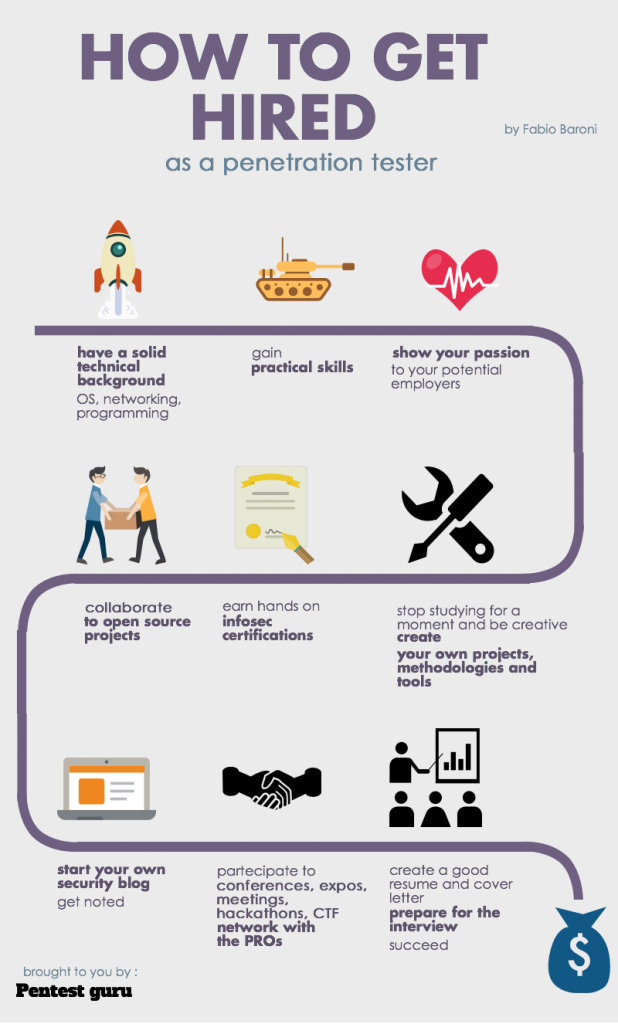
InfoSec Job Interview Questions. At least try to be prepared.
Job interviews are always nerve wracking. When it comes to the InfoSec industry, they can be even more so. The questions can range from trick questions, to incredibly technical, to so simple you want to overthink it. For anyone with an interest in transitioning to the InfoSec field, provided below is a long list of questions that you can anticipate encountering at some point or another in your career.Pentest.guru has an entire blog post, Cracking the infosec interview for fun and profit - how not to suck and get $$ hired$$, with more tips and advice on getting a job interview, as well as the questions below. I went ahead and added a few questions that came to my mind as well. For now, I will only provide the questions so that you can get your brain thinking and maybe discover a few new areas to brush up on. In later posts, I will select a hand full of questions at a time and provide my answers. In the meantime, feel free to comment your own answers, or maybe a few questions that you have encountered in the past.
Network Security
- Are open-source projects more or less secure than proprietary ones?
- How do you change your DNS settings in Linux/Windows?
- What’s the difference between encoding, encryption, and hashing?
- What’s more secure, SSL or HTTPS?
- Can you describe rainbow tables?
- What is salting, and why is it used?
- Who do you look up to within the field of Information Security? Why?
- Where do you get your security news from?
- If you had to both encrypt and compress data during transmission, which would you do first, and why?
- What’s the difference between symmetric and public-key cryptography?
- In public-key cryptography you have a public and a private key, and you often perform both encryption and signing functions. Which key is used for which function?
- What kind of network do you have at home?
- What are the advantages offered by bug bounty programs over normal testing practices?
- What are your first three steps when securing a Linux server?
- What are your first three steps when securing a Windows server?
- Who’s more dangerous to an organization, insiders or outsiders?
- Why is DNS monitoring important?
- What port does ping work over?
- Do you prefer filtered ports or closed ports on your firewall?
- How exactly does traceroute/tracert work at the protocol level?
- What are Linux’s strengths and weaknesses vs. Windows?
- Cryptographically speaking, what is the main method of building a shared secret over a public medium?
- What’s the difference between Diffie-Hellman and RSA?
- What kind of attack is a standard Diffie-Hellman exchange vulnerable to?
- What is an icmp redirect and how can it be exploited?
- How does the ARP protocol work?
- Have you ever caught a botnet with a snmp trap?
- How does SMTP spoofing work?
Application Security
- Describe the last program or script that you wrote. What problem did it solve?
- How would you implement a secure login field on a high traffic website where performance is a consideration?
- What are the various ways to handle account brute forcing?
- What is Cross-Site Request Forgery?
- How does one defend against CSRF?
- If you were a site administrator looking for incoming CSRF attacks, what would you look for?
- What’s the difference between HTTP and HTML?
- How does HTTP handle state?
- What exactly is Cross Site Scripting?
- What’s the difference between stored and reflected XSS?
- What are the common defenses against XSS?
- When was the most recent OWASP Top 10 list published?
- What are the three types of cross site scripting?
- How does HTTP Response Splitting occur?
- What are prepared statements in regards to SQL and SQL Injection.
- How is SQL Injection prevented?
- Explain the Secure Software Development Life Cycle.
Corporate/Risk
- What is the primary reason most companies haven’t fixed their vulnerabilities?
- What’s the goal of information security within an organization?
- What’s the difference between a threat, vulnerability, and a risk?
- If you were to start a job as head engineer or CSO at a Fortune 500 company due to the previous guy being fired for incompetence, what would your priorities be? [Imagine you start on day one with no knowledge of the environment]
- As a corporate Information Security professional, what’s more important to focus on: threats or vulnerabilities?
- What is the biggest threat facing web applications in your experience?
- What does RSA stand for?
- What conferences do you routinely attend?
- How do you create SSL certificate, generically speaking?
- What is meterpreter?
- With regard to forensics, what is physically different about how the platters are used in a 3.5″ and a 2.5″ HDD?
- What’s the difference between a router, a bridge, a hub and a switch?
- What’s port scanning and how does it work?
- Can we perform VA remotely?
- What experience do you have with Data Loss Prevention (DLP)?
- Give me an example of when you thought outside of the box. How did it help your employer?
- What is a spyware?
- Is NT susceptible to flood attacks?
- What is DES?
- What is DNS Hijacking?
- What is LDAP?
- What are DCO and HPA?
- Are there limitations of Intrusion Detection Signatures?
- Please explain how asymmetric encryption works
- How do you determine when to update virus protection systems?
- What is Stuxnet?
- What is Wireshark?
- What do you see as challenges to successfully deploying/monitoring web intrusion detection?
- What ports must I enable to let NBT (NetBios over TCP/IP) through my firewall?
- Are server-side includes insecure?
- What’s the difference between a threat, a vulnerability and a risk?
- What are IDA and/or Olly?
- What is the difference between stored and reflected XSS?
- What is NMAP?
- What is NAT and how does it work?
- What are the standard port numbers for SMTP, POP3, IMAP4, RPC, LDAP and Global Catalog?
- Have you hacked any system?
- Your network as been infected by malware. Please walk me through the process of cleaning up the environment.
- What is PCI compliance testing?
- What is %3C in HTML encoding?
These are excellent questions. They're not just for nerdy expertise but general awareness of life around you.
Most definitely! Some of them make you think quite a bit. Some made me chuckle a bit.