
Keyboard's and Mice are often the most unloved components of your PC
Majority of the considerations when choosing a new keyboard and mouse combo might go toward the colour, style, buttons and connection method.. Generally security is not a consideration. I am here to tell you, Security of these devices is much more important than you might give it credit for!!
Q. What does your Keyboard and Mouse say about you?
A. Potentially everything!
Wireless is the way of the new world and keyboards and mice are no different, a large amount of the high end devices are focused towards wireless solutions for user convenience and I imagine a decent amount of the user's reading this post will be scrolling and potentially typing a reply on a wireless keyboard and mouse combo.
The issue here is that some wireless communication (non-Bluetooth devices in this case) are susceptible to monitoring, recording, interception and manipulation. Similar to any other RF communication these keystrokes, mouse movements and clicks are broadcast into the air for any one listening to hear. This fact could allow a remote attacker up to 100 feet / 30 meters away to eavesdrop on this communication and even inject his own keystrokes and mouse clicks.
Encryption in Modem implementations
Most modern versions of this technology have implemented AES encryption around the keystrokes sent from the keyboard and to a lesser extent the mouse. But there are still a lot of older vulnerable devices in operation and even scarier still being sold on shelves today that include no encryption or a form of encryption that has been provable exploited and is therefore not effective; that is to say key strokes are transmitted in the clear and broadcast over wireless.
Further to this a vast majority of the newer encrypted wireless keyboards have poor implementation which have recently been exploited and allow a remote attacker to inject unencrypted keystrokes to your wireless receiver/dongle which are accepted by the receiver and your computer meaning that within seconds you machines could be executing malicious code and installing backdoors to you system allowing the remote attacker full control of your computer for full scale compromise, data exfiltration, screen and webcam captures the sky is the limit. With this particular attack it is like the attacker is sitting in front of your computer and typing on your keyboard. This could happen at home, in the office, at a cafe anywhere...
Let’s take a look at two type of attacks against wireless keyboards
Attack Type 1 - Key logging:
Keysweeper
In this section we will talk about two types of keysweeper implementations; fist once is the earlier version and comes in such a neat form factor that i cannot be overlooked and the second version dubbed 'KeySniffer' is a newer implementation that affects a wider range of devices.
The $10 Adreno based passive key logger concealed inside a working USB charger.

Samy Kamkar’s implantation of Keysweeper is my favourite approach.
Keysweeper is a stealthy Arduino-based device, camouflaged as a functioning USB wall charger, that wirelessly and passively sniffs, decrypts, logs and reports back (over GSM) all keystrokes from any Microsoft wireless keyboard in the vicinity.
All keystrokes are logged online and locally. SMS alerts are sent upon trigger words, usernames or URLs, exposing passwords. If unplugged, KeySweeper continues to operate using its internal battery and auto-recharges upon repowering. A web based tool allows live keystroke monitoring.
Keysweeper is an older exploit which is still proving to be effective on older Microsoft keyboards and mouse combos. Microsoft has adapted their method of wireless communication and newer implantations to do not suffer from this particular exploit but there are plenty of older Microsoft keyboards that are still at risk!
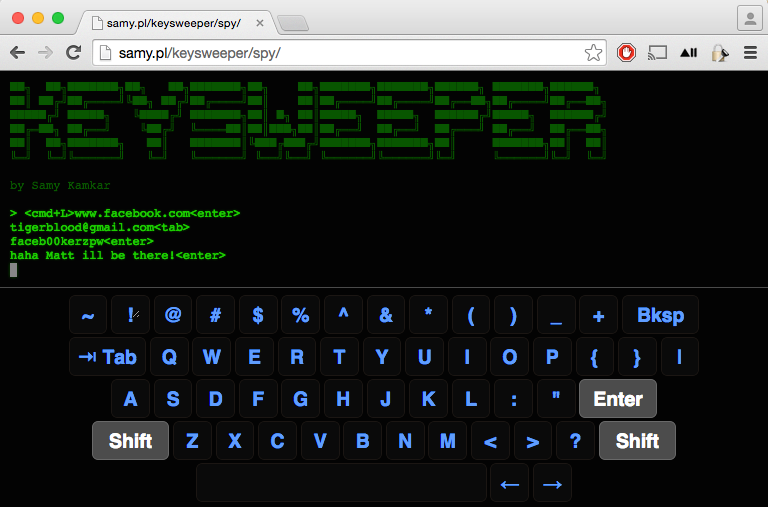
Want to learn more?
To learn more about keysweeper check out samy.pl/keysweeper
KeySniffer - New implementation with a wider range of supported keyboards
The KeySniffer attack has been developed by Marc Newlin from the Bastille Research Team which provide the same ability to monitor and log keystrokes from older non-bluetooth wireless devices that do not implement AES encryption. This technique has been responsibly disclosed to vendors who are issuing firmware updates to resolve the issue. The responsible disclosure period has lapsed and therefore this technique has been made public. This attack is effective against old models of keyboards and some cheap keyboards still manufactured today
It uses a Crazyradio PA - Long Range 2.4Ghz USB Radio Dongle and the attack can be carried out from 100 feet / 30 meters

A list of some vendors who have been recently tested on their current range of keyboards and found to be vulnerable to the attack can be found below
- Anker
- EagleTec
- General Electric
- Hewlett-Packard
- Insignia
- Kensington
- Radio Shack
- Toshiba
This list is not a complete list, For further details regarding models affected and vendor responses, please see http://www.keysniffer.net
Want to learn more?
To learn more about Marc Newlin’s version of keysniffer check out keysniffer.net
What data is vulnerable?
Websites, Passwords; Credit cards, Bank Details, chat messages, personal information and secrets. If you are using a vulnerable keyboard litrally every single keystroke that you type on your keyboard is transmitted and potentially captured.
Think of a super secure password containing 64 Uppercase and Lowercase letters, numbers and symbols that you store on a piece of paper and type in manually for extra air gapped security protecting your password while at rest... That's roughly a 390 bit password and a brute force attack on a medium size botnet would take roughly 7 quattuortrigintillion years; Comparatively the password could be captures in the amount of time it take you to type in into your vulnerable wireless keyboard :(
Attack Type 2 - Keystroke injection
Mousejack – $15 device for keystroke injections - Full system compromise is seconds! – Scary stuff.

MouseJack (Discovered by Marc Newlin) is a class of vulnerabilities that affects the vast majority of wireless, non-Bluetooth keyboards and mice. With MouseJack it is possible to compromise a victim's computer by transmitting specially-crafted radio signals using a device which costs as little as $15.
An attacker can launch the attack from up to 100 meters away. The attacker is able to take control of the target computer, without physically being in front of it, and type arbitrary text or send scripted commands. It is therefore possible to rapidly perform malicious activities without being detected.
The MouseJack exploit centers around injecting unencrypted keystrokes into a target computer. Mouse movements are usually sent unencrypted, and keystrokes on modern devices are often encrypted (to prevent eavesdropping). However the MouseJack vulnerability takes advantage of affected receiver dongles, and their associated software, allowing unencrypted keystrokes transmitted by an attacker to be passed on to the computer's operating system as if the victim had legitimately typed them.
short dramatic video; worth a 2 minute watch
A list of some vendors who have been recently tested on their current range of keyboards and found to be vulnerable to the attack can be found below
- AmazonBasics
- Dell
- Gigabyte
- Hewlett-Packard
- Lenovo
- Logitech
- Microsoft
This list is not a complete list, For further details regarding models affected, please see https://www.bastille.net
TL;DR
If you did not read the section directly above this (MouseJack) and you use a wireless keyboard; read it! it is the most important part of the whole post and a serious security vulnerability
If you are using a wireless (non-bluetooth) keyboard and/or mouse make sure it is not vulnerable to MouseJack at the very least and if it is an older device it might be worth checking its vulnerability to Keysweeper/Keysniffer. All 3 of these attack vectors could be devastating to your personal privacy and digital asset portfolios; this is a seriously easy attack vector that could have you whole system compromised in minutes! With such cheap hardware requirements that are easily accessible by anyone it is not worth the risk.
I personally have replaced all my wireless keyboards with the wired alternatives
wow... guess now it will wired keyboard/mouse.
Is there any wireless keyboard/mouse protected against those hacks ?
Bkuetoith keyboards are bot vulnerable to this attack. Also not all wireless keyboards are vulnerable and sone of the vendirs who are have issue firmware updates to mitigate the issue
Thank you, thank you, thank you! I am just about to go and buy a Logitech ergonomic mouse; I'll stick to the wired version.
Cg
I think it's the keyboard that is at risk so you will be safe with a wireless mouse.
Mice are also vulnerable but it is obviously harder to execute remote commands via a mouse but i would still also be worried that the dongle may also accept keyboard input due to cross use of hardware
Thanks for cleaning that up. I thought it might have been impossible to hijack one's computer without a clear line-of-sight to the screen.
I am changing my wireless mouse and keyboard to wired one .......... the ones that i am using are chinese stuffs, they work well but after reading this article I am 100% sure they are not encrypted.... thanks for this info...
Such learning. Very knowledge! :)
Excellent post!
I never really saw the point of a wireless keyboard, anyway, but I do use a wireless mouse. I will have to investigate how vulnerable it is.
i like u article, nice information :)
Intesting article and needed article, thanks! Too bad it had to be written though! This "old dog" grew up on a street in a big city at a time when no one even locked their doors.
I have always been a gamer, never saw value in having a wireless device, but good information to know for future purchases.
Those attacks are old man it's nothing new, I reads about this in 2014..
Keysweeper is old keysniffer is new and so is mousejack
I'm old fashioned. I'm still wired. :-)
I just read about mobile battery status API browser exploit. Even your battery can't be trusted!
This is some threat many people would never recognize until someone tells them, so thank you for telling us!
I use notebook keyboard and touchpad, so I'm probably safe...
Against this attack yes :)
👍great post @steempower
Wow, great info. Thanks. I never even thought of this before.