure. Complete visibility into physical and cloud environments and a complex global network allows NOVAM to monitor, detect and respond to threats internally using our Immune System Defence and endpoint health check solution for remote IoT devices.
Transportation: Mobility and transportation are very important to nations, car manufacturers, shared-economy networks, and mobility-as-a-service (MaaS) providers. New international initiatives have changed travel and logistics by using autonomous, highly connected machines for transportation, electronic ticketing, payment services, bookings, and end-to-end trip planning. The digital transformation will go further with smart cars, unmanned aerial delivery and transportation to connected maritime vessels with IoT transportation and mobility helping to shape and mould the next decade. The new trend of smart devices that help in transportation and mobility for citizens and visitors will improve the world around us by providing convenience and safety. NOVAM’s mission includes securing IoT endpoints of all types using our health check solution and Immune System Defence.
Consumer Electronics: By the year 2050, there will be about 50 billion connected devices ranging from phones, computers, wearable devices, smart home appliances, security cameras, smart audio, TVs and more. The Internet of Things and its widespread use of applications in daily activities have already changed lives. Personal privacy, unauthorized controlled devices and service interruption are only a few of the concerns that have been newsworthy in recent years. The Internet of Things has hundreds of protocols to address diverse aspects of the IoT ecosystem, including applications and machine-to-machine (M2M) communications. IoT devices will continue to be targeted, but NOVAM’s system health check can verify a device is healthy, without infection and/or automatically install patches to fix infected devices.
Smart Buildings and Cities: By the year 2020, it is expected that the global smart city market will reach $1.5 trillion dollars. The rise of IoT innovation offers cities new ways of becoming operationally resourceful, reducing costs, improving city management, providing infrastructure resilience, creating environmental sustainability and attracting new organizations. Smart City IoT includes a wide range of solutions:
Smart Energy: Digital Management of Energy - smart grids, smart meters, intelligent energy storage.
Smart Buildings: Automated Intelligent Buildings; smart HVAC, smart lighting equipment, smart elevator systems.
Smart Technology: Seamless connectivity; 4G & 5G connectivity, super broadband, free city Wi-Fi.
Smart Infrastructure: Digital Management of Infrastructure; sensor networks, digital water and waste management, smart parking, traffic management and public transportation.
Smart Citizen: Civil Digital Natives; use of green mobility options and smart lifestyle choices.
Smart Security: Intelligent Threat Detection; surveillance, biometrics, simulation modelling and crime protection.
Smart Government: Disaster management solutions, alert systems and more.
The Internet of Things promises to make great contributions to our society within cities, but IoT’s connected infrastructure can also expose us to greater cyber-threats.
Government and Defence: Whenever governments, defence departments and defence contractors are hacked, it opens organizations and citizens to considerable damage. Weaknesses include identity theft, election manipulation, stock market manipulation, and crucial national security of our military, officials, war-time defences and infrastructure. Advanced Persistent Threat (APT) attacks well-financed, often state-sponsored, with a specific agenda, are used with the goal of gathering sensitive data to advance political, economic and military objectives in the future. Access to tools and data, enable rapid intelligence reporting and the measures needed to accomplish operations to the best of an employee’s abilities whether a contractor or government employee. NOVAM’s technology can assist security investigators in multiple categories from hardware and application verification to network intrusion.
Industrial and Manufacturing Internet-Of-Things: The most rapidly increasing Internet of Things market isn’t consumer electronics, its Industrial Internet-of-Things (IIoT). Estimated to reach $933 billion by 2025, universal manufacturers will invest $70 billion in IIoT solutions by 2020. Accenture estimates IIoT could add $14.2 trillion to the global economy by 2030. Integration with networked sensors and software, additional endpoints, remote monitoring and access, and machine digitization empowers IIoT to help with utility on a daily basis. With the implementation of IIoT devices, multi-cloud architecture, and system interoperability, comes additional vulnerabilities and threats to businesses and organizations. From manufacturing to significant industrial national infrastructure, securing endpoints, systems, user and device identity is very important. NOVAM’s Immune System Defence will enable endpoints, network, multi-cloud configurations and user privilege protection with autonomous monitoring, identification, and response to threats.
Digital Security and Surveillance: According to Markets and Markets, digital security surveillance (DSS) is estimated to become a $68 billion industry because of the reduction of price of components, increased demand for surveillance, usability and services. DSS is utilized globally for emergency management, infrastructure protection, public safety, process automation, control access management, traffic flow study and more. Insider threats with privileged credentials can evade controls intended to monitor external attack threats. A clever spear-phishing attack can allow access to internal servers and controls without alerts. An ordinary spear-phishing email can allow malware onto your computer or home network without detection. Unnoticed, it can then spread to all other devices on the same network and allow full control of your system. NOVAM can assist all industries in protecting their businesses and organizations.
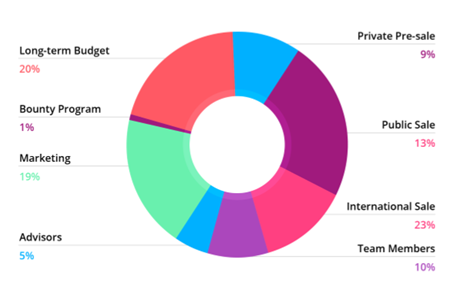
Token Distribution
Token will be distributed as follows:
Conclusion
As technology continues to grow, threats and anomalies are more ever-present than ever. Malicious attacks can come from anywhere, at any time from people and/or machines. The chances of someone or something discovering vulnerabilities, stealing private data and doing damage to organizations and individuals are higher than ever. As companies and networks progress, so must the tasks and responsibilities of IT teams. Many IT professionals are charged with finding and mitigating attacks and anomalies manually. Unfortunately, with more human interaction comes a higher chance of human error. Inteligus Solutions (IS) built a successful business by providing identity and access management solutions in the digital security and surveillance industry. IS recognized an opportunity to merge distributed cybersecurity, artificial intelligence and distributed ledger technology to create a company whose mission is to secure and protect entire networks, infrastructures and all endpoints with an automated technology modelled after the human immune system.
NOVAM is the first Artificial Intelligence driven cybersecurity program that combines distributed cybersecurity, artificial intelligence and distributed ledger technology for a system that’s designed to be proactive, behaving like the human body’s immune system and to automatically monitor and mitigate IoT threats from the secure boot chain, operating system, mobile application and network. NOVAM’s complex protection mechanism or approach provides resistance and removal of threats without prior knowledge of the existing danger. This nature makes NOVAM an emerging, disruptive technology that’s optimized by its innate ability to automatically initiate an immune system-like response that mitigates, removes, replaces or quarantines threats. NOVAM also provides auditing & regulatory compliance integration to threat monitoring and detection services to ensure system events are included on an immutable distributed ledger. Our focus is on threat detection and analytics for companies that have customers and want the assurance of an immutable record for auditing, compliance, and investigation needs and also to become the standard distributed ledger for cybersecurity threat detection, device mitigation and compliance.
For more information visit the links below”
Published by Cryptowin1
Website: https://novam.ai/
Whitepaper: https://novam.ai/wp-content/uploads/2018/10/NOVAM-Whitepaper.pdf
Twitter: https://twitter.com/NOVAMIntl
Facebook: https://www.facebook.com/novamintl/
Profile link: https://bitcointalk.org/index.php?action=profile;u=2068163