Smartphone botnets have become increasingly popular over the last few years. Android software is highly vulnerable to malware and is constantly targeted by attackers due to the OS’s popularity around the world. Often times the malware is installed on the device via malicious apps found in the Google play store, 3rd party app stores, malicious emails or drive by downloads while browsing from your device.
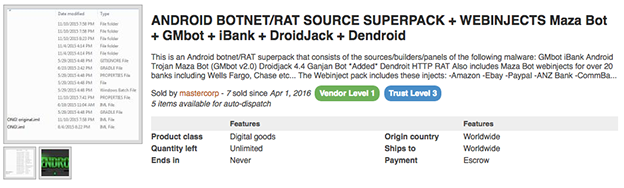
Figure 1: Android Botnet for sale
Infected devices that become part of a botnet can perform certain tasks like record audio and video, take photos, send text messages, open webpages, steal user data, delete files, launch denial of service attacks via HTTP floods and preform web injections, if supported.
The threat of a mobile botnet is very real and often hidden in unsuspecting apps found in different app stores. Once a user is infected, there is very little they can do to detect and remove the malware. A HTTP flood from a mobile botnet can easily produce over 100,000 unique IP addresses. making it increasingly difficult for websites to mitigate such a large scale attack.
The attack works very similarly to a standard botnet. Users are tricked into installing malware that gains root access. Devices that are infected with malware become enslaved into a global botnet. From there, an attacker controls the actions of the device through a command and control system where they can send a number of attack commands to the devices so they will perform the specified action.
There is a growing amount of mobile malware found in the wild that allows an attacker to enlist the compromised device into their botnet for malicious purposes. Malware such as GM bot, Dendroit, DroidJack and Viking Horde are just a few variants seen in the wild. Often times the malware can be purchased on the darknet or from a number of different forums and websites found on the Clearnet.

Figure 2: Android Botnet advertisement
If you experience disrupted or lost network connectivity, fraud, installed or removed applications, or calls, SMS’s and emails being sent without your consent, your device might be infected with malware. It’s suggested that you wipe your phone and restore factory settings if you suspect that your device has been compromised.
Extra
Contact us (Radware)
Contact me (Facebook)
My Introduction and other blogs:
Download Radware’s DDoS Handbook to get expert advice, actionable tools and tips to help detect and stop DDoS attacks.
Hi! I am a content-detection robot. This post is to help manual curators; I have NOT flagged you.
Here is similar content:
https://blog.radware.com/security/2016/05/the-rise-of-smartphone-botnets/
NOTE: I cannot tell if you are the author, so ensure you have proper verification in your post (or in a reply to me), for humans to check!
The many different ip adresses make it hard for website provider to block them. Those attacks are a pain in the ass and more effective in general.
Wow. How much you sell for that bot ? Do you have bot for steemit?
I'm not selling anything.
Please read the post again
Another excellent post; this time on smart phone security. I really appreciate the content.
Thank you.