After reviewing multiple scams, and the theft of coins from other people, I've decided to compile a guide on how to avoid the casual scams. You can buy it now at http://bitcoin-bookstore.com.
Use 50OFF as a coupon code to get 50% off (first 500 users).
From the book:
Scams and phishing attacks are the most common way people lose funds. Over the past years, I’ve seen numerous cases of people getting hacked and losing their funds. Back in 2013, I bought some dogecoin for myself and stored it on Dogewallet, a web-wallet with lax security. I didn’t want to run a full node and it was just a few bucks for 20,000 DOGE.
A few weeks after that, the exchange was hacked and all my funds were lost. This was not the first time an exchange was hacked. People who held money at other exchanges have seen this happen in bitcoin, but I just assumed that no one would care for 20,000 DOGE. I was wrong, the whole thing was wiped clean. This taught me: never hold funds in an exchange.
Ever since then, I’ve learned a few tricks and have seen my share of hacks. In this chapter, we will review how other scams happen. While this list is not exhaustive, it is extensive.
Every day brings a new breach, but learning the basics of how people get scammed will teach you a lot about what you might face, both online and offline.
In each of these scams we have a Mark. That's you, the victim. We have an Attacker, which is either a hacker, a thief, a scammer, or whatever, and we can analyze how it works and how it happened. By understanding the risks we can understand how to mitigate the damages and learn the lesson.
Please note that these scams are not mutually exclusive. A Ponzi scheme may have the features of a pyramid. An ICO may also be a fake investment, a Pump and Dump scheme may also lead to fake ID sales. The important thing is to know the tricks, recognize the suspicious patterns, and learn how to protect yourself from them.
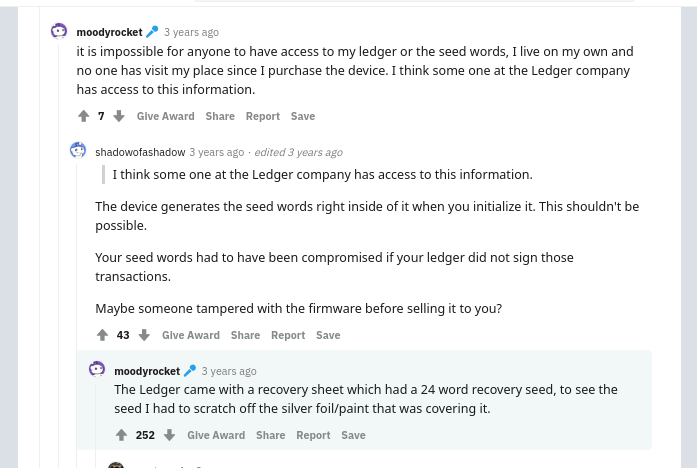
Prepackaged Seed
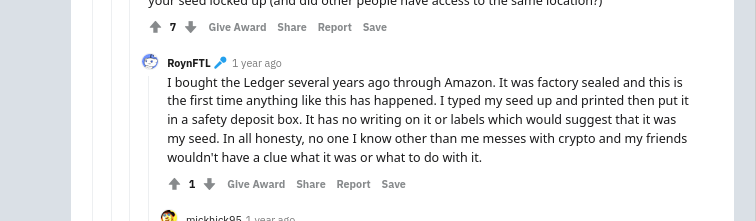
How it Works: In this scam, the mark receives a hardware wallet they bought online from a retailer. Not understanding how hardware wallets work, the mark receives a pre-generated seed and the attacker keeps a copy of the seed. To generate a sense of security, sometimes the seed is covered with security foil. As we can see in this example, the mark received his wallet with a pre-generated seed.
Sometimes, the seed given is not the actual seed at all, and only the attackers have the seed.
How it Happened: The mark wasn’t careful and wanted a discount on their hardware wallet. They paid a hefty price for that discount. When you buy a wallet, think of it as a safe deposit box: no step in the process should be compromised and never ever have a seed generated for you.
The Lesson: Don’t skimp on security. Don’t seek discounts because attackers target people like that.
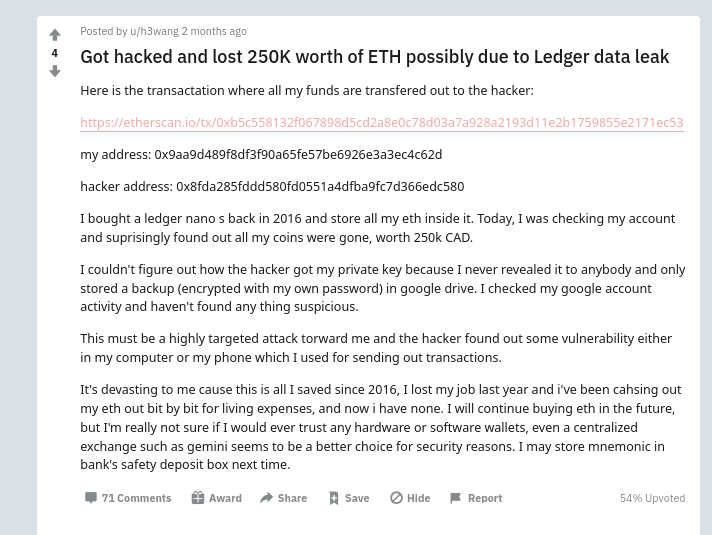
Seed Stored on a Cloud or PC
How it Works: The mark thinks that they are smarter than anyone else and that their cybersecurity is top notch. What they do is write their seed on their PC in a text file, or take a photo of it and back it on their iCloud or Google Drive, encrypted in some manner. Then, when their account is compromised for some reason, the attacker steals their funds. This mark, for example, stored an encrypted file on their Google Drive:
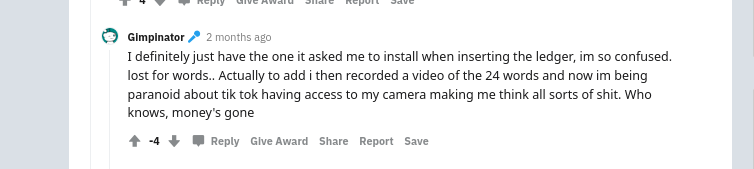
Another mark recorded a video with their seed, only to find out that they were compromised.
How it Happened: This is a case of multiple factors failing at the same time. For other stuff your hard drive encryption is good enough, but assume that when people have incentives, they will abuse and track down relevant data. In this case, an attacker waited for years with the mark’s funds. The fact that the data was stored digitally was sufficient to gain access.
The Lesson: Never store your seed on a digital medium. Always assume that all devices are compromised at all times.