
We have reached a point inside the age of the internet wherein no records can be assumed to be authentically secure, and that is why it is crucial that we take the important time out of our day to recognize how and why all web sites and offerings should be assumed to be insecure, and protecting operational security measures to prevent these malicious customers from being capable of do something with the facts that they acquire.

If you observe any news outlets, you have probably heard of a number of the current database breaches that resulted inside the mass leaks of person facts, a few examples are: Ashley Madison, Comcast, Adobe, Neopets, Snapchat, NexusMods, Powerbot, Epicbot, Stratfor, YouPorn, and the list simply is going on.

Protection is breached each day, and as a result databases containing personal account facts are stolen, traded, bought, or even publicly leaked. some databases as large as Adobe, and others as small as your favourite forum. every day, databases which can be filled with your account data are shared among the hacker underground. every day, both deserving and harmless human beings are attacked due to malicious customers gaining access to touchy personally identifiable data. in case you use the net like every body else, you then have the ability to be prone to those assaults as nicely. it's far critical to apprehend what you could do to prevent those security breaches from having a great effect to your privacy or anonymity.
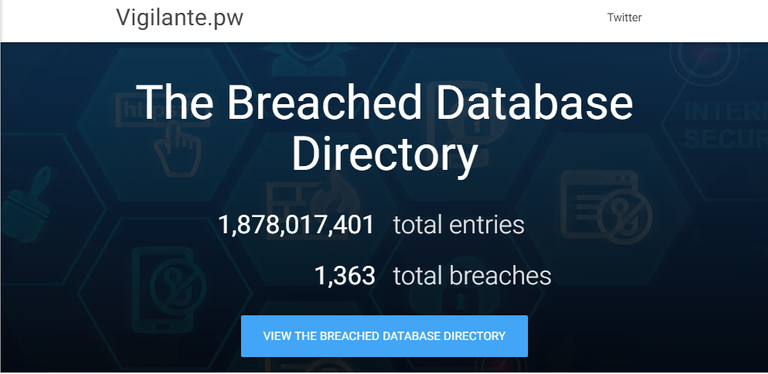
While a database is stolen best one person with malicious rationale has get admission to to it. After the initial breach and extraction of the user desk from the database, the attacker might also decide to do one in every of four matters: sell, change, share, or they'll pick to hold it private. there may be a large market for purchasing, selling and buying and selling databases. After a few months of a database being bought and traded, it turns into pretty saturated, and eventually someone will likely leak that data to the general public. An example of a popular database collector is keen from Vigilante; on Vigilante a listing of databases may be discovered, and you may see if they may be tagged “personal” or “public” for your self, those are all databases which are actively sold and traded each day. keen has left touch info and openly said “add me on Jabber at [email protected] in case you are interested in [discussing] databases.”
Peoples gather databases, and when they have 500,000,000 account entries available from a group of databases from over 1,000 exceptional breached servers, they are able to effortlessly sift via the data to perceive you. packages publicly reachable, like grep, allow an attacker to go into a string that they want to look for, and then it types via each unmarried account access in reputedly no time in any respect. depending on your hard pressure or strong nation drive, 500,000,000 entries can be taken care of thru, line-by-line, in less than half-hour; 30 minutes is all it takes for a malicious investigator to nearly effects discover a unmarried account amongst half one billion different money owed.
This was reported by the author at http://puppet.zone/breaches-and-registration/
Not citing sources is plagiarism, and copying pasting articles without permission is copyright infringement. If you want to share a news story, simply link to the source, and include your original commentary, and possibly small quotes from the source.
Copy paste is discouraged by the community, and may result in action from the cheetah bot.
Creative Commons: If you are reposting under a Creative Commons license, please attribute and link according to the specific license. If you are reposting under CC0 please consider noting that at the end of your post.
If you are actually the original author, please do reply to let us know!
Thank You! ☙