
The number 1 problem in cryptocurrencies today is that people are losing their passwords. Forget about hackers and scammers, those are nothing compared to how many people are locked out of their money due to losing a password. I see people constantly on Bitcointalk screaming for help because their password is lost.
So to avoid tragedies like these you should immediately start using a password manager. In this tutorial I am going to talk about how to setup easily and use KeePassXC, the best and safest password manager in my opinion. There you can safely store passwords or even private keys, in encrypted format.
First of all KeePassXC is an innovative fork of KeePassX with trusted developers, it's open source, so fuck the closed source password managers, you should not trust those. And it comes with tons of new features like OTP and TOTP systems as well as a better GUI.
1) Download & Verify KeePassXC -- SECURELY
Download it from here: https://keepassxc.org
Make sure it's HTTPS, verified by Let's Encrypt, the last thing you want is to download a malware from a phishing website. Then also verify the download, I'll be using the Linux portable version, and I really don't recommend people using Windows, just install a Linux operating system it's safer!
The Linux "Appimage" which is just a portable binary, but you can install it to root mode from the options available below, but I like the portable version, it can be put on a USB stick basically and the stick hidden away from thieves, so it offers strategic advantages.
In my case the version currently is 2.20 the file name is KeePassXC-2.2.0-x86_64.AppImage
Then verify the SHA256 hash by downloading that file too, for me the hash is:
d33640268b43496cb0f1906191404977d60ec6933c0ed827643c3fc1a6ac151e
Steemit posts become uneditable after 7 days so this is a good reference point to verify the authenticity, and compare this with your hash file, and the hash output of the application file which you get by opening the terminal in the same folder as the file is and typing in:
sha256sum KeePassXC-2.2.0-x86_64.AppImage
If the terminal output, the file hash (downloaded) and the hash I write above, all 3 match, then it's a good sign that the file downloaded is authentic, otherwise you could be a victim of an MITM attack.
Then also verify the signature of the file, to verify that the file comes from the developers, here is a tutorial:
Import the developer's public key:
gpg --keyserver pool.sks-keyservers.net --recv-keys 0xBF5A669F2272CF4324C1FDA8CFB4C2166397D0D2
Then download the GPG signature from the same page you downloaded the SHA sum, then open the terminal again from the same folder and check the public key against the signature, by entering this in the terminal:
gpg --verify KeePassXC-2.2.0-x86_64.AppImage.sig
It should show this:
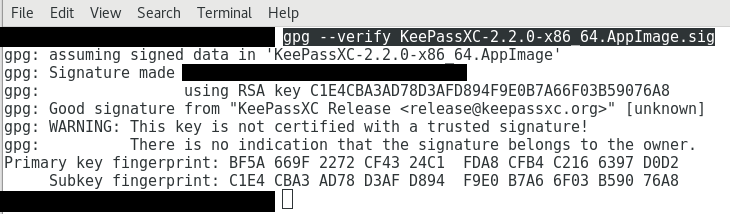
Make sure the Primary Fingerprint matches mine:
BF5A 669F 2272 CF43 24C1 FDA8 CFB4 C216 6397 D0D2
If they don't match then you have probably downloaded a malware version of it. Sorry for all this fuss, it's technical and uncomfortable, but remember we are downloading a password manager, where you will probably store all your cryptocurrencies's related passwords, and you really don't want to download a malware.
I mean it's critical for people to store their passwords safely and to know that the software they are using is real, genuine and trustworthy. So don't even think about using Windows if you are serious about security, just use Linux Mint or Debian.
2) Using KeePassXC
I am using the portable version, so just start that, make it an executable and it runs:
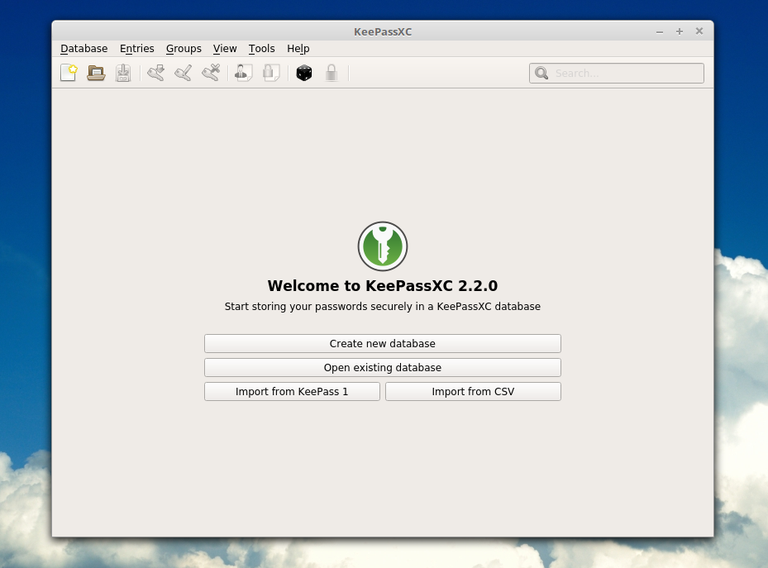
When you first run it you will have to create a database file that will store all your passwords, you will always have to back this up after adding or changing passwords in it. Obviously if you add a new password to it, it won't be present in an older file, so make sure you always back this file up.
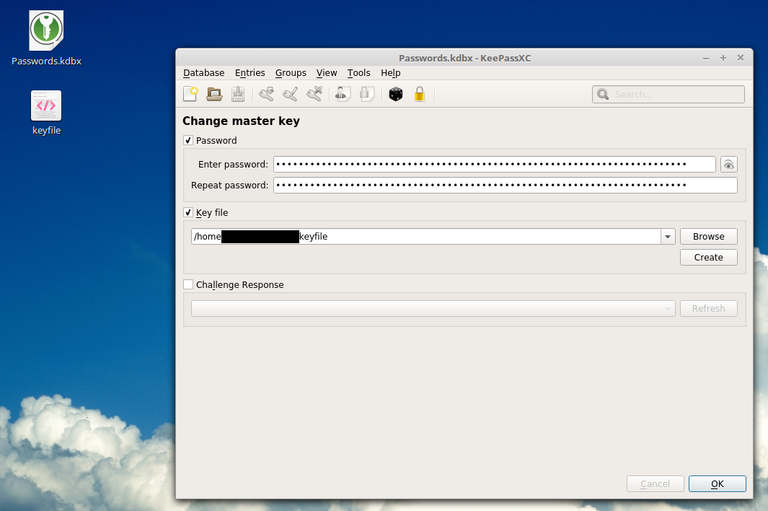
As you can see I already created a database file named Passowrds.kdbx, there are 2 ways to access it, either it's master password protected, or you open it with a key (which I have created there keyfile), or both. If the database will be master password based then use a good long strong password (which I will show you in a moment how to generate) and memorize that, write it down, or whatever. Remember without the password the database can't be opened!
An alternative is to use a keyfile, here named keyfile, which you can generate by pressing the Create button, and then copy the keyfile to like a micro-SD card and hide that away. So in this case you can just open the database when you plug in the micro-SD card, and it will remember the path of the file. Easy access, but again, if you lose the keyfile or the card, then it's all lost, so proceed with caution and make backups if necessary.
Remember the database file is basically public, it is an encrypted file so you don't have to worry about it being cracked, you can even upload it to places like Dropbox if you worry that your PC crashes, or make many copies of it to many USB sticks. Especially if the file is large like it can get up to 10-100 MB if you hold many stuff in there and add custom icons and things like that.
But the keyfile should be always kept secret, don't make that public ever, same with the master password, in fact it should be generated offline as well!
Master Password Generation
You can generate a strong password (for master password of the database for example) by clicking on the dice icon:
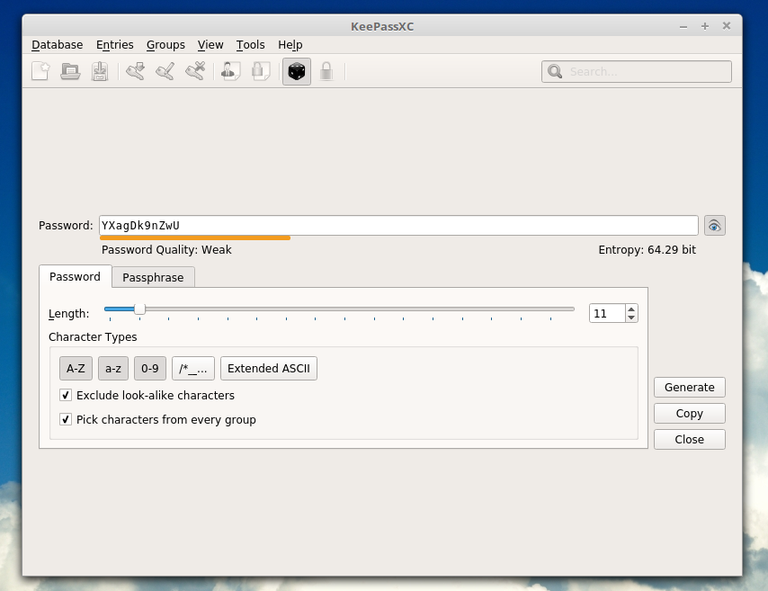
You can set there how complex the password should be (numbers,caps,symbols) but it should have minimum 128 bits entropy!
Entropy measures the "size of the haystack" of possibilities of your password, in this case 128 bits is a haystack of the size of 2128 combinations, which is pretty impossible to guess.
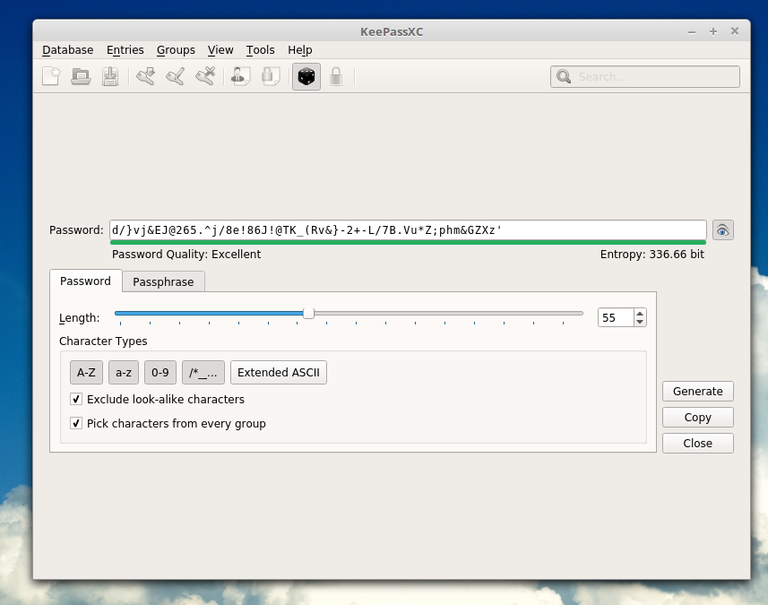
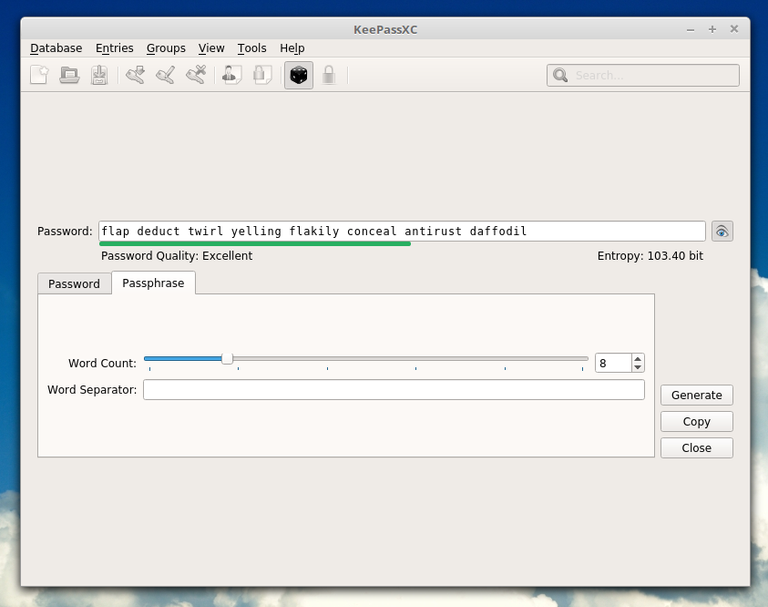
This password is decent if I can say so. Also you can use (and should use) passphrases instead which are easier to memorize:
So after you have created your database file (here Passowrds.kdbx already created), you can customize it’s strength by choosing it’s properties, by going to DATABASE>DATABASE SETTINGS:

Leave the algorithm to AES-256, but you can change the round size, if you click on benchmark it will set it to a number so that the database will open in 1 second.
NIST recommends 10,000,000 rounds I believe, so if speed is not an issue then set it to that, but if the file gets large like >10 MB then this will slow down the user experience.
So either leave it like that, but if you plan to upload the database as a backup to public PRISM places like Dropbox or Google Drive, then you should definitely set the round number to 10m or even higher!!!
Add Password Entries
Then after the database is created, backed up and customized to your needs, then start adding passwords here, or copy them out from Firefox or Chrome’s login/password bookmark lists, it’s much safer to store passwords in a database like this than in Firefox or chrome, and you can auto-type them into the login pages so no need to manually enter them.
Add a new password entry for example:
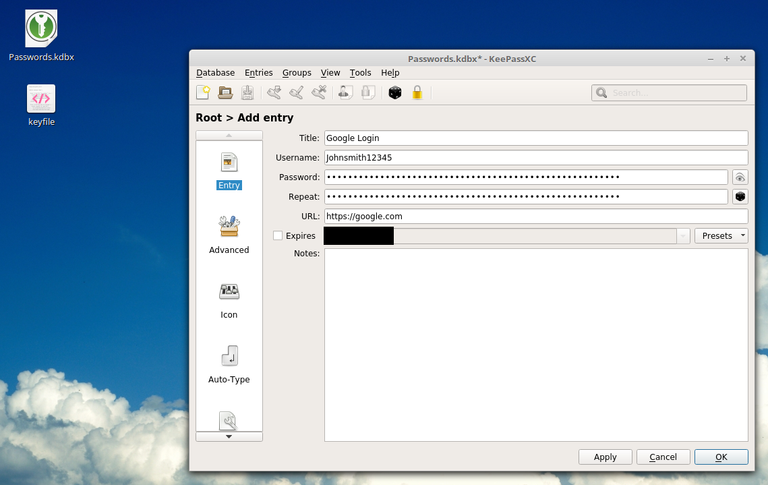
Make sure you add the URL of the login link, I think it has to be the exact full link, so for Steemit it’s not https://steemit.com but https://steemit.com/login.html so make sure it’s the exact URL.
Then choose an icon for it:
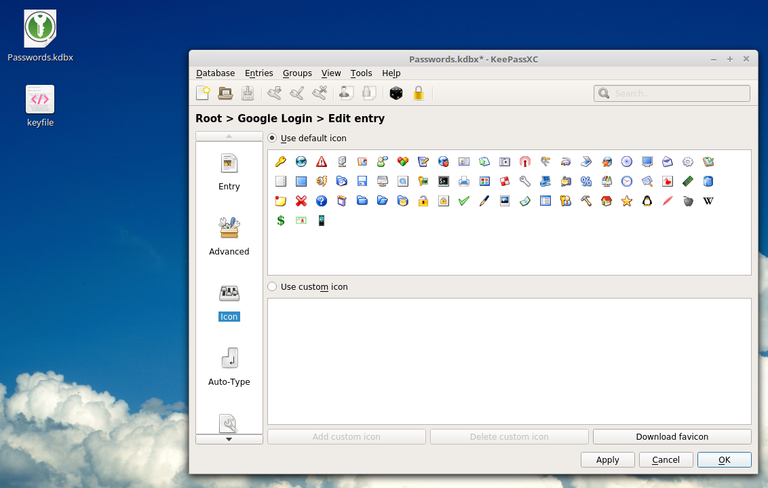
Your first entry will look like this, in the Root main folder, but you can also customize it:
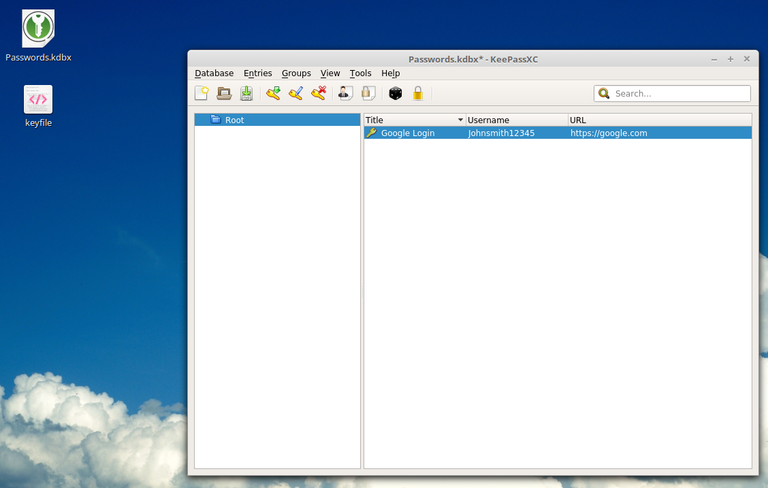
Then just add groups there fore different things, and drag entries from 1 group to the other, organize it as you wish, pretty easy to learn, just drag items basically:
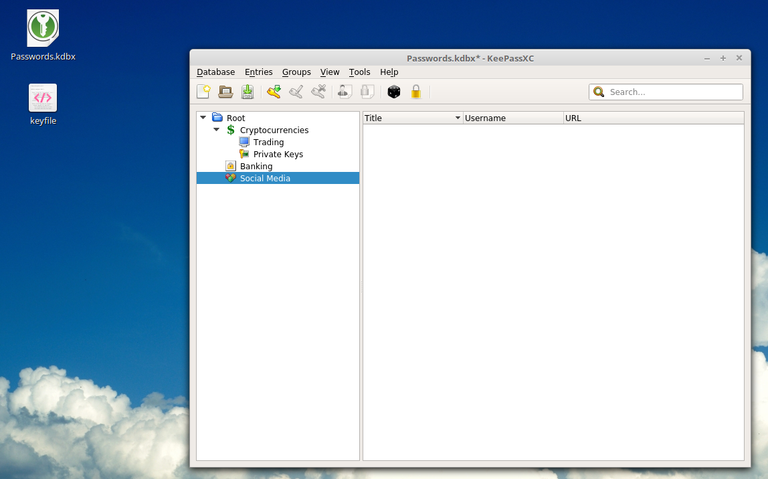
After you are done, back up the database, store it well and don’t lose nor expose your password or keyfile associated with it.
Conclusion
KeePassXC is the safest, most tested and most easy to use password manager in my opinion. With it’s new gorgeous design and features it helps you store your cryptocurrency related passwords and secrets safely.
Of course this only works if you are careful, like have a secure PC, or perhaps use KeePassXC in a non-networked computer. It’s your decision and your responsibility to store your passwords safely.
However this software makes it easy, instead of storing them on pieces of paper that get lost or browser login lists, which are insecure due to Javascript problems and things like that. No browser is sandboxed so no password stored there is safe, so storing in a safe database like this is better.
The database itself should always be backed up, again the database can be public, but the password or the keyfile should not be. So a database backed up on multiple USB sticks and on Dropbox or Google Drive, meanwhile using a secret keyfile to open it, that is stored on multiple micro-SD cards hidden well away in multiple places is a good idea.
When you use the software, you can just open the link of the website you want to login and press CTRL+V to auto-type the login/password into that page, or copy it manually, where the clipboard will be erased in 10 seconds, so you can browse after that safely, or set that timer to less in the options, if you can copy it quicker.
Sources:
- KeePassXC team, software licensed under GPL3

Omg, thank you! This is totally for me because losing passwords is the story of my life and this is going to save me all kinds of stress. Thanks!
I've been using lastpass of late, can't complain, it does everything i need
Last pass works good too.
No thanks, it's not open source....
I prefer a decentralized password holder, this ones a bit too central for me ;P
There is no such thing, all passwords centralize in your mind eventually.
I use last pass but this look a lot safer then last pass, Is there away to use this on android.
I really dont understand why people use closed sourced software where nobody knows what it does?
Windows 10 has also been caught, allegedly, that it sends out keystrokes via the internet, basically a keylogger....
So I think people should just start using Linux+Keepass
The problem with it is a lot people don't know Linux like i have said before i think, And mostly change people hate change.It seams there is not as much support for it from a lot of things . it is getting a lot more support for hardware but there is still some coins that don't have wallets.
Yes there was keylogger i am have read this before and there is a way to so called shut it off.
Well people have to learn fast or risk losing money. I have seen a lot of people here on steemit using windows, from the videos they post or they admitted it.
People are very afraid to not lose like banking password but have like not problem logging into a website where 50,000$ of their wealth is stored, from a vulnerable computer....
It boggles my mind, people really need to start using Linux, and every single hack that happens is like a learning tax, people either learn it the smart way or the hard way, hackers are relentless...
So are you telling me that the keylogger can be "shut off", hahaha you have a nice sense of humore today.
I use Zemana antilogger and Norton Power Eraser for that. The antilogger software encrypts keystrokes at low level, and Norton's power eraser is the best keylogger detection and removal software out there
Good idea dude !
Good job! I am using truecrypt for these issues. But this looks quite good as well. Use awsome encryption or simply do it like "Mam" and wright it down 😉. But keep some "emergency" backup of your passwords.
Why not use Veracrypt then? Truecrypt is obsolete and has many vulnerabilities. Veracrypt is the latest fork of is:
Thank you for the informative post. I'll have to take a look at this password manager. Would you agree that multi-factor authentication is more important than just a strong password?
It makes no sense 2FA is for like online websites where you don't control the private key but only have indirect access to it, through authentication methods.
In case of a private key, there is no authhentication, the private key is what the money is, and either it's secure or it's not.
In case of like a private key inside a keepass database, one method would be to have both password and keyfile login as well, so that both are needed for accessing the database.
But if the computer is secure, then this is really an overstretch, I'd just go for a password that is easy to memorize.
Thanks for the reply and explanation. I think I have a better understanding. New to this block chain and cryptocurrency business, so will have to continue researching.
Good information buddy.... Thanks for the share... Is it available for android and ios
Excellent post my friend, visit my profile and read mine.