We will use SSH tunneling to build such scheme:
Local machine -> Remote Server -> WWW
What we need:
- Local machine with SSH client
- Remote server with SSH daemon running (you can connect to server via ssh)
Remote server will act as a proxy server in this case.
Run this command on your local machine:
ssh -N -D 1080 username@hostname
-N - do not execute a remote command (is used for forwarding ports)
-D - specifies a port forwarding (in this example we run the SOCKS server on port 1080)
username - user on the remote server (not necessary with root privileges)
hostname - remote server (its IP address will be publicly visible)
This command will set up a SOCKS proxy server to listen on localhost (127.0.0.1) and port 1080. All requests will be transparently forwarded via remote server (hostname). The traffic will be encrypted (local machine -> remote server) and then sent from the remote server to some host (website). Your IP address will be hidden for this host.
Now we can use localhost:1080 to configure SOCKS proxy settings in web-browser or any software that supports SOCKS proxy.
Firefox example:
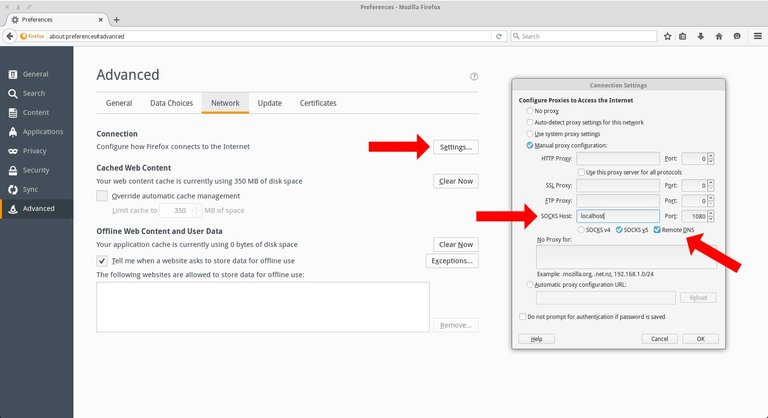
That’s all ;)
P.S. Make sure, that you configure your software (web-browser etc) to perform DNS queries via SOCKS proxy as well (it prevents so-called DNS leak).