
Building and running a cybersecurity organization is a daunting task and most aren’t doing very well. The brutal reality is that the industry is struggling. Even as gains are made in the professional community, losses are skyrocketing in the face of security spending that is increasing to astronomical levels. Some estimates place losses to cybercrime alone at $6 trillion by 2021, doubling from $3 trillion in 2015, while security spending will top $1 trillion with expected double digit annual growth. These losses exceed the global illegal drug market and the security investment burden increases at an unsustainable rate. Even with massive investments over the years, the world continues to hemorrhage losses due to cyber-attacks. These damages are derived from individual organizations that have failed to erect and maintain viable defenses.
Companies in regulated industries and larger businesses will typically invest in an internal team to actively manage the cyber risks with a Chief Information Security Officer (CISO) at the helm. The current incarnation of the CISO position has not really been in widespread use for very long and the role has radically changed over the years. Where they report within the organization, what background and skills they possess, their overall responsibilities, and the desired experience for which they are hired varies wildly from one CISO to the next. The traditional CISO role focuses on protecting company assets, including preserving reputation, preventing downtime, securing data and financial assets, and ensuring regulatory compliance. But some companies are also using the CISO role as an external marketing ambassador to fuel visibility and drum up customers. So, in today’s world it is a mixed bag. Consequently, security teams are managed very differently and there is a major performance gap that needs to be addressed.
Illusions of a Universal Plan

Consistency of security teams between companies is rare. There is no gold standard or template that is used. This is partly by necessity as every company is different, but mostly because the security industry is still in a state of flux: learning and adapting. Therefore, collective continuous improvement is spotty and difficult to transplant. Each organization is going at it individually. Anyone who says different either has not been around very long or is trying to sell you something.
Even within an established cybersecurity team, stability is atypical. I tell new graduates entering into the field to expect their roles to change within 18 months of being hired. The functions, responsibilities, priorities, tasks, and tools will change regardless of where they land. Veterans too often experience the same state of ambiguity. It can feel like chaos in the front lines, while senior staff are faced with similar challenges as their superiors’ expectations also shift with the wind. Frustration is the norm. Change is constant in cybersecurity and with it, brings challenges for teams to establish long-term focus, and delivery of stability and confidence.
Not for the Faint-Hearted

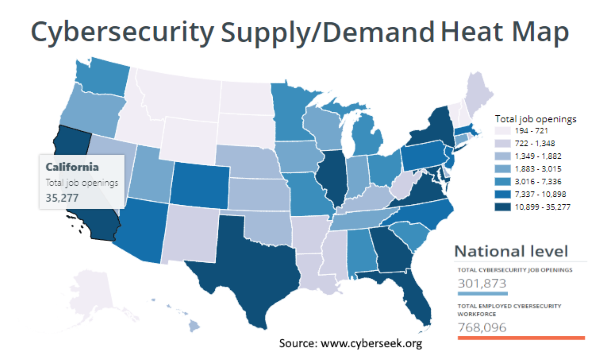
CISO’s are faced with cyber threats that are highly motivated and continue to increase in number, sophistication, and creativity. In many cases the attackers possess the advantage in skills and actively collaborate to maximize speed and aptitude. The pool of highly effective security personnel necessary to build a team, is small, expensive, and in great demand. There are more jobs than people. Nationwide, about 28% of all cybersecurity jobs are still open. Recent predictions show a global deficit of 2 million unfilled cybersecurity positions by 2019 and 3.5 million by 2021.
The battlefield, being the technology (data, software, hardware, networks, and information technology services) used by any enterprise, is constantly changing and must be securely configured and maintained in order to have any semblance of defense from attack. Attackers maintain the initiative, determining when, where, and how exploits will unfold. They own the tempo and have the element of surprise across a large target surface. Then there are the misguided actions of employees which can undermine security at the click of a mouse. Finally, senior and middle management tends not to value security investment until something horrible happens, characterized by the axiom “security is not relevant, until it fails.” Managing cybersecurity is nothing short of a madhouse.
It is not surprising that CISO’s don’t typically have a long tenure, averaging a scant 24 to 48 months. When something goes wrong, they are an easy scapegoat. The history of the position has been one fraught with responsibility without oversight and accountability without resources. In essence, the CISO’s neck is on the chopping block for many areas they don’t have visibility or control over. Purse strings for resource availability can allow for feast or famine, depending upon the fleeting fears or obliviousness of the Board and C-level executives. Even with the greatest view of their domain, the CISO sees a massive landscape that is difficult to comprehend, appearing like shifting sand dunes: seemingly impossible to oversee and control.
What Boards and C-suites have been slow to grasp over the years is the CISO is only one cog in the overall security machine. Everyone has a roll and the CISO needs active help and support from the entire organization. The root of the CISO function is operational oversight for the digital security teams. “Operational” is the key term. They must establish and maintain control over the risks of loss due to cyber threats. Not just today, but every day.
Scars from the Trenches

Herein lies the challenge. In order to have a sustainable cybersecurity risk management capability, i.e. consistently effective over time, the security team must be forged and run in a way that it is agile enough to adapt to changes in cyber threats, protect the legacy and ever-evolving technology employed by the organization and partners, comply with emerging digital regulations, and most importantly, meet the ambiguous and shifting expectations of management and shareholders. Daunting.
Some CISO’s are lost, blind, in denial, or are blundering the best they can every day, knowing they are probably not in a role well suited to their talents or longevity. However, many of the CISO’s I have met are capable managers, who understand technology, and are current on the latest threats and attacks. However, this is not enough. Even the best-of-the-best know they don’t have everything figured out. They strive to elevate their team and organization to ever higher tiers of effectiveness and value for their stakeholders. Often, they are the ones who, behind closed doors, who want to know how others are succeeding or failing, pitfalls to avoid, where criminals are shifting, and practical insights of the long-term changing threat landscape. These are the conversations I relish.
One of the dirtiest secrets in security is that the community is terrible at sharing and collaborating, and stuck in a tactical mindset of putting out fires. But by knowing the best practices of others, a CISO can compare what they are doing and possibly apply those learning to improve their team and begin to think ahead. Ultimately, the more we share, partner, and collaborate the stronger and more capable the cybersecurity community becomes.
Challenges that Everyone Suffers

- Communications with the C-Suite and Board that garner clear risk expectations and necessary support to achieve realistic capabilities
- Defining clear and persistent long-term meaningful goals that can be pursued and achieved by the security team
- Instituting truly valuable success measures and metrics which allow for clear data-driven decisions to be made for continuous improvement and determining when risk levels have reached desired goals
- Designing a team to deliver capabilities which remain cost effective in the face of ever increasing threats, attacks, and regulations
- Gaining collaborative support from other departments and divisions, including winning the minds of employees
- Understanding how future risks will evolve so the organization can be proactive instead of solely reactive
These are no simple feats and the struggle is real. As cybersecurity becomes more of a firestorm in the media, important to stockholders and investors, and on the minds of citizens and customers, effective risk management rises in importance. Boards and C-suite executives can no longer ignore the necessity of good security. Recognition of the need does not translate to understanding what it means, the costs, and potential impacts of productivity and customer usability. Cyber-risk is a new language, still being shaped. Nobody has all the answers and very few even have good questions.
So, they hire a CISO with the expectation this person will have all the answers and not need good questions or clear direction. Ironically, the opposite is true. The CISO and superiors should work with the Board and C-Suite to clearly define the expectations, tempered by the willingness to invest, so the CISO may then develop and execute necessary plans to meet the requirements. This usually entails the willing participation of everyone in the company. All is easier said than done and a certain amount of vagueness will still exist.
Everyone Has a Role

At the uppermost echelon, the Board of Directors and C-suite set the high-level vision and mission for security. They establish, normally through qualitative business-oriented descriptions, what they desire and find unacceptable. The CISO works to define the scope, develop the mission, budget, policies, and necessary capabilities which drives the focus and actions of the security team. The CISO is then responsible for managing the team day-to-day and held accountable for its functions and value.
Challenges quickly arise due to the vast ambiguity that normally permeates these roles and efforts. In most cases, CISO’s rush into a firefight on day one and are in a constant state of responding to incidents, bolting in security solutions, forcing new policies on resistant employees, mandating regulatory compliance measures, and trying to minimize losses. All the while, wondering what they are missing and when the next unexpected major event will erupt like a volcano beneath their feet.
Thinking strategically is difficult when you are constantly maneuvering in a tactical battlefield. The big picture is lost. Efforts are distilled down to preventing the next surprise attack. Sadly, this is a losing path, fraught with ever rising costs, incidents which do not cease, and wasted efforts that do no materially reduce the risk of loss. The result is increasing frustration by the business leaders, resulting in an erosion of confidence in the security apparatus and its management.
Function of the Cybersecurity Strategist

The first challenge for any successful security organization is to understand what they are trying to accomplish. Flawed or vague expectations leads to wasted resources, missed opportunities, perception of incompetence and poor performance, and usually failure down-the-road. Most Boards and C-suite personnel are not security or risk savvy. Even the lexicon can seem to be a foreign language, creating difficult communication barriers. Unrealistic expectations are common. Those who are leading a company down the road to financial success, more often than not, simply want NO security events, impacts, or related losses. It sounds great, but is naive. To the uninitiated, security is binary: either you are secure and experience no loss or you are not secure. This simply is not the case and not realistic in the cybersecurity world. Security is about managing the risk of loss. There are tradeoffs, usually measured in security spends, employee productivity, and customer usability. Generally speaking, the more an organization wants to reduce the risk of losses due to cyberattack, the higher the other costs will be. These can grow to be quite sizeable very quickly and it is questionable if ever it is possible to make an organization impervious to attack. Even if it were, the costs would likely be astronomical and represent a completely unacceptable impairment to the business.
This is where a cybersecurity strategist can play a crucial role in gently guiding and facilitating discussions around risk. It is something that takes practice and experience. Much of challenge is interpreting what the Board and C-suite are asking, which is typically in qualitative terms and translating those to more quantitative descriptions that the leaders can then refine. The outcome is a long-term set of expectations that can clearly be pursued by the CISO with regular reports back to the leadership team in a format that is already understood.
Such a framework is hugely helpful for the CISO. Knowing what areas are important, targets to hit, and how to consistently measure progress removes a number of significant hurdles and burdens. It also provides a platform to justify spending as it relates to the expectations. Removing unfamiliar language also opens up the possibility for a stronger relationship between CISO and everyone above. Bridging the communications gap is a major success for every cybersecurity organization, yet few have done it successfully.
The next challenge is to actually architect a security organization that will meet the expectations of the C-suite and Board now and well into the future. This must be done in a way that is financially frugal, dynamic to the shifts in cyber threats, and in balance with the potential impacts to business priorities. Executives have grown tired of double digit security budget increase requests every year. It has become a sign of a CISO’s inability to plan for the future. A well-crafted security team is one that can adapt, by design, to absorb new challenges without significant budgetary demands. This is where strategic perspectives returns significant dividends.
Strategic Cybersecurity Deliverables

The 7 deliverables an experienced cybersecurity strategist should provide:
- Define the cybersecurity strategy. The value proposition for cybersecurity is defined by how it helps the organization, usually by avoiding or minimizing losses due to digital based attacks. The details however will vary greatly as every company, government, and organization is different. Ultimately, an efficient, effective, and adaptable security capability, which can be sustained over time, must be defined. It describes the balance between security costs, risks, and usability. The strategy is the long-term plan and path to make managing risk easier and better in tune with leadership expectations. The mission, goals, objectives, and success criteria must be documented and clear. The strategy normally includes identifying key assets to protect, regulations to comply with, ethics to uphold, policies to enforce, necessary investments, acceptable usage impacts, and defining overall acceptable losses.
- Facilitate executive communications. Working with the CISO to bridge the gap with the Board and C-suite to tease out long-term qualitative expectations and simultaneously establishing a framework to communicate progress, compliance, posture, and risks. This crucial step sets up the CISO for long-term success.
- Identify and align to future threats. Understanding the future threats, attacker objectives, targets, and likely methods is one of the only ways to break the reactive-only cycle and be proactive in a systematic and efficient way. Many just focus on closing all ‘vulnerabilities’, which is a misnomer as anything can be a vulnerability. Although a well thought-out and prioritized vulnerability management capability is valuable and important, the key is in knowing which weaknesses and potential misuse will be exploited. Better to know your enemy and predict where, why, and how they will attack. This affords a great opportunity to effectively bolster security by aligning the team’s focus in advance.
- Architect a sustainable security capability. At the direction and in partnership with the CISO, build an organization and functional map of security responsibility. Objectives of people and teams support goals of the group that in aggregate satiate the overall mission to meet the Board and C-suite expectations. This defines and clarifies the scope of accountability.
- Build a resourcing model. Headcount, spending, and roles must be tied to deliverables aligned to executive expectations. A good model will predict how many resources are required, with what skillsets and assignments, will be needed for varying levels of deliverables. If demands change, so can expectations in the required investments.
- Develop a security metrics package. Often overlooked, the development of a consistently accurate and unbiased set of measures and metrics is necessary for reporting, continuous improvement, resource allocation, and to determine if the success criteria are being met for any given area. What is important are the indicators that directly tie to impacts and losses. Too often, groups follow the IT ops metrics models that focus on quantities of alerts, traffic, patched deployed, and total systems under control, which have little bearing on actual risk-of-loss mitigation. Nobody cares about the number of false positive alerts received. Frivolous statistics are often manipulated to show work effort, when the real purpose is to mitigate loss. A good metrics package will be the basis for update presentations to mid and front-line managers, C-suite, and the Board to discuss risk, incidents, and impacts.
- Advocate the security vision. The value proposition must be extolled up, down, and laterally across the organization to garner support. Achieving buy-in from other departments is crucial to success. Security strategist are strong in communication and can tell the compelling story like no other. They should be leveraged to rally community support. This function can also extend outside the company, to investors, customers, partners, regulators, vendors, and suppliers. Explaining the needs, value, and expectations is initially complex, but can represent a beneficial business advantage.
I am biased, plain and simple. I have been doing cybersecurity strategy for a very long time and the list above represents the biggest areas of value in my opinion and I expect others to likely have differing viewpoints. I have worked with major businesses in almost every industry, consulted to governments and academia, developed risk methodologies, and spoken at countless security conference across the globe. These are the critical pain points that are pervasive in almost every organization. The professional community as a whole has much growing to do and we must get better. Defining a comprehensive cybersecurity strategy is crucial to building strong foundations for enduring success.
Permanent or expert-for-hire

This is an area where I would like to see more consultant firms and Managed Security Services Provider (MSSP) to step in. Unfortunately, that has not been the case. Even the big consultant groups have not yet been able to fill the gap. I have worked with many of the top technology and enterprise advisory firms. They have tremendous assets and knowledge for the business side of the industry, including tech innovations and services, but largely lack the depth of understanding around cyber threats. Yes, they can answer questions on yesterday’s attacks and provide a list of vendors to help, but generally lack the veteran CISO mindset, understand how to build a sustainable security organization, and are far from being able to read the tea leaves of what cyber-threat challenges are just around the corner.
How many of the top 1000 companies and government use business consulting and research firms? Most. They do represent a tremendous asset for business related challenges, such a product advancement, capable IT services, competitive opportunity advisement, and market research. However, cybersecurity is not the same. It deals with intelligent and creative adversaries with a variety motivations and unorthodox methods which must be mapped to the organization in question. It is asymmetric to the standard IT way of thinking and ruthlessly different than the normal competition in the business world. Clients of these big firms who pay significant annual fees aren’t faring significantly better at resisting attacks, showing immunity from data breaches, or being provided practical insights preparing them in advance from emerging compromises. A few hours of consulting, generalized reports, and narrow research is insufficient. It takes more in-depth and customized insights, married to a well-designed security infrastructure to make that leap forward.
Smaller boutique cybersecurity consultancy firms are a specialty field, that are able to give the necessary attention for exclusive customers, but the model does not scale to meet the broader needs of the market. Most of the successful experts, comprising a very small community, have already been scooped up and are working for big companies as in-house employees or by security product and service firms who leverage them to attract and sustain customers. This leaves dreadfully few to help the vast majority of organizations which cannot afford a dedicated specialist.
For those who choose the path of bringing in an experienced cybersecurity strategist, expect their contributions to take some time to deliver. Every situation is different, but for optimal engagements with medium sized organizations with positive managerial support, estimate 4 months to get everything defined, in place, and sustainable. Larger enterprises or those with complex challenges could take one to two years, such as government agencies with political challenges, cross-oversight dependencies, and formal budgetary processes. There are simply too many variables to narrow the expectations any further. Mileage will vary.
Cybersecurity is one of those niche areas where experience and expertise are necessary to gain ground. Highly customized insights are really what CISO’s need. Answers that are specific to their challenges, technology environment, and risk appetites is valuable. Such guidance is hard to find and like all things in cybersecurity, expensive.
Architecting Sustainability

Cybersecurity fails over time without proper strategic planning. A strategist may be the key resource for a CISO and Board to build the strong foundations needed by an operational cyber-risk mitigation team to remain effective and efficient over time.
Interested in more insights, rants, industry news and experiences? Follow me on your favorite social sites for insights and what is going on in cybersecurity: LinkedIn, Twitter (@Matt_Rosenquist), YouTube, Information Security Strategy blog, Medium, and Steemit
I was shocked when I read that cyber losses add up to more than the illegal drug cartel makes in a year.
A huge illegal enterprise that continues to grow. Organized criminals know this and have been investing in online fraud, hacking, extortion, and black-markets
Great article. Couldn’t agree with you more...
reliable leadership really is key and especially with situations like this
It takes a certain type of (twisted) mind to think ahead and outmaneuver cyber-attackers.
I think cryptojacking and solving the custodian problems for the big institutional investors will be one of the big challenges in 2018 and 2019 for the cyber security industry.
I agree, because crypto has become a target by the cyber-attackers. They go where value exists to find weakness, big scores, and easy victims.