
As Harry Halpin, CEO of Nym stated: “Nym wants to anonymize the world with software that can be applied to crypto wallets and other mobile apps to mask IP addresses and user data from the network itself.“
When compared to Tor and VPNs, Nym offers an enhanced and better solution with the use of Mixnets and by providing incentives to increase censorship-resistance and scalability. It protects the users’ network traffic and improves the existing models represented by VPNs and Tor.
It is important to note that Nym isn’t directly competing with existing blockchains but can rather help them improve their privacy. Nym has also created an alternative to Google & Facebook Sign In which is called Nym Credentials. You can use these credentials to login to websites without being tracked and monitored by anyone.]
Some historic facts
The startup Chainspace was created in 2018 by George Danezis and other academics and had 15 researchers working out of the University College London. Later on, it was acquired by Facebook which didn’t use most of the technology created by Chainspace, but rather integrated the team into its blockchain group that created the Libra project. The whole team was hired by Facebook except for a couple people. Four of the five researchers behind Chainspace’s academic whitepaper joined Facebook.
Chainspace offers a huge potential with its revolutionary “sharding” technique for blockchain technology. This technique adds extra layers, or “shards”, to a blockchain. These shards layer transactions to provide privacy and scale faster.
While George Danezis now works for Facebook, Dave Hrycyszyn, Chainspace’s Chief Executive (now Nym’s CTO) and Mustafa Al-Bassam, Chainspace co-founder, moved on to create Nym.
Of great importance is also a privacy protocol used by Nym called Coconut. According to Halpin, it was originally developed by Chainspace before it was acquired by Facebook. The novel thing about Coconut is that it provides privacy and decentralization that no other signature scheme provided so far. You can transform your credentials into something that is valid and perfectly able to use but in no way linkable back to what you already have.Nym is partially built on Cosmos, it uses some of the Tendermint code.
The next Generation of Privacy infrastructure
Today, data about every intimate aspect of our lives is concentrated in the hands of a few corporations. Government agencies harvest it without our knowledge or permission. This is destroying trust in the internet, stifling innovation, and exposing millions to privacy breaches and identity theft.
Existing end-to-end encryption models can protect the content of your communications data—but they do not protect the metadata about whom you are communicating with and when. As Edward Snowden confirmed, the National Security Agency (NSA) has been collecting metadata on a massive scale, indiscriminately spying on the entire internet. No current system can protect you against traffic analysis at scale.
Nym protects both content and metadata, keeping the relationship unlinkable between client devices at one end and service transactions at the other. Nym’s fundamental innovation is a holistic, open-source, decentralized, permissionless, and incentivized network: a secure foundation on which developers can build applications that can anonymize metadata both at the level of network traffic and at the level of applications. Nym is designed to
transmit data without access to or knowledge of the source, location or content of that data by the network or its participants.
As George McDonaugh, KR1 CEO, stated:
“There are lots of projects talking about privacy but ignoring the elephant in the room, which is the network layer. You can build privacy applications but unless they’re built on a private network, you’re only going halfway. What Harry [Halpin] and his team are doing is … using blockchains to incentivize and create network-level privacy.”
Internet Freedom & the End of Surveillance
How Nym Works
Privacy is a property of an entire system taken as a whole, not any one aspect of the system. Even if you use the most advanced cryptographic tools to secure one layer of your communication, it won’t be private if the other layers leak information. Nym’s goal is to provide privacy to all internet traffic across multiple layers by deploying a generic system that can scale by design to include the entire world.
Nym is comprised of two components:
- A decentralized mixnet that protects users’ network traffic,
improving on the models represented by VPNs and Tor. - A tokenized credential system that provides application-level privacy
and enables users to access the Nym mixnet.
The Nym Mixnet

Nym provides stronger privacy than any single-use-case mixnet or isolated application of privacy-enhancing technologies or cryptographic primitives. Because its infrastructure supports so many different applications, Nym can blend large, diverse user bases of different applications into a single massive crowd. This is a breakthrough, because in order to be anonymous when using a system, you must be indistinguishable among a group of users—and the larger the group, the better the privacy.
What is a mixnet?
Mix networks are routing protocols that create hard-to-trace communications by using a chain of proxy servers known as mixes which take in messages from multiple senders, shuffle them, and send them back out in random order to the next destination.
The Nym mixnet uses multiple hops like Tor but adds timing obfuscation via random delays and cover traffic so a powerful external observer cannot identify a user based on the patterns of their network traffic. In addition, it provides a powerful set of usability and performance features other mixnets lack. (like improved anonymous messaging)
Mixnets were first conceived by David Chaum in 1979. In the early 2000s, when Tor was being built, the internet was too slow to allow mixnets to function at an acceptable speed for everyday usage. Today, increased speed, along with a modern mixnet design developed by the team behind Nym, have rendered it possible to develop mix-networking fast enough for regular users, and without scaling limits. One of the advantages of the Nym network is that rather than slowing down with more users, the system can become faster and more private as the anonymity set grows.
Mix-mining Rewards
Nym develops on both proof-of-work and proof-of-stake designs to create a proof-of mixing system called “mix-mining.” Where proof-of-work incentivizes solving arbitrary hash puzzles, mix-mining rewards mixnodes for doing computation for privacy. Mix-mining combines the best aspects of
both proof-of-work (cryptographic proof that a mix-node and validator has acted correctly) and proof-of-stake (mix-nodes and validators place a stake in NYM tokens that can be slashed if they misbehave, while users can delegate stake to the mix-nodes and validators of their choice). Mix-nodes earn
mix-mining rewards in the form of new NYM tokens, as well as possibly fees from service providers and users of the mixnet.


Nym credentials serve as a privacy-enhanced and decentralized alternative to OAuth-based systems like Facebook Login and Google Sign-In, while sharing even less data on-chain than W3C DIDs. In effect, Nym credentials allow users to selectively disclose their data to whomever they choose, however they wish to, backed up by the power of cryptography and decentralization. Combined with mixnets, Nym provides a holistic solution to privacy that can be integrated with any blockchain and any other application.
The Nym Token
Economic incentives are necessary to encourage participation and help in avoiding network abuse. The network requires users to utilize NYM tokens. These tokens are used to pay for and are part of the provided network services.
The token is designed to be compatible with any blockchain. A Nym blockchain maintains the state of credentials and the operations of the mixnet so the Nym network can be decentralized, permissionless, and trustless.
Nym tokens provide credentialed access to privacy-enhanced and uncensored internet communication. The NYM token is a voucher for these credentials and is used to pay for network operations. For example, tokens will be used to reward those who provide services for the Nym network, such as operating a mix-node or validators for the Nym blockchain. NYM tokens have a deflationary reward schedule.
Staking is an integral component of the provision of the network services. It ensures that all the participants in the Nym network—the mix-nodes that compose the mixnet, the validators that maintain the chain, and the service providers that allow users to access their services via that mixnet—are incentivized to give users the highest quality of service via “mix-mining” rewards. Like Bitcoin, the Nym network makes it possible to take fees on transactions; as more apps and users join the Nym network, fees will overtake mix-mining rewards as the primary source of income for the operators of mix-nodes, mix guards and Nym validators.
Nym's Development team

You can learn more about Nym’s team members here: https://medium.com/@nymtech/an-introduction-to-the-nym-technologies-team
The Nym Architecture
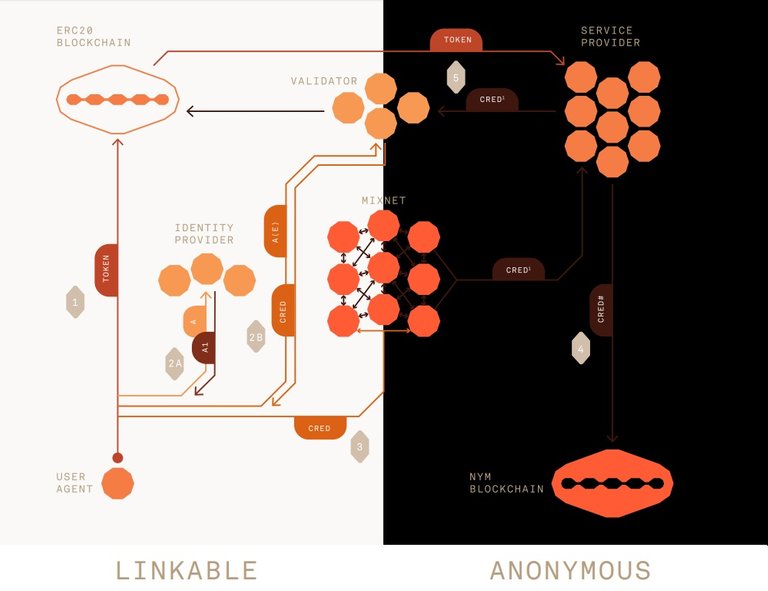
The Nym network comprises of:

Users can use the Nym mixnet to access a service and make their transactions private. They can pay directly within Nym, they can pay a service provider externally or the provider can choose to cover the costs or stake NYM tokens on behalf of a pool for the users and let them use the service for free.
How Does Nym Compare to Other Systems?
“Nym’s protocol doesn’t only anonymize at the protocol layer but also at the network layer. That is a major difference compared to something like Tor. It even mixes the data packets at the network layer, therefore anonymizing metadata such as IP addresses, geolocations, etc. It’s really one step ahead of the solutions that are out there at the moment.”
The problems:
Despite being encrypted, when using messaging services like Telegram & WhatsApp it is possible for a third party to monitor your traffic and track you. This is the problem of layer-zero privacy, or privacy at the network level.
Cryptocurrencies such as ZCash, Monero, and Mimblewimble may achieve privacy on the blockchain level but can be deanonymized by timing and associated metadata on the network level. This is true of any zero-knowledge proof system used in isolation on a single level.
VPNs appear to solve this problem but force the user to trust the VPN provider with their data, and the privacy they offer can be broken by adversaries that can observe the entry and exit points of the VPN. The providers can also fully observe all network traffic between users and the public internet, knowing exactly what services its users are accessing at a given time. The user must trust that the VPN provider is not using their information in a malicious manner or keeping logs. Sentinel dVPN which is built on Cosmos solves some of these problems and it can also be boosted by Nym.
Tor and I2P provide a more sophisticated multi-hop solution, but cannot provide strong privacy guarantees against a powerful adversary that can observe the entire network—or just its entry and exit points, as it is not anonymous towards end-to-end network adversaries. Unlike Nym, Tor is optimized for low-latency web browsing and so does not mix packets or generate cover traffic.
Nym solutions :
Nym will be an encryption network that will run across the internet. It will enable developers to build applications with enhanced data privacy without depending on Google Play or Apple’s app store. In addition, existing applications like Messengers, VPNs and file sharing, blockchain transactions & sign-on authentication services can be integrated for increased privacy and protection of the user’s data.
Every technological breakthrough like this has been followed by revolutions that transform society. If the previous generation of encryption technologies paved the way for Tor and Bitcoin, think what Nym will render possible. The risks of centralizing the internet in a handful of institutions are obvious. Today big corporations and government agencies are gathering our data without our knowledge or permission.
Nym protects both content and metadata, keeping the relationship unlinkable between client devices at one end and service transactions at the other. Nym’s fundamental innovation is a holistic, open-source, decentralized, permissionless, and incentivized network: a secure foundation on which developers can build applications that can anonymize metadata both at the level of network traffic and at the level of applications. Nym is designed to transmit data without access to or knowledge of the source, location or content of that data by the network or its participants.
The mixing defeats the kinds of traffic-analysis attacks that can deanonymize packets on VPNs, Tor and I2P. In addition, Nym uses blockchain technology to decentralize the operations of the mixnet so that the network has no centralized points of failure.
This review was a synopsis of the Nym Litepaper and was based on the info that is available today. The full technical wallpaper will be released soon.
You can learn more about Nym at the website: https://nymtech.net
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
https://www.crypto-world.gr/altcoins/nym-groundbreaking-privacy-infastracture-crypto-project-litepaper-released/