Monitoring system detects hacker attacks by thermal behaviour of the processor
Treacherous heat: A new monitoring system could in future protect industrial computers from particularly sophisticated hacker attacks - the sabotage caused by overheating caused by malware. In order to detect such attacks in time, researchers are working on an intelligent sensor system for chips. This system, coupled to neural networks, detects deviations from the normal thermal pattern of the chip and triggers an alarm.
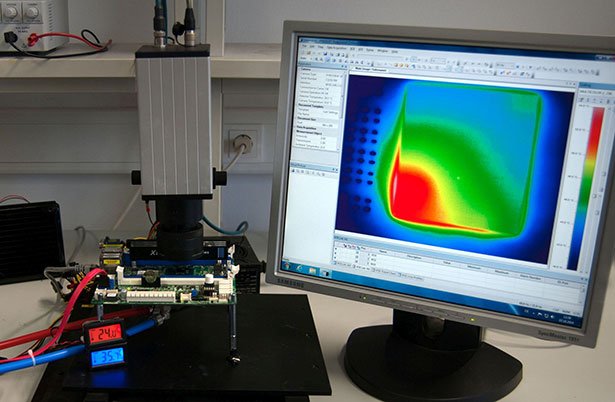
Experimental setup for monitoring a computer chip - here with infrared camera © CES / KITCyber attacks are increasing with the increasing importance of computers and networks for industry, society and the economy. Hackers use trojans, viruses or worms to infect computers with malicious software that gives them access to data or allows them to sabotage computer processes. Even processor operations are potentially vulnerable, as recently demonstrated by the Spectre and Meltdown vulnerability.
Sabotage due to overheating
Connecting the physical and application level towards grasping aging effects © CES / KITBut there is still another danger, as Jörg Henkel and his team at the Karlsruhe Institute of Technology (KIT) explain. Due to the miniaturization, processors for industrial production are now so small that the sensitive components can be damaged even at low overheating.
The shift of just a few atoms in such a transistor is sufficient to damage the functionality of the entire chip temporarily or permanently, according to the researchers.
But this opens up a completely new method for hackers to sabotage such computer systems: Incorrect control commands introduced into the chip can trigger a specific overload in the chip. This can cause an artificial aging process that destroys the chip within a few days.
Thermal fingerprint
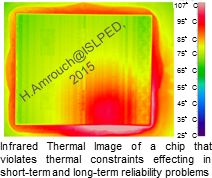
© H. AmrouchBut there is a remedy: Henkel and his colleagues have developed an intelligent self-monitoring system for computer chips that detects such hacker attacks in real time. The core of the new approach is the monitoring of the thermal patterns of the processor:
Each chip generates a specific thermal fingerprint, explains Henkel.
This consists of tiny short-term temperature fluctuations that occur during normal operation.
Calculations are performed, something is stored in memory or retrieved from the hard disk. All these operations lead to brief heating and cooling in different areas of the processor, says Henkel.
These patterns can be observed and monitored with sensitive infrared cameras or sensors directly on the chip. Because industrial computers carry out the same processes countless times in a row, their patterns are relatively constant.
Detecting attacks in real time
But it's different when a hacker hacks the computer: Then the typical temperature pattern changes - both in temporal rhythm and in relation to the maximum temperatures. The thermal monitoring system developed by the researchers enables such suspicious deviations to be detected immediately and reported in real time. This enables IT managers to shut down and check the affected computer before damage occurs.
There are already temperature sensors on the chips. They serve as overheating protection, says Henkel. We will increase the number of sensors and use them for cyber-security purposes for the first time.
In addition, the scientists want to equip chips with neural networks that can identify thermal deviations independently and thus monitor the chip in real time.
However, the threat situation is dynamic:
If the hackers know that the temperature is being monitored, they will adapt, explains Henkel's colleague Hussam Amrouch. They will write smaller or slower programs whose heating profiles are harder to detect.
The researchers therefore want to train their neural networks from the outset in such a way that they can recognize a modified threat.
Source: Karlsruhe Institute of Technology

I love the post lots to think about how to keep safe n3bul4 thank you
With love,
harj : ) xoxo
Abstract artist
(My latest artwork is "Government")
Thank you! It's indeed an interesting attempt to protect against anomalies.
Thank you! n3bul4 great to get your interpretation on my last art post called "Government" your insight would help us : )
With love,
harj : ) xoxo
Abstract artist
(My latest artwork is "Government")
I havent heard of it before. It is so useful for big companies ..
Yes indeed, this could be very useful... It's a very new attempt to encounter malware etc.
I like the post so much informative.
Thanks a lot! I am glad you like my post. Stay tuned for more to come...
Hello guys pls help me upvote and resteem i am new here pls https://steemit.com/life/@jossysylvester/after-effects-of-butt-implantation
Here we go...
Peace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.Congratulations! This post has been upvoted from the communal account, @minnowsupport, by n3bul4 from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, theprophet0, someguy123, neoxian, followbtcnews, and netuoso. The goal is to help Steemit grow by supporting Minnows. Please find us at the
If you would like to delegate to the Minnow Support Project you can do so by clicking on the following links: 50SP, 100SP, 250SP, 500SP, 1000SP, 5000SP.
Be sure to leave at least 50SP undelegated on your account.
This post has received a 0.51 % upvote from @booster thanks to: @n3bul4.