Welcome to another review of the #REMME project. In this blog we will understand more detailed insights of the REMME project and also kind of high level of business model overview.

Let us get familiar with some of the key words that REMME project use for its business model and also understand what they really do or mean within this model. This way we will understand the easiness of REMME project and how useful it is for the added security.
REMME : It is the entity who created the distributed ecosystem for generating the various digital keys, private certificated and web auth apps so that users like us and big data companies can benefit the secured environment. More details about the #REMME entity can be found at https://remme.io
REM : It is the #digital #token or coin that is symbol of REMME distributed ecosystem. It can give us the access to various services provided by the REMME entity, for example; certificate generation/revocation, node formation, fiat conversion fees etc.
PKI : #PKI is the Public Key Identification which is a digital certificate created uniquely for each users and the systems so that they can share the information secretly for the purpose of encryption and decryption of the system or devices. It is also distributed with various elements like #CA - Certification Authority, #RA - Registration Authority, #VA - Validation Authority with different purposes each. All of them give rise to unique function which help the #PKI to validate securely.
2FA : It is "Two Factor Authentication" protocol. REMME has formed their own secured second authentication level by using this type of added security where 2FA works on the principle of Time Based One Time Password (TOTP) protocol.
SSL/TLS : Are the certificates generated as presence of PKI, along with which they can identify the unique devices and persons and thus with these certificates and REMMEauth system one can access the whole system with one click.
These all are important aspects of the #REMME business model where these are the steps, protocols, ways which are used to secure the one system.
But,
How does the whole system works here and how is REMME protecting you with its model?
REMME model is custom blockchain based protocol and hence it completely runs on the consensus algorithm thus giving it whole new possibility of using the master nodes too. Thus it is PoS based algorithm.
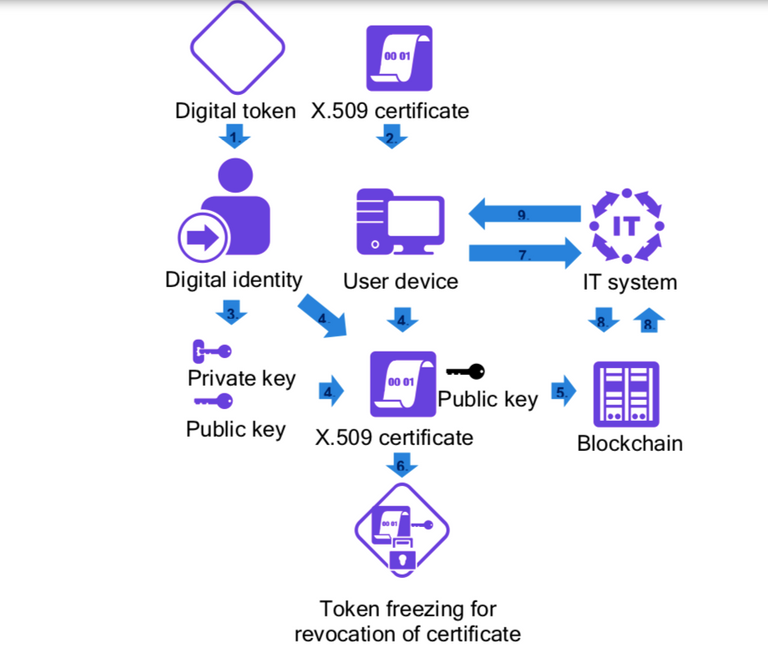
The very first requirement of using the REMME protocol is to obtain the digital token of REMME distributed ecosystem which is nothing but the REM token. This is used to obtain the identity from the REMME network.
Then a certificate is issued which includes all the info about the users which is always embedded in the blockchain itself. This is very important certificate which identifies the user from the blockchain data.
This is not enough for the identification as user needs to generate two types of keys that is private and public. This pair of key is important to have the access as it forms the unique digital identity of that user.
This generated private key is then embedded with all the personal info about the user which is later used for the purpose of identity and signing of the private keys.
As we are in the blockchain technology then it becomes more secured one when we store the private keys over there. REMME does the same by storing the whole private key in the blocks over the chain.
The certificates and private keys generated by following such complex way makes the whole key unique and thus only user with #Valid #certificate can access the systems by contacting the #IT.
How does #REMME makes everything secured after having such big data of certificates?
Off course the answer is in the blockchain tech itself!
REMME never stores our digital certificates over the centralised network and thus it is almost impossible to hack such data set from the decentralised chain like blockchain.
REMME always provide lighting fast private certification and thus your process of accessing more credential is never hampered.
They provide single sign on option which is always available with worldwide authentication.
What things I have understood so far from the #REMME project.
REMME has created a usr interface and a protocol which is almost not hackable by any other system. The use of REMME with their one click sign on option is best suited for those who are always has to keep logging in multiple times in the industries or big data companies. Many times I am signing on my crypto exchangers and many times I have to go away but as you know with thousands of tokens stored on it we cant just skip the logout process. It always becomes very tedious job to visit the website again and make the login process go on. With REMME you can just upload the certificate and logging process finishes in matter of seconds.
The process takes into consideration your devices. When first time you get on the REMME service then they allocate a SSL or TLS certificate to your that device and you can also feed your information into this private key. Depending upon that the certificate is generated successfully and store on your device successfully. REMME dont just rely on this system yet, they also add 2FA- REMME authentication process where you have to confirm your identity with 2FA login.
It means just getting hands on the certificate doesn't mean anything to you, you also need to verify the 2FA. All the information and certificates are always stored in the blocks so it means no hacker can possibly go and pick your identification. This is where REMME stands out among all the other security systems.
"Not only this, if you think that your certificates has been compromised by some means (which is impossible) but if it does happen then you an always revoke the access to that particular certificate and thus no one will be able to login with that certificate ever again."
This way #REMME has taken care of almost every bit of the security majors in their account and keeping the system almost flawless for you.
REMME is Big Potential
Thus after reading the whole processes behind this project, the complex algorithms and ways to secure the environment is exceptional quality and none of us could feel more secure than this as REMME has made us today.
With their such protocols not an individual but various big data companies, healthcare centres with personal and case sensitive data, complex infrastructure and big crypto currency exchangers can be protected.
With the current use cases and also real life partnership with mega projects I can proudly say that #REMME project is something that I have started to understand truly and its effect over the large firms can already be seen.
For additional details about REMME you can visit following #Official Links :
Website : https://remme.io/
Twitter : https://twitter.com/remme_io
Reddit : https://www.reddit.com/r/remme/
Medium : https://medium.com/remme
GitHub : https://github.com/Remmeauth
ANN Thread : https://bitcointalk.org/index.php?topic=2060387.new#new
Whitepaper : https://drive.google.com/file/d/0B1jTRGmj_3khUV9RTERnYzNvaE0/view
Reviewed by :

You have a minor grammatical mistake in the following sentence:
It should be their own instead of there own.Excellent article. I learned a lot of interesting and cognitive. I'm screwed up with you, I'll be glad to reciprocal subscription))