
After my post about one part of my job (Ethical Hacking). I will write something about forensics this time. This is also a part of my day job. In this blog I will also introduce a free tool (with GUI) that you can run on your own computer. You will be surprised how much info you can dig up.
How did I become one
When I started doing more security related work I also had to extract information from systems. This could be server related but also user/computer based. Some of them where sensitive cases, so it is vital to follow the right steps. To learn that I followed Digital Forensic courses.
Is it something for you?
If you like to dig around and connect the dots, this is the job. This job is more for analytical people although you also need to think outside of the box. The most difficult part is not how to get information, but how to get the right information.
There are several courses you can follow to become a Forensic specialist. Like for example the Computer Hacking Forensic Investigator (CHFI) from EC-Council. But besides following courses it also about learning something new every day.
The scale is enormous. For example you can use computer memory dumps, hard disks or use logging from firewalls to find out what your after. Just looking trough a memory dump can reveal encryption keys or hashes. But is a needle in a haystack most of the times. So patients is a virtue.
Just like ethical hacking there is a need for specialists. In general you can break down digital forensics in.

How does it work
Before you investigate anything you have to do some administrative work. Like organizing your case. You need a case name (one that does not link to the subject itself). For privacy reasons this is important.
There are 4 steps we can define here.
-
Seizure
Prior to the actual examination digital media will be seized. Well this is obvious ofcourse. There are guidelines on how to do that the right way.
Acquisition
Once the material have been seized an exact duplicate (or "forensic duplicate") of the media is created, usually via a write blocking device. This can be done with hardware or software tools. Like EnCase, FTK Imager or FDAS. This will be verified by using the SHA-1 or MD5 hash functions (Later on the process this will be rechecked. To be sure nothing has changed to the copy). And the original drive is then returned to secure storage to prevent tampering.
Analysis
During the analysis we usually recover evidence material using a number of different methodologies (and tools), often beginning with recovery of deleted material.
Reporting
And ofcourse we need to make a nice report. It is a important last step to get all the details right and make it readable for management (meaning adding cool ;-) pictures).

So just lets have a look at your pc
There are many tools. From simple to very complicated.
A nice tool that is easy to use and already gives you a lot of information about your (past) pc usage is the sleuthkit. Especially interesting is the GUI above it, named Autopsy.
Here you can download it: http://www.sleuthkit.org/autopsy/download.php
So what does it do?
Well a lot of things.
For example:
Cases and Adding Data Sources (this is ideal for keeping info together)
Automated Analysis (Well this gives you a lot of information without any work)
Manual Analysis (The opposite ;-) you have to do some manual labor)
Reporting
Well lets have a short look on what you can do with it. But I am sure you have the most fun doing it on your own computer.
One of the nicest tools that is included in Autopsy is PhotoRec. Based on the name you could think it recovers photos. But it does much more. It recovers a lot of different file types you thought where already gone.
How does file recovery work
File systems store files in data blocks (also called clusters under Windows. When a file is deleted, the meta-information about this file (file name, date/time, size, location of the first data block/cluster, etc.) is lost. The names of deleted files are still present, but the location of the first data block is removed.
This means the data is still present on the file system, but only until some or all of it is overwritten by new file data. To recover these lost files, PhotoRec first tries to find the data block (or cluster).
For example, PhotoRec identifies a JPEG file when a block begins with:
0xff, 0xd8, 0xff, 0xe0
0xff, 0xd8, 0xff, 0xe1
or 0xff, 0xd8, 0xff, 0xfe
Long story short. Autopsy will do all the work for you. This is how it looks like

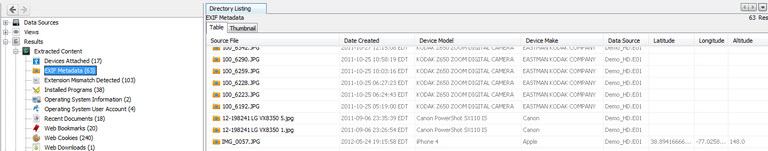
And when you have all these files. It is also nice to get some EXIF data from the pictures
Also very nice (or scary) is how Autopsy makes your Web Activity ( Web Downloads, Web History, Web Searches) visible.
Just play around with it and be surprised. The tool does take it's time tough. But the first results will be shown fast. If you want to know it all. Let it run for a few hours.
Some protection
There is really not much we cannot find out. So better delete your files for real. You can use this tool to clean up already existing "deleted" files/data by typing sdelete d: -c
For day to day delete actions you add a GUI (windows) right click option. Download RightDelete for that.

In future series I will write about more advanced stuff. Like volatility (memory forensics)etc. Thank you for reading this on @timsaid. I appreciate his help. I will also post more on my own blog @disofdis.
Awesome, so much learnings we can get on your post.
How much education have you had on this? You are brilliant...
Haha thank you for the nice words. Lots of practise and learning on the job. And courses ofcourse.
Where at?
Thx
I Will Check Out The Tool
Thank you for your post, I'm slow reared :) English not my native but I try to read all of your topics.
Hey smailer, thanks for the support. Means a lot to me. Started following, nice art!
Thank you :)
And glad to hear what you like my art
Fantastic article man, I love the link to Sleuthkit, I am trying this out!
It is a wonderfull tool for sure.
I'm a big Pentoo linux fan! Loved this article!!
Ah we Can share notes then :)
Thanks for your post and sharing those tools!
Used photorec several times. It was not able to recover photos every time. Maybe because of overwritten data on the original address on the hard drive. By the way good article!