Picture coming soon
Good evening, Steemit, and all you geeks who are reading my blogs!
Today's topic is about Scanning and Enumeration of a network (or a network of hosts)- And I promise that it's going to be understandable for beginners too! :^)
So lately I got a job offer at a power station. It's not just any power station, it's also an ISP, it offers Electrician services and more. I will be working in different areas such as Security, Pentesting, Networking, and System Administration. I'm really happy about it because that means that I'm able to see what it's like inside the mind of a company that puts security at the top priority list. Also, that means more content for you guys! It's a win-win.
Diving straight into it; Today we will go through Nmap, Nikto, TheHarvester, Dirb, Sparta, and general knowledge. These tools are used for finding vulnerabilities on a network or scanning for information that could get you further in your pentest. Now it's important to note that these tools are not technically legal without written consent from the company/host you're pentesting on. Always remember that if what you're doing can be directly traced back to you, then you're pushing boundaries.
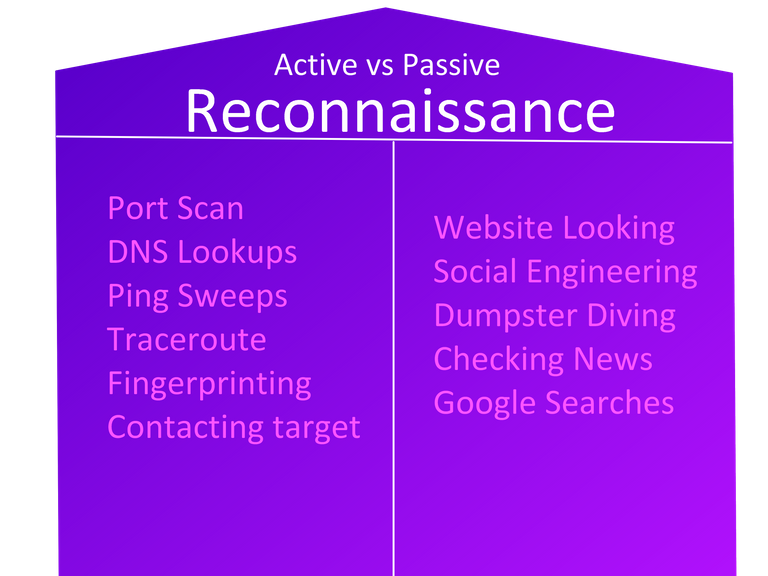
(This picture was made within 2 minutes, so please excuse the quality)
As you see here, sending a ping, directly scanning the network, contacting individuals or tracing routes, are all activities that have to do with active reconnaissance, AKA Interaction with target/company.
Searching on Google, Social Engineering without interaction, Gathering information passively are all "legal" as these are things that are publicly available. This is Passive reconnaissance. We are going to be diving deeper into the active reconnaissance and also doing enumeration and scanning, which is a step deeper; asking ourselves "Is the target online, what more is there?"
I will be using HackTheBox as my legal gateway for these pentests.
Let's go!
Nmap
Nmap, short for Network Mapper, is a free, open-source tool for vulnerability scanning and network discovery. It's used as one of the very basic and default tools when it comes to pentesting.
Simple scan: Nmap 10.10.10.160
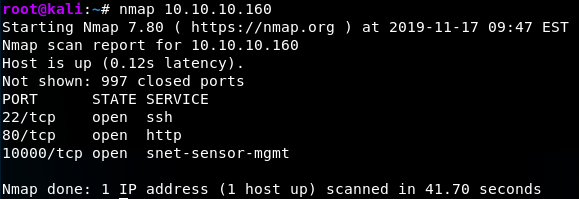
What you see here is nothing special, and just a straight forward output of a network scan from one of the HackTheBox hosts.
This part PORT gives information about which ports are open and what connection type it's using. As we can see, Port 22 is open and using TCP (Transmission Control Protocol, a connection-oriented protocol that makes sure packets get sent in the right order and that they're being delivered).
STATE is quite straight forward and explains whether the port is open or closed. If a port is open, it will accept packets, but if it's closed it will drop and reject everything that is sent to it. AKA, it's a dead end.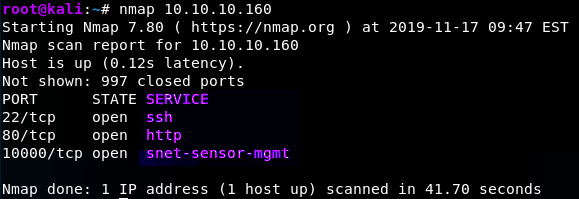
SERVICE Explains what type of operation is being done on the port. Whether it's a website, a file transfer, a mail client, etc. Here we see that SSH, HTTP and some management service being in use. By knowing SSH is open, we know that we can connect to the host if we get the username and password. By knowing HTTP is open, we know there must be a website somewhere on this host.
This can help us to continue on our pentest as we choose to check out what this HTTP open port is giving us. For that reason, I'm going to input 10.10.10.160in the URL field and see what we get.
This is the website that is being served on that IP.
Dirb
Normally we would navigate around manually and which existing web objects are present on the website, but today I'm going to use Dirbas a tool to make all that go much quicker. Dirb is a web content scanner that often aids penetration testers when finding hidden, or hard to find objects on a website. And as you can see in the picture below, with the help of a wordlist we've found a couple of directories below the root directory(the main folder). Most Kali Wordlists are available under this path: /usr/share/dirb/wordlists/vuln
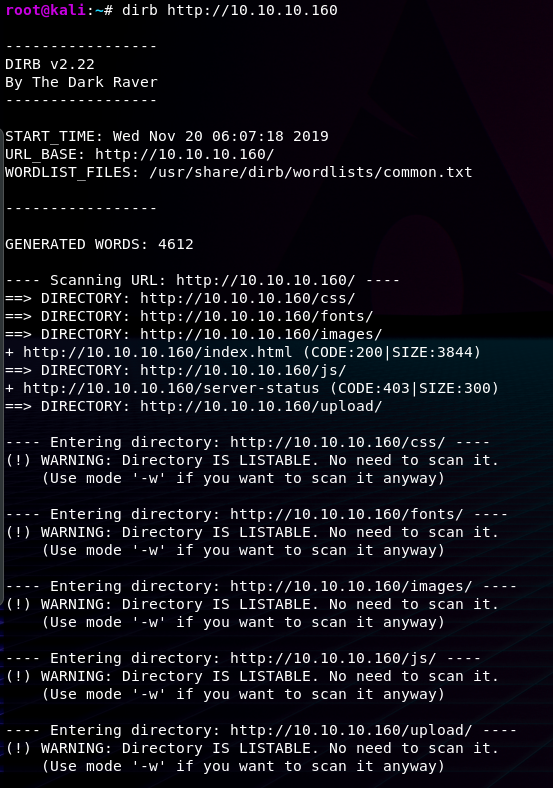
Dirb can take a very long time and needs to be given patience when doing the scan. The codes that are printed are based on which response the webserver (the website we're connecting to) gives it- whether it's existing, whether you don't have access, or whether you can see it. Here's a cheat sheet for the HTTP responses(responses from the website we're connecting to):
| Code | Meaning |
|---|---|
| 200 | OK (success) |
| 302 | Found, but located somewhere else (we need to do something else technically to find this document) |
| 403 | Forbidden error (You're not allowed to see it) |
| 404 | Error on the browser-side |
| 500 | Error on the server-side |
But as we can see in the picture, we can now navigate to the different directories and see if there are some security holes that we can try to squeeze between.
Nikto
Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items such as potential danger programs, outdated versions, version problems, server configuration items; such as the presence of multiple index files, HTTP server options, and will attempt to identify installed web servers and software.
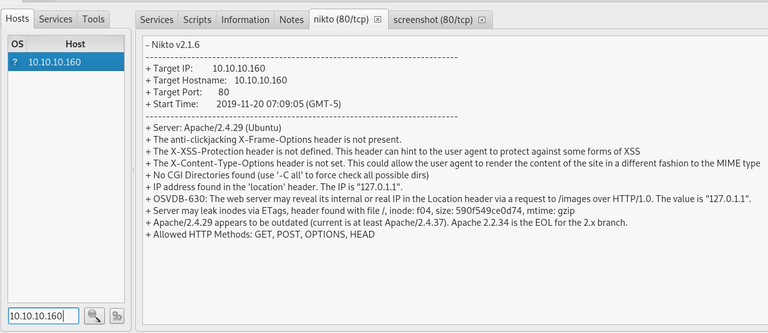
The command nikto -h http://10.10.10.160 defines which host -h you're targeting, and then giving the address for it in web format. If you had given it an IP address instead of an URL you are changing what it's looking for, as an IP address doesn't just belong to web servers, but could also belong to other devices. That's why it's important to specify with http:// on the start, or https:// for secure websites.
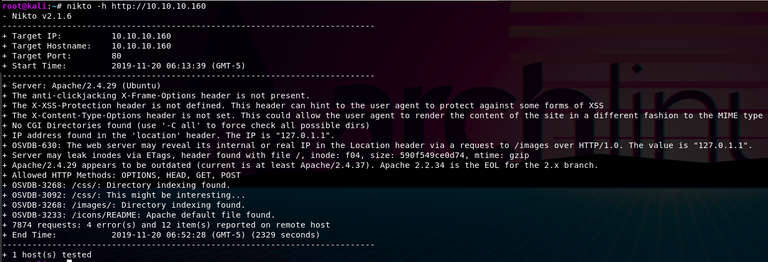
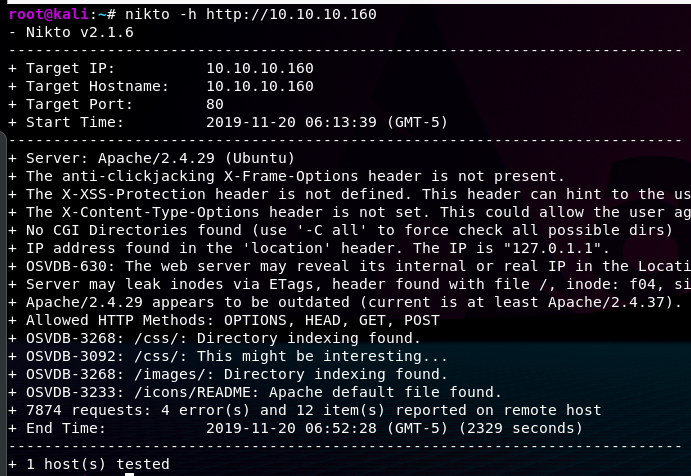
I apologize for the small picture. Please open the first image in a new window to see the cropped text.
But as we can see in the picture, it starts by giving us basic information about our targets such as the Target IP, Target Hostname, Target Port, and the start time of the scan. If you remember the nmap scan we did earlier, we had port 80 open that was using the service HTTP. This scan too is targeting port 80, which means that all of this information has to do with our website. We can see more information about the webserver than we got from our other scans, such as the allowed methods like GET and POST which are ways or receiving or sending information. This web server seems to be quite vulnerable as a lot of security headers haven't been set, and there are some leaks. I won't go deep into this, but I will just demonstrate that Nikto is quite useful to see what holes we can try to get through without having to sit and test this manually.
TheHarvester
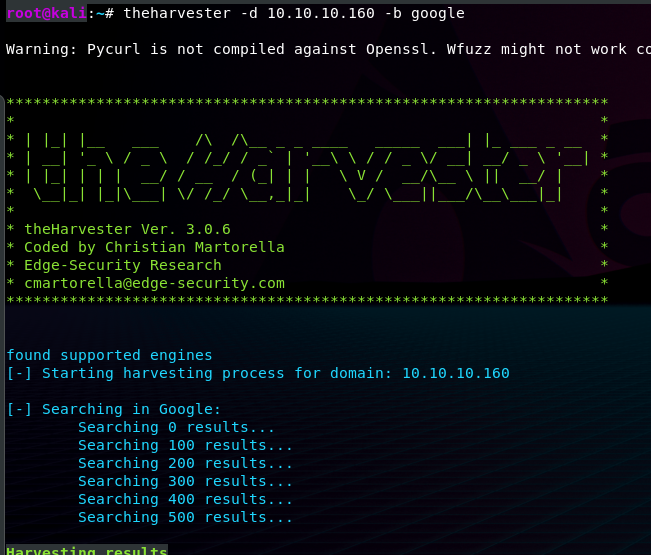
The command theharvester -d 10.10.10.160 -b google means that we're searching for the host 10.10.10.160 with the help of google, AKA using that as our data source.
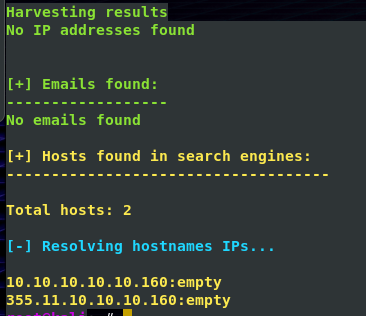
in this scan, we only looked for emails and other hosts that are related, which could give us more information about the network infrastructure. Because I'm legally pentesting on a game, and because this specific box/host isn't public nor reachable from the outside world, information about it is quite narrow. But you get the point.
Sparta
Last, but not least is Sparta. Sparta is a tool that aids penetration testers by minimizing the work done within Scanning and enumeration. It combines tools for you and helps you save time by displaying them in a convenient way. I have not worked too much with Sparta personally, but I know it can also aid in brute-forcing.
It's kind of like the burp suite of enumeration.
With the help of nikto and nmap we're able to navigate through the three tabs host, services, and tools.
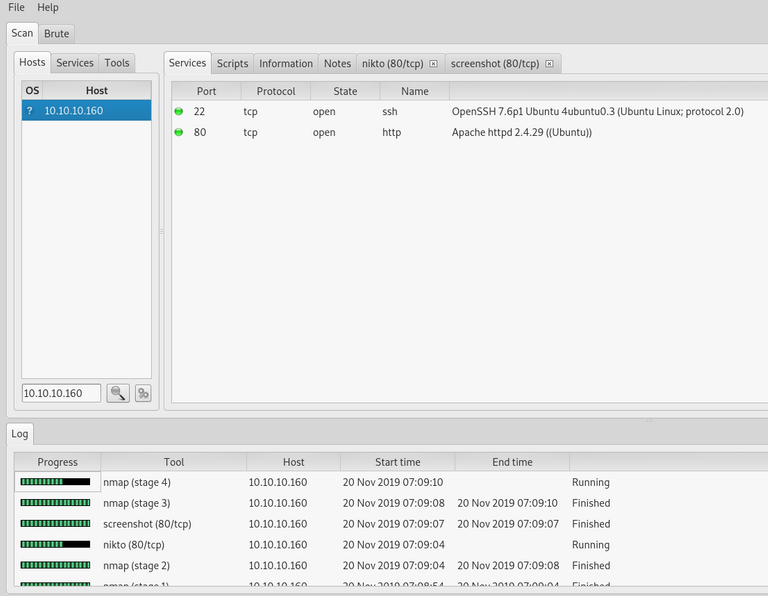
and the great thing is that you can see the scans for themselves in a nice User Interface as well.
Now I know this may have been a very long and perhaps tedious article, but I hope it was full of knowledge and that we all learned something. At the same time I tried my best to keep it understandable for those who aren't completely into the field yet, and that it was interesting to get to know these tools.
Thank you for reading this blog, see you next time! :^)