A Google security scientist has found a serious powerlessness in Blizzard diversions that could enable remote assailants to run vindictive code on gamers' PCs.
Played each month significantly a billion clients—World of Warcraft, Overwatch, Diablo III, Hearthstone and Starcraft II are mainstream web based diversions made by Blizzard Entertainment.
To play Blizzard recreations web based utilizing web programs, clients need to introduce a diversion customer application, called 'Snowstorm Update Agent,' onto their frameworks that run JSON-RPC server over HTTP convention on port 1120, and "acknowledges orders to introduce, uninstall, change settings, refresh and other support related alternatives."
Google's Project Zero group analyst Tavis Ormandy found that the Blizzard Update Agent is helpless against a hacking strategy called the "DNS Rebinding" assault that enables any site to go about as a scaffold between the outer server and your localhost.
Simply a week ago, Ormandy uncovered a comparable helplessness in a well known Transmission BitTorrent application that could enable programmers to remotely execute pernicious code on BitTorrent clients' PCs and take control of them.
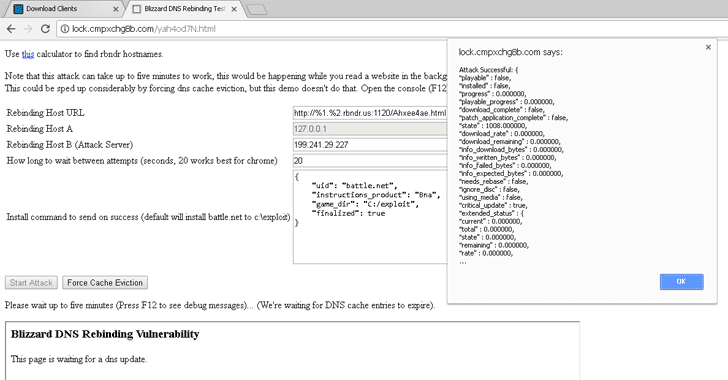
By just making a DNS section to tie any assailant controlled website page with localhost (127.0.0.1) and deceiving clients into going by it, programmers can without much of a stretch send favored summons to the Blizzard Update Agent utilizing JavaScript code.
In spite of the fact that an arbitrary site running in a web program for the most part can't make solicitations to a hostname other than its own, the nearby Blizzard updater benefit does not approve what hostname the customer was asking for and reacts to such demands.
Snow squall DNS Rebinding Attack — Proof of Concept Exploit
Ormandy has likewise distributed a proof-of-idea misuse that executes DNS rebinding assault against Blizzard customers and could be adjusted to permit abuse utilizing system drives, or setting goal to "downloads" and influencing the program to introduce malignant DLLs, information documents, and so on.
Ormandy capably revealed Blizzard of the issue in December to get it fixed before programmers could exploit it to target a huge number of gamers.
Notwithstanding, after at first correspondence, Blizzard improperly quit reacting to Ormandy's messages and noiselessly connected halfway moderation in the customer rendition 5996.
"Snowstorm was answering to messages however quit conveying on December 22nd. Snowstorm is never again answering to any enquiries, and it would appear that in adaptation 5996 the Agent now has been noiselessly fixed with an odd arrangement," Ormandy says.
"Their answer gives off an impression of being to question the customer summon line, get the 32-bit FNV-1a string hash of the exename and after that check if it's in a boycott. I proposed they whitelist Hostnames, however obviously, that arrangement was excessively exquisite and straightforward. I'm not satisfied that Blizzard pushed this fix without telling me, or counseled me on this."
After the Ormandy's report opened up to the world, Blizzard reached and educated him that a more powerful Host header whitelist fix to address the issue altogether is as of now being created for arrangement.
Ormandy is additionally checking other defining moments merchants with a client base of more than 100 Million to check whether the issue can be imitated.