After attending the 2017 Rainbow Gathering in Oregon for 2 days and discovering without any doubt that the entire backbone of the event was run by undercover police dressed up like hippies, distributing fake 'acid' and baiting people into crimes with underage persons, I returned to my vehicle and travelled back to the city. I was concerned that at some point in time they might have accessed my Honda CRV in a no knock raid and placed hardware rootkits on my computers.
So I pulled into McDonald's, rebooted my computer, started Wireshark and turned capture on my wifi interface, then joined McDonald's wifi.
Before I started a single program there was so much traffic I had no chance to investigate even a small percentage of the addresses or gauge how much actual traffic was passing even though it was clearly a lot.
I let the capture go for about a minute before I was too freaked out to let it go any more. I shut the wifi off and stopped the capture, saved the .pcap file.
The .pcap file was 1.8 Megabyte of data. I was running OS X El Cap on a 2011 Macbook Pro at the time. I reinstalled my OS after this experience.
That rate of data could download a a feature length film in 12 minutes. Every text and image file on my desktop in less time. Enough to transmit real time audio or low res video.
This was/is a lot of data for a computer to be transmitting on boot without any action or notification of the user. At the least it is worth asking some questions, but I think it's pretty obvious this is a security event. Analysis of the .pcap shows 179 distinct ip addresses contacted in this minute and an astounding 6044(!) obscure tcp ports being used. I will list an exact copy of the ip addresses below but due to the extreme length of the port list I'll just show the screenshot.
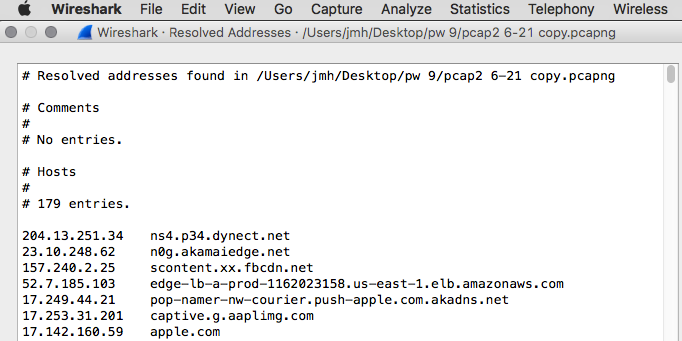
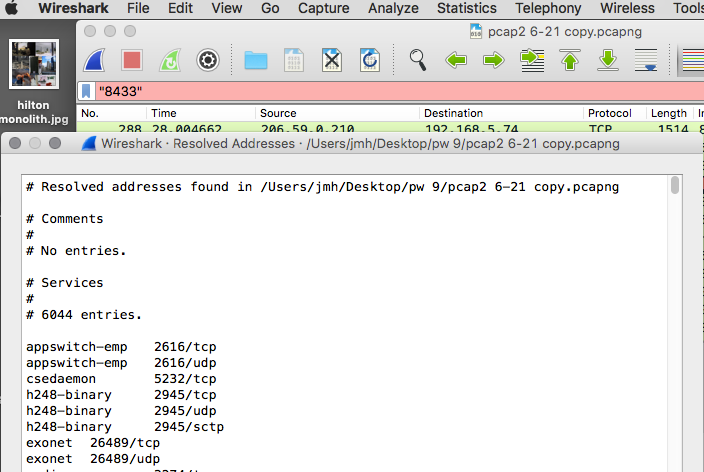
Resolved addresses found in /Users/jmh/Desktop/pw 9/pcap2 6-21 copy.pcapng
Hosts
179 entries.
I sorted them into some basic categories. In this IP list, my computer was the ip address 192.168.5.74 on the Mcdonald's LAN, the rest are foreign addresses my computer was talking with in the first minute after boot with no action taken by myself to start any processes. I have sorted them into basic groups for analysis(this took some time....)
Me
192.168.5.74 8433dsl-m144-2.local
fe80::fa1e:dfff:feed:903d 8433dsl-m144-2.local
McD (I am on their network so I am using their name servers(dns), so it makes some sense my computer will connect to these addresses, but every site i visit will be logged and tagged of course))
192.243.232.9 mcdonaldscorporation.tt.omtrdc.net
192.243.232.8 mcdonaldscorporation.tt.omtrdc.net
66.235.141.161 mcdonaldscorporation.sc.omtrdc.net
192.243.232.2 mcdonaldscorporation.tt.omtrdc.net
66.235.153.29 mcdonaldscorporation.sc.omtrdc.net
63.140.35.173 mcdonaldscorporation.sc.omtrdc.net
192.243.232.7 mcdonaldscorporation.tt.omtrdc.net
66.235.141.160 mcdonaldscorporation.sc.omtrdc.net
66.235.153.28 mcdonaldscorporation.sc.omtrdc.net
63.140.35.172 mcdonaldscorporation.sc.omtrdc.net
66.235.157.5 ns12.omtrdc.net
66.235.157.4 ns11.omtrdc.net
66.235.157.7 ns2.omtrdc.net
66.235.157.6 ns1.omtrdc.net
APPLE (just because i run the os doesn't mean i want to phone home every .3 seconds geez apple, lots of dns even though im using the McD dns, akadns.net is suspicious, we will investigate, my OS is not configured to do auto updates either so the phoning home ticks me off. At least they operate out of an obvious 17. ip block that is consistent.)
17.142.160.59 apple.com
17.178.96.59 apple.com
17.172.224.47 apple.com
17.249.44.97 pop-namer-nw-courier.push-apple.com.akadns.net
17.249.44.96 pop-namer-nw-courier.push-apple.com.akadns.net
17.249.44.101 pop-namer-nw-courier.push-apple.com.akadns.net
17.249.44.31 pop-namer-nw-courier.push-apple.com.akadns.net
17.249.44.11 pop-namer-nw-courier.push-apple.com.akadns.net
17.249.44.21 pop-namer-nw-courier.push-apple.com.akadns.net
17.249.44.75 pop-namer-nw-courier.push-apple.com.akadns.net
17.249.44.91 pop-namer-nw-courier.push-apple.com.akadns.net
17.188.166.16 1.courier-sandbox-push-apple.com.akadns.net
17.188.138.71 6.courier-sandbox-push-apple.com.akadns.net
17.253.201.8 a.gslb.aaplimg.com
17.253.31.203 captive.g.aaplimg.com
17.253.31.201 captive.g.aaplimg.com
17.254.0.59 nserver2.apple.com
17.112.144.59 nserver4.apple.com
17.151.0.152 adns2.apple.com
17.151.0.151 adns1.apple.com
17.249.57.246 api-glb.smoot.apple.com
17.253.217.53 ns1.smoot.apple.com
17.171.63.30 nserver5.apple.com
17.112.144.50 nserver3.apple.com
17.253.206.8 b.gslb.aaplimg.com
17.171.63.40 nserver6.apple.com
17.254.0.50 nserver.apple.com
17.253.217.54 ns2.smoot.apple.com
AKAMAI(a truly staggering number of connections to distinct ip's, we will investigate in the next section, but at least this is a known company that exists. With ipv6. Some .orgs in there that are odd, mostly edge, dns. Do I know akadns is really akamai? Nope. And these IP blocks are all over the place. Therefore when I pulled into mcdonald's and rebooted my computer, there was apparently some sort of global networking event, as in I moved electrons on all 5 continents and under every ocean during this single minute of non-activity on the internet.)
23.59.189.97 a1414.g4.akamai.net
165.254.26.79 n1g1.akamai.net
23.59.189.90 a1414.g4.akamai.net
207.109.73.45 n0g1.akamai.net
23.3.105.157 n5g4.akamai.net
23.3.105.151 n4g1.akamai.net
23.3.105.156 n4g4.akamai.net
23.3.105.150 n6g1.akamai.net
23.59.189.83 a1441.g4.akamai.net
165.254.26.71 n1g4.akamai.net
207.109.73.54 n0g4.akamai.net
23.3.105.143 n7g4.akamai.net
23.3.105.165 n5g1.akamai.net
23.3.105.137 a1165.g1.akamai.net
23.3.105.159 n3g4.akamai.net
23.3.105.161 a1165.g1.akamai.net
23.3.105.142 n6g4.akamai.net
23.10.248.62 n0g.akamaiedge.net
23.49.13.185 e5799.g.akamaiedge.net
96.17.177.61 n1g.akamaiedge.net
88.221.81.194 n0g.akamaiedge.net
96.17.163.120 n6b.akamaiedge.net
104.90.25.200 e8385.g.akamaiedge.net
165.254.1.206 n5a.akamaiedge.net
96.17.177.55 n4b.akamaiedge.net
184.85.250.34 n3b.akamaiedge.net
96.17.177.60 n0b.akamaiedge.net
88.221.81.193 n1a.akamaiedge.net
104.125.181.155 e6987.a.akamaiedge.net
184.51.217.22 e8051.b.akamaiedge.net
165.254.1.210 n4dsce9.akamaiedge.net
96.17.177.59 n4g.akamaiedge.net
96.17.163.118 n7b.akamaiedge.net
165.254.1.204 n2a.akamaiedge.net
96.17.8.36 n2dsce9.akamaiedge.net
72.246.55.133 n2g.akamaiedge.net
165.254.1.209 n6a.akamaiedge.net
96.17.163.117 n5b.akamaiedge.net
96.17.8.30 n0a.akamaiedge.net
96.17.163.122 n4g.akamaiedge.net
165.254.1.208 n7a.akamaiedge.net
184.27.179.236 n1dsce9.akamaiedge.net
165.254.1.197 n5dsce9.akamaiedge.net
96.17.163.116 n1b.akamaiedge.net
96.17.8.29 n2g.akamaiedge.net
104.90.18.53 e10231.g.akamaiedge.net
104.126.37.85 e6858.dsce9.akamaiedge.net
104.90.26.221 e10723.g.akamaiedge.net
184.27.179.246 n3a.akamaiedge.net
96.17.177.62 n2g.akamaiedge.net
96.17.163.121 n7g.akamaiedge.net
165.254.1.207 n4a.akamaiedge.net
88.221.81.195 n3dsce9.akamaiedge.net
2600:1480:e800::c0 a0b.akamaiedge.net
193.108.88.128 a1-128.akadns.net
184.85.248.128 a9-128.akadns.net
23.61.199.131 a7-131.akadns.net
84.53.139.129 a11-129.akadns.net
95.100.173.129 a28-129.akadns.org
95.101.36.128 a18-128.akadns.org
95.100.168.130 a5-130.akadns.org
2.22.230.130 a13-130.akadns.org
96.7.49.129 a3-129.akadns.net
Facebooc(not running app or even browser, never used instsagram, ipv6 connection also. I had been using facebook at the time on firefox.)
157.240.2.25 scontent.xx.fbcdn.net
157.240.11.22 scontent.xx.fbcdn.net
69.171.239.11 a.ns.xx.fbcdn.net
157.240.18.19 scontent.xx.fbcdn.net
31.13.69.228 star-mini.c10r.facebook.com
157.240.18.63 instagram.c10r.facebook.com
69.171.255.11 b.ns.xx.fbcdn.net
2a03:2880:fffe:b:face:b00c::99 a.ns.xx.fbcdn.net
2a03:2880:ffff:b:face:b00c::99 b.ns.xx.fbcdn.net
AMAZON(no apps, no browser, 3 ipv6 connections, at least I have used amazon)
52.7.185.103 edge-lb-a-prod-1162023158.us-east-1.elb.amazonaws.com
205.251.196.95 ns-1119.awsdns-11.org
52.54.164.164 edge-lb-a-prod-1162023158.us-east-1.elb.amazonaws.com
205.251.199.1 ns-1793.awsdns-32.co.uk
205.251.192.235 ns-235.awsdns-29.com
2600:9000:5304:5f00::1 ns-1119.awsdns-11.org
2600:9000:5307:100::1 ns-1793.awsdns-32.co.uk
2600:9000:5300:eb00::1 ns-235.awsdns-29.com
GOOGLE(chrome is installed but otherwise no google apps, but this is a huge number of addresses)
108.177.8.95 googleapis.l.google.com
108.177.103.95 googleapis.l.google.com
108.177.10.95 googleapis.l.google.com
173.194.223.136 youtube-ui.l.google.com
173.194.78.95 googleapis.l.google.com
74.125.30.95 googleapis.l.google.com
216.239.32.10 ns1.google.com
173.194.223.91 youtube-ui.l.google.com
173.194.223.102 www-google-analytics.l.google.com
209.85.235.95 googleapis.l.google.com
216.239.34.10 ns2.google.com
64.233.169.95 googleapis.l.google.com
173.194.223.113 www-google-analytics.l.google.com
216.239.36.10 ns3.google.com
216.239.38.10 ns4.google.com
173.194.200.95 googleapis.l.google.com
173.194.223.101 www-google-analytics.l.google.com
108.177.9.95 googleapis.l.google.com
64.233.160.95 googleapis.l.google.com
108.177.104.95 googleapis.l.google.com
173.194.223.190 youtube-ui.l.google.com
173.194.223.139 www-google-analytics.l.google.com
173.194.223.100 www-google-analytics.l.google.com
64.233.168.95 googleapis.l.google.com
173.194.223.138 www-google-analytics.l.google.com
74.125.198.95 googleapis.l.google.com
173.194.223.93 youtube-ui.l.google.com
Spotify(which I have never, ever used)
104.154.127.47 weblb-wg.dual-gslb.spotify.com
(how the hell did spotify install on my system if I don't use it? )
twitter(I use but how does it install a phone home functionality?)
199.96.57.6 platform-eb.twitter.com
wayport.net (probably mcdonald's)
216.12.255.2 auth1.wayport.net
216.12.255.1 auth0.wayport.net
216.12.255.3 auth2.wayport.net
206.59.0.210 = 206.59.0.210 nmd.mcd26924.sea.wayport.net
MYSTERY SECTION (truly no idea what these are, we are going to research them in the next section)
204.13.251.34 ns4.p34.dynect.net
208.78.71.23 ns3.p23.dynect.net
204.13.250.23 ns2.p23.dynect.net
204.13.250.34 ns2.p34.dynect.net
208.78.70.23 ns1.p23.dynect.net
204.13.251.23 ns4.p23.dynect.net
2001:500:94:1::34 ns3.p34.dynect.net
2001:500:90:1::23 ns1.p23.dynect.net
2001:500:94:1::23 ns3.p23.dynect.net
2001:500:90:1::34 ns1.p34.dynect.netdynect (mystery dns) (login to change the internet! https://portal.dynect.net/login/)
(safety rating unknown:https://www.mywot.com/scorecard/dynect.net, divergent reports from comments)
208.78.71.34 r01-01.ns.twtrdns.net
208.78.70.34 d01-01.ns.twtrdns.netTWTR (mystery dns)(aha! mark monitor, brand protection https://www.whois.com/whois/twtrdns.net, also connected to dynect.net!)
HOWEVER dynECT is also this company: https://en.wikipedia.org/wiki/Dyn_ and GUESS WHAT they are directly connected to: The Oct 2016 internet outage coinciding with the Assange event in london! Very interesting. They say it was DDoS but if this is connected to deep state surveillance networks, all they would have had to do is take it down themselves to simulate an outage that would cover their actions.)
198.51.44.5 dns1.p05.nsone.net
198.51.45.69 dns4.p05.nsone.net
198.51.44.69 dns3.p05.nsone.net
198.51.45.5 dns2.p05.nsone.netNSONE (mystery dns) (https://ns1.com/ whatever this is....)
104.156.80.32 ns2.fastly.net
104.156.84.32 ns4.fastly.net
23.235.32.32 ns1.fastly.net
23.235.36.32 ns3.fastly.net
151.101.48.175 cdn-fastly.krxd.net.c.global-ssl.fastly.netfastly(banned in china for ties to us military but wikipedia is now taken down just the homepage: https://www.fastly.com/)
Incoming packet size total however turns out to be 1.6Mb and outgoing only .2Mb.
Let's look for the big outgoing addresses
.04 Mb to some seattle McDonald's waypoint that has some sort of auth mechanism attached, odd
206.59.0.210 = 206.59.0.210 nmd.mcd26924.sea.wayport.net
This mystery address looks like a Seattle McDonald's asset. But also here large numbers of Resets, Duplicates. Most packets sent here are acknowledgements, some say 'windows update' and some are GET requests for graphics, so this is probably some incompetent authorization implementation for mcdonad's wifi. Needing 42kb for a single minute of authorization processes is pretty horrible as far as efficiency goes. Some of the failed transmissions and resets could be due to wifi dropouts or unavailability but in a single minute, this is a staggering number of packets to send as part of overhead. This address stood out first because of the large number of error packets, which stands out graphically in wireshark.
Looking for the rest of the .16Mb of data my computer sent out in this one minute all over the world and drilling a little bit into what kind of traffic is being sent.
23.3.105.* is a bunch of akamai servers that get 50kb or .05Mb of the outgoing traffic. So between McD's waypoint and Akamai's mystery server farm we have accounted for at least half of my outgoing traffic. And in general there are a lot of other akamai matches, it would be difficult to make a filter that could count all the traffic here.
A small number of packets with an encrypted TLS handshake went to Twitter for some reason:
199.96.57.6 = 199.96.57.6 platform-eb.twitter.com
(*twitter)
For some reason spotify also makes an encrypted but small connection
(* spotify's encrypted handshake)
I see other packets outgoing to apple but many of the other more obscure addresses only send packets in, which is not what I would have expected to find.
So if Akamai is the number one phone out address, what are they all about? Well it turns out to be worst case scenario.
Totally connected to US government, CEO on presidential advisory committee. Other founder former Israeli soldier that allegedly died on 9-11.
https://en.wikipedia.org/wiki/F._Thomson_Leighton
https://en.wikipedia.org/wiki/Daniel_Lewin
So basically, if you don't trust the American and Israeli cybersecurity, then this is the devil. And since I don't trust them, then this is worst case scenario.
https://en.wikipedia.org/wiki/Akamai_Technologies#Controversies
Also owned partially by Blackrock, which is the worst. Literally the devil/illuminati. Also controversies regarding forwarding facebork data to the NSA etc.
So akamai is basically surveillance of one kind or another for global bad guys. And they are really interested in my computer.
So as Ali G. says, just like in a video game if you encounter the bad guys, you must be going in the right direction...
As for the scope of this article, I have,
a. demonstrated that I am being surveilled
b. demonstrated how to investigate the connections your computer is making behind your back
c. demonstrated that you don't have to be browsing or using any programs on your computer for numerous companies to be able to make encrypted connections to your system
d. given you a list of ip addresses that you can use to identify enemy surveillance infrastructure
One extra bonus tip: on OS X, a process that seems to be associated with surveillance events like this is the VTX Decoder:
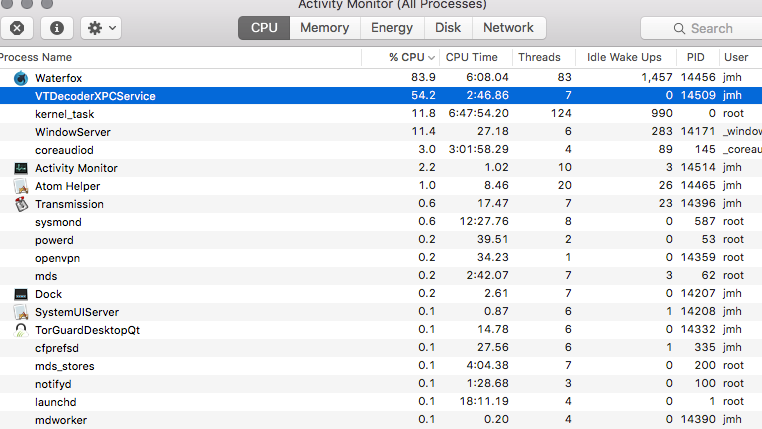
So if you see this running in activity monitor, just kill it. I haven't noticed any performance issues after killing it, but after every reboot I have to deactivate it at some point when it spikes the cpu for no reason. Like usual apple forums on this are dead ends. (fwiw Apple discussions are total shit and whoever is responsible for those whitewashes the whole OS)
I find the connections to akamai and dynECT as well as Blackrock to be very disturbing. This connects my computer directly to the entities that are highly associated with two deep state events about whose official story I am in complete doubt: 9/11 and Wikileak's London events of Oct. 2016.
Remaining question: Why so many more packets incoming than outgoing? What point can there possibly be to hitting my computer with 1.6Mb of traffic inside of a minute if no information is received? Were they installing something? Were they attacking me somehow? I will keep the file on hand in a safe place of course and as time goes one and I learn more, and have time to do so, I will dig deeper into the packets themselves.
Any further insight or if you see an error in my analysis, please comment.
I have committed to doing one more Privacy Workshop on Steemit, but if nothing changes I am going to have to abandon this platform due to the low quality/sketchiness of the user base and the invalidity of the overall value algorithm. It's way too easy for disinformation to spread here and there are huge gangs of disinformation agents already camping/blocking/sliding all possible topics. This makes me doubt the overall validity and resiliency of the Steem blockchain, if it is so easily co-opted by tyrannical forces and if the things that I do fail to attract a single reputable other person(or if people are already too terrified of retribution to be associated with the truth...), then this platform will not be long lived.
I hope, but wonder if it's possible, that in some way what I have contributed here will have a long life and eventually be seen by more people. It's not for me to say, I am just writing what the smartest stuff I can say about what's I find most important. And I do that even if no one reads and even if no one pays.
I still haven't gotten a single BTC donation, really disappointed with the community. Also 300 followers but getting only a handful of upvotes from mostly fake or troll accounts. Look at my steemd, 99% of interactions I've had over the last few months have been with .1/14.99 delegated new accounts who don't have shit to say, and other people who comment are only here once and have next to nothing to say, and really not even a single person has demonstrated they have even partially read one of my posts.
If there were one word I would use to describe steemit, it would be "Braindead."
Prove me wrong or you get one maybe two more posts and that's it.
BTC: 1G5BEFLbLMBfXPQSzTPuRLusJuWeuQ33gZ
BTS: actual-mindhawk
Let the good vibes get a lot stronger, (but it's probably safer at this point to start building your underground base and isolating yourself from the coming madness than to have any expectation of a safe and/or sane future on this planet )
p.s. i was censored at reddit for daring to suggest that the r/conspiracy mods work at military bases or fbi/mossad hq, so I think we can safely say that reddit has been fully co-opted by spies/police. The % of decent information I get there has been on the slide for a long time, now I have to sift through so much crap to get any actual information it is not much use. I have never in my life had has much difficulty either getting information or finding anyone real to interact with on the internet, and I do not think this is an accident. 99% is disinfo even though the truth is actually in plain sight, a strange arrangement indeed and makes me wonder how long this can go on for before something really bad happens and a chinese system takes over the entire world...
I am one of those who have read your posts and follow but don't comment or don't always upvote. My upvotes are almost worthless.
Its all been a learning experience and not sure what to do with all the info you have shared.
I find it interesting you use bitcoin as it not exactly private. Maybe that is why no one has donated any?
I have also wondered that, I'm working on a solution to that dilemma regarding an actually private donation coin.
hmm 'not sure what to do with', well knowledge has a way of altering your future passively. i can't say i wake up every morning and say 'im going to act on these facts.'
your mind actually tells you what is most important to you, it's what you think about all the time. i think about technology and how it's being implemented in such a way that it makes for overall less freedom not more. and that it appears that secret societies, banks, sexual predators and racists are taking over the world.
I wish i was 1 / 1000 as smart with this kind of stuff as you are. I get what you are saying in total but you lost me on the finer details way back about a 1/4 of the way in.
The point of the workshop aspect is that you can really ask questions about what you don't understand.
I'm curious how you would summarize what I'm saying in your own words?
Update:
The Port count on wireshark is likely buggy as it stays the same regardless of which pcap you are looking at. So disregard the 6044 ports thing for now.
TORGUARD IS LIKELY COMPRIMISED
There has been NO response from the gangstalking website I contacted as part of Privacy Workshop 8:
https://steemit.com/privacy/@mindhawk/privacy-workshop-8-the-epidemic-of-homicidal-maniacs-hearing-voices-and-police-state-stalking
I suspect this is also a honeypot in a nest of honeypots trying to look like the honeypot that outs all the other honeypots but it still just a honeypot.
This alone should be a huge scandal, the 'biggerthansnowden' site and ones like it, that they exist, means there is an active attempt to intervene when people being experimented on or manipulated attempt to reach out for help or to journalists.
This, is wierd, very wierd and exactly the type of thing that made me want to leave the USA.
And makes it clear the constitution is not in effect, at all when not for show.
Only came across you a few months ago and have read all your posts. If you do move on could you please advise where so i can still read your work.
problems are simple to solve
snitch + vpn + tor. call it a day
or tails on a usb stick