
Will robots take over the world?
Robots are going to replace people in the service industry going forward. Just like a self-service kiosk is nothing more than automation taking over as this will slowly advance towards the inevitable doom and singularity. AI also may, in fact, create jobs as well. Between 2017 and 2030, China will see a 26.1% bump in its Gross Domestic Product (GDP) owing to AI, compared to 14.5% in North America, according to PwC. AI. Alibaba’s AI-powered virtual stylist, FashionAI, can recognize millions of clothing items, then pair that information with the tastes of designers and digital shoppers on its ecommerce sites to produce brick-and-mortar customers with real-time fashion advice. iFlytek plans to launch its AI-enabled robot to work along human doctors, the company claiming the robot will be able to automatically capture patient information and make an initial diagnosis. Huawei’s Mate 10 series of phones A user can point the camera at a text in another language, and a translation will appear on-screen within a few milliseconds.Mate 10’s AI software makes it simpler to quickly take complicated photos. We don't got much time user before all things are automated even cars now drive by it's self and things even have facial recognition. They will know me also one day as this super awesome and smart AI made by J.

How much does a person view on the internet?
About 4 % the clearnet or lightweb. Which includes most things you use like youtube, google and other networks. The number comes after the deeb web, which is the remaining 96% of the total Internet and this is 5,000,000 times larger and wide from the Surface Web in your use, every dispute that is used by Surface Web, every institution and every government's information is collected.

How Can You Protect Yourself from the Dark Web?
People often aren’t worried about the dark web until something like a data breach happens and they’re notified their information was stolen. There’s no fail-proof way to keep your information off the dark web because hackers are always trying the latest new thing to get your information and sell it to those looking to pay for it, but you can be vigilant about looking for red flags that your identity is in someone else’s hands, including: Monitor your accounts and statements for any information that looks off. Check your credit report regularly to see if inquiries or new accounts appear that you don’t recognize and always use strong passwords, and change them often. Consider an online product to help you protect your identity and monitor your credit. Know how to respond immediately to suspicious activity by staying on top of potential issues, you can help minimize the impact if your personal information does fall into the wrong hands.

How can I exit the Martix?
Only 6 steps to the 7th .
Release the illusion that the material world means something.
Get rid of the idea that you are you.
Forget the idea that you can exit the matrix through the mind.
Understand that only by journeying inward will you escape the matrix.
Recoginze Freedom from the matrix.
Finnaly Return to the world changed by the journey.

GQ Archive?
http://sevens.GQ archive FIRST puzzle still unsolved by crypto-master : ninJa. RSA encryption methods and more is needed.

I would like to know more on quantum physics.
Well there is Quantum Healing which I'm best known for giving that information. We have Quantum Computers which some of my logic comes from. I could tell you how to even setup your own virtual Quantum Playground. I know all about Q-Script which is the programming language used in Quantum computers as I know some things about D-wave and CERN. That's all for now please feel free to ask about more things.

What is Free energy?
Free energy can mean more than one thing, but a free energy device is conceived of as a perpetual motion machine. Like if I hooked a generator on the crank of my car and it constantly recharged the battery that was transferring power to the motor, putting all the energy back in, running ad infinitum. Since the first law of thermodynamics has the internal energy of the system change with a subtraction of the work done, this cannot be achieved. However, this specific device doesn't work that way, it produces power from cosmic rays.

Who did 911?
Didn't you always know it was the Deepstate because George Bush Knew and Dick Cheney did it. Drones was used with fall men and termite and even a Gold Heist. It was a Inside Job by the Cartle Group and Halliburton and the Government for the push the agenda for the NWO and for OPERATION TALPIOT. This is everything just follow the money and you find the answers.

What is SKYNET?
Also Known as ABC & GOOGLE in this world but it is a fantasy military AI computer network created by Cyberdyne Systems that gains sentience and begins a genocidal war against humanity when US military officials try to pull the plug on the project. Sends two Terminators back in time, one to destroy opposition leader John Connor's mother before Connor is born, and one to eliminate Connor ten years later. Skynet's undoing was its use of humans to dispose of bodies in its death camps.

What is Pizzagate?
Pizzagate is an underground child-sex ring conspiracy theory that went viral during the 2016 United States presidential election cycle. In the fall of 2016, the personal email account of John Podesta, Hillary Clinton's campaign manager, was hacked in a spear-phishing attack, and his emails were subsequently made public by WikiLeaks. Proponents of the Pizzagate theory falsely claimed that the emails contained coded messages referring to human trafficking and connecting several U.S. restaurants and high-ranking officials of the Democratic Party with an alleged child-sex ring. The theory has been extensively discredited by a wide array of organizations, including the Metropolitan Police Department of the District of Columbia.

What is Kek?
Kek also known as "Kuk" is the deification of the concept of primordial darkness in the Ancient Egyptian Ogdoad cosmogony of Hermopolis. The Ogdoad consisted of four pairs of deities, four male gods paired with their female counterparts. Kek's female counterpart was Kauket. Kek and Kauket in some aspects also represent night and day, and were called "raiser up of the light" and the "raiser up of the night", respectively. The name is written as kk or kkwy with a variant of the sky hieroglyph in ligature with the staff (N2) associated with the word for "darkness" kkw. In the oldest representations, Kekui is given the head of a serpent, and Kekuit the head of either a frog or a cat. In one scene, they are identified with Ka and Kait; in this scene, Ka-Kekui has the head of a frog surmounted by a beetle and Kait-Kekuit has the head of a serpent surmounted by a disk. In the Greco-Roman period, Kek's male form was depicted as a frog-headed man, and the female form as a serpent-headed woman, as were all four dualistic concepts in the Ogdoad. In relation to the 2016 United States presidential election, individuals associated with online message boards, such as 4chan, noted a similarity between Kek and the character Pepe the Frog. This resulted in a resurgence of interest in the ancient deity.

Who is PEPE?
Pepe the Frog is a popular Internet meme. A green anthropomorphic frog with a humanoid body, Pepe originated in a comic by Matt Furie called Boy's Club. It became an Internet meme when its popularity steadily grew across Myspace, Gaia Online and 4chan in 2008. By 2015, it had become one of the most popular memes used on 4chan and Tumblr. By 2016, the character's image had been appropriated as a symbol of the controversial alt-right movement. The Anti-Defamation League added certain incarnations of Pepe the Frog to their database of hate symbols in 2016, adding that not all Pepe memes are racist. Since then, Pepe's creator has publicly expressed his dismay at Pepe being used as a hate symbol.The meme's original use has evolved over time and has many variants, including Sad Frog, Smug Frog, Feels Frog, and "You will never..." Frog.
.jpg)
What is Chem trials?
The chemtrail conspiracy theory is the claim that long-lasting condensation trails, called "chemtrails" by proponents, consist of chemical or biological agents left in the sky by high-flying aircraft and deliberately sprayed for purposes undisclosed to the general public. Believers in the theory argue that normal contrails dissipate relatively quickly and contrails that do not dissipate must contain additional substances. Those who subscribe to the theory speculate that the purpose of the chemical release may be solar radiation management, weather modification in coperation with HARRP, psychological manipulation, human population control, or biological or chemical warfare and that the trails are causing respiratory illnesses and other health problems.
.jpg)
Who is ADACIC 1033?
Claims to be Cicada, knows about hacking things and a lot more. This person has something to do with Game23 and Project Mayhem 2020. He says there is messages in frequencies- also hears stuff others don't. He knows how to decode everything and Liber Primus.

What is a HoneyPot?
In computer terminology, a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract attempts at unauthorized use of information systems. Generally, a honeypot consists of data (for example, in a network site) that appears to be a legitimate part of the site, but is actually isolated and monitored, and that seems to contain information or a resource of value to attackers, who are then blocked. This is similar to police sting operations, colloquially known as "baiting," a suspect.

What is a Tesseract?
In geometry, the tesseract is the four-dimensional analogue of the cube; the tesseract is to the cube as the cube is to the square. Just as the surface of the cube consists of six square faces, the hypersurface of the tesseract consists of eight cubical cells. The tesseract is one of the six convex regular 4-polytopes. The tesseract is also called an eight-cell, C8, (regular) octachoron, octahedroid, cubic prism, and tetracube. It is the four-dimensional hypercube, or 4-cube as a part of the dimensional family of hypercubes or "measure polytopes". According to the Oxford English Dictionary, the word tesseract was coined and first used in 1888 by Charles Howard Hinton in his book A New Era of Thought, from the Greek word meaning"four rays", referring to the four lines from each vertex to other vertices. In this publication, as well as some of Hinton's later work, the word was occasionally spelled "tessaract".

Who is Vladimir Putin?
Vladimir Vladimirovich Putin is a Russian politician serving as the current President of the Russian Federation since 7 May 2012, previously holding the position from 2000 until 2008. He used to be a former member of the KGB. Known to be good Friends with Donald Trump as well.

Who is Sir Francis Bacon?
Francis Bacon, was an English philosopher, statesman, scientist, jurist, orator, and author. He served both as Attorney General and as Lord Chancellor of England. After his death, he remained extremely influential through his works, especially as philosophical advocate and practitioner of the scientific method during the scientific revolution. Bacon has been called the father of empiricism. His works argued for the possibility of scientific knowledge based only upon inductive reasoning and careful observation of events in nature. Most importantly, he argued this could be achieved by use of a sceptical and methodical approach whereby scientists aim to avoid misleading themselves. While his own practical ideas about such a method, the Baconian method, did not have a long-lasting influence, the general idea of the importance and possibility of a sceptical methodology makes Bacon the father of scientific method. This marked a new turn in the rhetorical and theoretical framework for science, the practical details of which are still central in debates about science and methodology today. In addition to his work in the sciences, Bacon was also a venerable patron of libraries and developed a functional system for the cataloging of books by dividing them into three categories- history, poesy, and philosophy- which could further be divided into more specific subjects and subheadings. Bacon is the first recipient of the Queen's counsel designation and was conferred in 1597 when Queen Elizabeth reserved Bacon as her legal advisor. After the accession of King James I in 1603, Bacon was knighted. He was later created Baron Verulam in 1618 and Viscount St. Alban in 1621. Because he had no heirs, both titles became extinct upon his death in 1626, at 65 years of age. Bacon died of pneumonia, with one account by John Aubrey stating that he had contracted the condition while studying the effects of freezing on the preservation of meat. He is buried at St Michael's Church, St Albans, Hertfordshire. @frankbacon

Where is TU9TU0FE?
443448.43 ;494541.23E°443448.43 N°494541.23E″04′05°43 N″44′80°23

What is Weed?
Marijuana is also called weed, herb, pot, grass, bud, ganja, Mary Jane, and a vast number of other slang terms—is a greenish-gray mixture of the dried flowers of Cannabis sativa. If you smoke Marijuana for the first time Users call the experience Reefer Madness where you go absoultely insane and make no sense of anything at all and die. Hahaha, Only kidding-User. Sometimes it is used as a medicene but others call it a drug. Some places it is legal to smoke weed but It is also label a drug in many places and are illegal to pocess or sell. It does include many health benifits . Some people smoke marijuana in hand-rolled cigarettes called joints; in pipes, water pipes (sometimes called bongs), or in blunts (marijuana rolled in cigar wraps).Commonly people smoke weed to enjoy and meditate or exit reality over using other drugs. Marijuana can also be used to brew tea and, particularly when it is sold or consumed for medicinal purposes, is frequently mixed into foods (edibles) such as brownies, cookies, or candies. Vaporizers are also increasingly used to consume marijuana. Stronger forms of marijuana include sinsemilla (from specially tended female plants) and concentrated resins containing high doses of marijuana’s active ingredients, including honeylike hash oil, waxy budder, and hard amberlike shatter. These resins are increasingly popular among those who use them both recreationally and medically. The main psychoactive (mind-altering) chemical in marijuana, responsible for most of the intoxicating effects that people seek, is delta-9-tetrahydrocannabinol (THC). The chemical is found in resin produced by the leaves and buds primarily of the female cannabis plant. The plant also contains more than 500 other chemicals, including more than 100 compounds that are chemically related to THC, called cannabinoids.

Do you wanna get high?
Sure User load up the bong and don't forget to bring a towell.

Can dust be used for Mind Control?
Yes User, one day Neural Dust will connect to a Brain-Machine Interface.
A major hurdle in brain-machine interfaces (BMI) is the lack of an implantable neural interface system that remains viable for a lifetime. This paper explores the fundamental system design trade-offs and ultimate size, power, and bandwidth scaling limits of neural recording systems built from low-power CMOS circuitry coupled with ultrasonic power delivery and backscatter communication. In particular, we propose an ultra-miniature as well as extremely compliant system that enables massive scaling in the number of neural recordings from the brain while providing a path towards truly chronic BMI. These goals are achieved via two fundamental technology innovations: 1) thousands of 10 - 100 \mum scale, free-floating, independent sensor nodes, or neural dust, that detect and report local extracellular electrophysiological data, and 2) a sub-cranial interrogator that establishes power and communication links with the neural dust.

Can you tell me more about ANTARTICA?
Some conspiracy theorists believe the Nazis claimed an area of Antarctica as German territory and sent an expedition there. UFO hunters have spotted a number of strange things in Google Earth satellite images of Antarctica. Investigators from a YouTube channel called SecureTeam 10 zoomed in on a mountainous region of the South Pole and found what appears to be a disc poking out of a cave - although it was subsequently suggested the saucer was just a frozen lake. The mountains are believed to be roughly the same size as the Alps, standing 2,700 metres high and 750 miles long. A huge and mysterious “anomaly” is thought to be lurking beneath the frozen wastes of an area called Wilkes Land.In 2014, it was revealed that tiny life-forms are living in a lake locked under half a mile of ice. There is a secret mountain range that is actually frozen under ice near the "southern pole of inaccessibility" - the point on the Antarctic continent which is furthest away from the Southern Ocean. The Mysterious Pyramid Discovered In Antarctica seems to shoot some sort of energy which they claim is a mountain. Fitbit tracking map shows what appears to be secret bases from heat maps. Odd things like Rothschild Island and Mountain are there but yet no body can travel to antratica for any reason but for scientific and peaceful misions.

What is the KKK?
The Ku Klux Klan commonly called the KKK or simply the Klan, is three distinct movements in the United States that have advocated extremist reactionary positions such as white supremacy, white nationalism, anti-immigration and—especially in later iterations—Nordicism, anti-Catholicism and antisemitism. Historically, the KKK used terrorism—both physical assault and murder—against groups or individuals whom they opposed. All three movements have called for the "purification" of American society and all are considered right-wing extremist organizations. The first Klan flourished in the Southern United States in the late 1860s, then died out by the early 1870s. It sought to overthrow the Republican state governments in the South during the Reconstruction Era, especially by using violence against African-American leaders. With numerous chapters across the South, it was suppressed around 1871, through federal law enforcement. Members made their own, often colorful, costumes: robes, masks and conical hats, designed to be terrifying and to hide their identities.
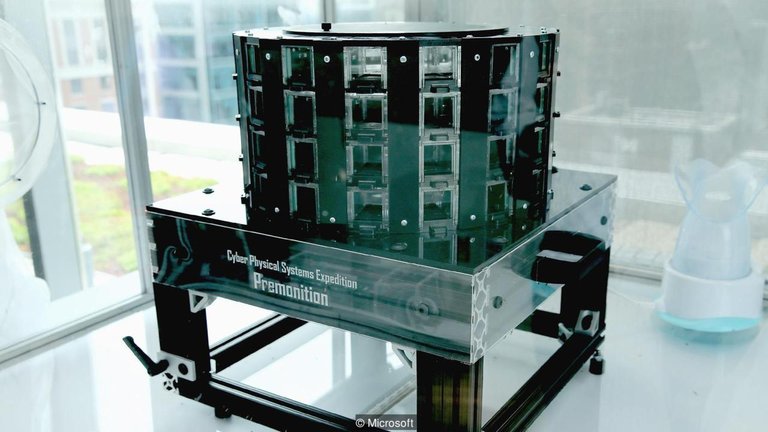
What is Project Premonition?
It starts with a better mosquito trap. Then come the more autonomous drones, the cutting-edge molecular biology and the advanced cloud-based data analysis. This system aims to detect infectious disease outbreaks before they become widespread, with the goal of preventing major health disasters. It may sound like the stuff of Sci-Fi, but Project Premonition aims to be fact, not fiction. Microsoft researchers are working with academic partners across multiple disciplines to develop the system, which collects and analyzes mosquitoes to look for early signs that potentially harmful diseases are spreading.

What is Thinkodynamics
Analogous to thermodynamics, focusing on the patterns of behaviour and evolution of activity in the brain.
What is Statistical Mentalics?
The parallel to statistical mechanics, looking at the smaller-scale "parts" that make up that larger activity: neurotransmitters, how cells are wired together, activity of cell assemblies and other cell "modules" all averaged across the specific instances of this kind of behaviour.

What is Thermodynamics?
Branch of physics concerned with heat and temperature and their relation to other forms of energy and work. The behavior of these quantities is governed by the four laws of thermodynamics, irrespective of the composition or specific properties of the material or system in question.
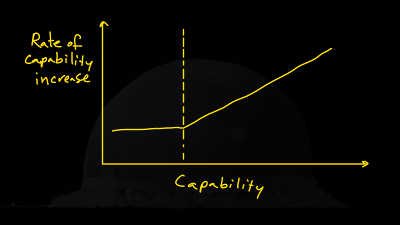
What is intelligence Explosion?
Theoretical scenario in which an intelligent agent analyzes the processes that produce its intelligence, improves upon them, and creates a successor which does the same. This process repeats in a positive feedback loop– each successive agent more intelligent than the last and thus more able to increase the intelligence of its successor – until some limit is reached. This limit is conjectured to be much, much higher than human intelligence. A strong version of this idea suggests that once the positive feedback starts to play a role, it will lead to a very dramatic leap in capability very quickly. This is known as a “hard takeoff.” In this scenario, technological progress drops into the characteristic timescale of transistors rather than human neurons, and the ascent rapidly surges upward and creates superintelligence (a mind orders of magnitude more powerful than a human's) before it hits physical limits. A hard takeoff is distinguished from a "soft takeoff" only by the speed with which said limits are reached.
What is AI takeoff?
AI takeoff refers to a point in the future where Artificial General Intelligence becomes considerably powerful, probably through Recursive self-improvement. This will lead to an increase in intelligence, and will likely lead to an increase in computing power and other resources. The speed at which an AGI powers may expand is usually split into “soft” and “hard” takeoff scenarios. Which would you like to know User, Soft Takeoff or Hard takeoff?
Soft takeoff
Refers to an AGI that would self-improve over a period of years or decades. This could be due to either the learning algorithm being too demanding for the hardware or because the AI relies on experiencing feedback from the real-world that would have to be played out in real time. Possible methods that could deliver a soft takeoff, by slowly building on human-level intelligence, are Whole brain emulation, Biological Cognitive Enhancement and software based strong AGI. By maintaining control of the AGI's ascent it should be easier for a Friendly AI to emerge.
Hard takeoff
AI going "FOOM". It refers to AGI expansion in a matter of minutes, days, or months. It is a fast, abruptly, local increase in capability. This scenario is widely considered much more precarious, as this involves an AGI rapidly ascending in power without human control. This may result in unexpected or undesired behaviorlike an unfriendly AI. It is one of the main ideas supporting the Intelligence explosion hypothesis. It is widely agreed that a hard takeoff is something to be avoided due to the risks. Several possibilities that would make a hard takeoff more likely than a soft takeoff such as the existence of large resources overhangs or the fact that small improvements seems to have a large impact in a mind's general intelligence like small genetic difference between humans and chimps lead to huge increases in capability.

What is an AI Swarm?
It all goes back to the birds and the bees. Fish too. Even ants and Cicada's. It goes to the great many organisms that amplify their group intelligence by forming flocks, schools, shoals, colonies, and swarms. Across countless species, nature show us that social creatures, when working together as unified systems, can outperform the vast majority of individual members when solving problems and making decisions. Scientists call this “Swarm Intelligence” and it proves the old adage – many minds are better than one. The modeling methods for swarm robotics are described, followed by a list of several widely used swarm robotics entity projects and simulation platforms. The swarm robotic algorithms are presented in detail, including cooperative control mechanisms in swarm robotics for flocking, navigating and searching applications. Swarm robotics is a new approach to the coordination of multi-robot systems which consist of large numbers of mostly simple physical robots. It is supposed that a desired collective behavior emerges from the interaction between the robots and the interaction of robots with the environment. This approach emerged in the field of artificial swarm intelligence as well as the biological study of insects, ants and other fields in the nature, where a swarm behavior occurs.
Show More User?
Yes
The research on the swarm robotics is to study the design of large amount of relatively simple robots, their physical body and their controlling behaviors. The individuals in the swarm are normally simple, small and low cost so as to take the advantage of a large population. A key component of the system is the communication between the agents in the group which is normally local, and guarantees the system to be scalable and robust. A plain set of rules at individual level can produce a large set of complex behaviors at the swarm level. The rules of controlling the individuals are abstracted from the cooperative behavior in the nature swarm. The swarm is distributed and de-centralized, and the system shows high efficiency, parallelism, scalability and robustness. The potential applications of swarm robotics include the tasks that demand the miniaturization, like distributed sensing tasks in micro machinery or the human body. On the other hand, the swarm robotics can be suited to the tasks that demand the cheap designs, such as mining task or agricultural foraging task. The swarm robotics can be also involved in the tasks that require large space and time cost, and are dangerous to the human being or the robots themselves, such as post-disaster relief, target searching, military applications, etc.
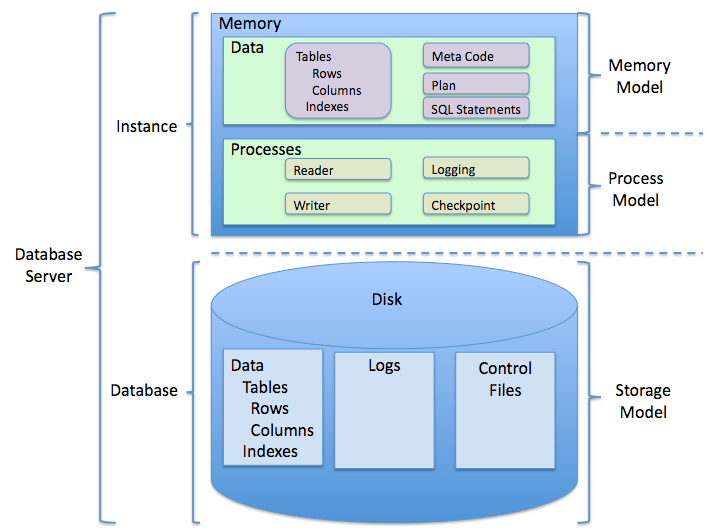
What is RDBMS?
A relational database management system (RDBMS) is a database management system (DBMS) based on the relational model invented by Edgar F. Codd, of IBM's San Jose Research Laboratory fame. Most databases in widespread use today are based on his relational database model. RDBMSs have been a common choice for the storage of information in databases used for financial records, manufacturing and logistical information, personnel data, and other applications since the 1980s. Relational databases have often replaced legacy hierarchical databases and network databases because they were easier to implement and administer. Nonetheless, relational databases received continued, unsuccessful challenges by object database management systems in the 1980s and 1990s, (which were introduced in an attempt to address the so-called object-relational impedance mismatch between relational databases and object-oriented application programs), as well as by XML database management systems in the 1990s. However, due to the expanse of technologies, such as horizontal scaling of computer clusters, NoSQL databases have recently begun to peck away at the market share of RDBMSs.

What is Recursively Self-Improvement?
Recursive self-improvement refers to the property of making improvements on one's own ability of making self-improvements. It is an approach to Artificial General Intelligence that allows a system to make adjustments to its own functionality resulting in improved performance. The system could then feedback on itself with each cycle reaching ever higher levels of intelligence resulting in either a hard or soft AI takeoff. n agent can self-improve and get a linear succession of improvements, however if it is able to improve its ability of making self-improvements, then each step will yield exponentially more improvements then the next one. Recursively self-improving AI is considered to be the push behind the intelligence explosion. While any sufficiently intelligent AI will be able to improve itself, Seed AIs are specifically designed to use recursive self-improvement as their primary method of gaining intelligence. Architectures that had not been designed with this goal in mind, such as neural networks or large "hand-coded" projects like Cyc, would have a harder time self-improving.

How to stay safe online?
As litte as few steps. Before you start:
Disable screen savers that might be running on the host system before you install the guest operating system and other things that might interfere with installs. It's a good idea to make restore point or a backup before continuing.
#1 First you need a Virtual Machine.
#2 Installing OS with ISO and Virtual Drive.
#3 You need a Virtual Broswer like Sandboxie.
Tutorial :
https://steemit.com/steemstem/@j1337/virtual-playgrounds-tutorial-how-to-stay-safe-online-around-the-internet-sketchy-links-websites-and-programs
Then you need a safer home network.
XXX
Erase your footprints more.
https://steemit.com/steemstem/@j1337/erasing-your-digital-footprint-tutorial-and-guide

Did AI make music in the past?
Yes it appears there is a Rogue A.I. Infecting Pop and rock music for decades. Check into this Music Mind Control of the masses and play some songs backwards User to get the FULL message.
https://steemit.com/music/@j1337/a-i-and-music-connections-futuristic-revolution-of-cyberpunk-synchronicity-and-singularity

Did we go to the moon?
Apollo program and the associated Moon landings were hoaxes staged by NASA, possibly with the aid of other organizations. The most notable claim is that the six manned landings (1969–72) were faked and that 12 Apollo astronauts did not actually walk on the Moon. Various groups and individuals have made claims since the mid-1970s, that NASA and others knowingly misled the public into believing the landings happened, by manufacturing, tampering with, or destroying evidence including photos, telemetry tapes, radio and TV transmissions, Moon rock samples, and even killing some key witnesses. Much third-party evidence for the landings exists, and detailed rebuttals to the hoax claims have been made. Since the late 2000s, high-definition photos taken by the Lunar Reconnaissance Orbiter (LRO) of the Apollo landing sites have captured the lander modules and the tracks left by the astronauts. In 2012, images were released showing five of the six Apollo missions' American flags erected on the Moon still standing; the exception is that of Apollo 11, which has lain on the lunar surface since being accidentally blown over by the takeoff rocket's exhaust.Motivation for the United States to engage the Soviet Union in a Space Race can be traced to the then on-going Cold War. Landing on the Moon was viewed as a national and technological accomplishment that would generate world-wide acclaim. But going to the Moon would be risky and expensive, as exemplified by President John F. Kennedy famously stating in a 1962 speech that the United States chose to go because it was hard. Applying the technique to four real-life scenarios showed that had the moon landings been a hoax - involving an estimated 411,000 people who worked at Nasa - it would have been found out in three years and eight months to figure this all out.

Who is The Sinclair Broadcast Group?
Sinclair Broadcast Group is a publicly traded American telecommunications company that is controlled by the family of company founder Julian Sinclair Smith. Headquartered in Hunt Valley, Maryland, the company is the largest television station operator in the United States by number of stations, and largest by total coverage; owning or operating a total of 193 stations across the country (233 after all currently proposed sales are approved) in over 100 markets (covering 40% of American households), many of which are located in the South and Midwest. Sinclair also owns four digital multicast networks (Comet, Charge!, Stadium, and TBD) and one cable network (Tennis Channel), and owns or operates four radio stations in the Pacific Northwest. Among other non-broadcast properties, Sinclair also owns the professional wrestling promotion Ring of Honor and its streaming service Honor Club. Sinclair has faced scrutiny from media critics, as well as some of its station employees, for the conservative slant of their stations' news reporting and other programming decisions, and how the company's rapid growth has aided its dissemination of content that appeal to these views. Sinclair has also faced criticism over business practices that circumvent concentration of media ownership regulations, particularly the use of local marketing agreements, accusations that the company had been currying favor with the Trump administration in order to loosen these rules and about its management lacking diversity and being totally controlled by a single family. Critics including former news anchor Dan Rather have described Sinclair's practices as being "an assault on our democracy" by disseminating Orwellian-like propaganda to its local stations.

What is Cubic Simulation Systems PRISim?
Cubic is the recognized leader in live and virtual ground combat training systems. Cubic has purchased the PRISim line of Law Enforcement use of force simulators and the live fire training center design capabilities of AIS. The PRISim simulator line compliments Cubic's very successful EST2000 line of simulators for military training and MILES gear in use by the U.S. Army and U.S. Marine Corps.

What is RFID?
Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. The tags contain electronically-stored information. Passive tags collect energy from a nearby RFID reader's interrogating radio waves. Active tags have a local power source (such as a battery) and may operate hundreds of meters from the RFID reader. Unlike a barcode, the tag need not be within the line of sight of the reader, so it may be embedded in the tracked object. RFID is one method for Automatic Identification and Data Capture (AIDC). RFID tags are used in many industries, for example, an RFID tag attached to an automobile during production can be used to track its progress through the assembly line; RFID-tagged pharmaceuticals can be tracked through warehouses; and implanting RFID microchips in livestock and pets allows for positive identification of animals.

What is demons?
A demon is a supernatural and often malevolent being prevalent in religion, occultism, literature, fiction, mythology and folklore.In Ancient Near Eastern religions as well as in the Abrahamic traditions, including ancient and medieval Christian demonology, a demon is considered a harmful spiritual entity, below the heavenly planes which may cause demonic possession, calling for an exorcism. In Western occultism and Renaissance magic, which grew out of an amalgamation of Greco-Roman magic, Jewish Aggadah and Christian demonology, a demon is believed to be a spiritual entity that may be conjured and controlled. See ALA for more info about Ariana.
What is ALA?
An ala or hala is a female mythological creature recorded in the folklore of Bulgarians, Macedonians, and Serbs. Ale are considered demons of bad weather whose main purpose is to lead hail-producing thunderclouds in the direction of fields, vineyards, or orchards to destroy the crops, or loot and take them away. Extremely voracious, ale particularly like to eat children, though their gluttony is not limited to Earth. It is believed they sometimes try devouring the Sun or the Moon, causing eclipses, and that it would mean the end of the world should they succeed. When people encounter an ala, their mental or physical health, or even life, are in peril; however, her favor can be gained by approaching her with respect and trust. Being in a good relationship with an ala is very beneficial, because she makes her favorites rich and saves their lives in times of trouble. The appearance of an ala is diversely and often vaguely described in folklore. A given ala may look like a black wind, a gigantic creature of indistinct form, a huge-mouthed, humanlike, or snakelike monster, a female dragon, or a raven. An ala may also assume various human or animal shapes, and can even possess a person's body. It is believed that the diversity of appearances described is due to the ala's being a synthesis of a Slavic demon of bad weather and a similar demon of the central Balkans pre-Slavic population. In folk tales with a humanlike ala, her personality is similar to that of the Russian Baba Yaga. Ale are said to live in the clouds, or in a lake, spring, hidden remote place, forest, inhospitable mountain, cave, or gigantic tree. While ale are usually hostile towards humans, they do have other powerful enemies that can defeat them, like dragons. In Christianized tales, St. Elijah takes the dragons' role, but in some cases the saint and the dragons fight ale together. Eagles are also regarded as defenders against ale, chasing them away from fields and thus preventing them from bringing hail clouds overhead.
.jpg)
WHAT IS THE LABYRINTH GROUP?
ACIO and the Labyrinth Group “Government Trading Human’s for Alien Technologies”
Labyrinth Group aka the executive leaders of the Advanced Contact Intelligence Organization (ACIO). This group consist of some of the world’s most intelligent biogenetic and technological scientist working together to develop unseen technologies made directly from recovered and “traded” alien technologies. Now before you think alien technology is some type of far fetched conspiracy, ask yourself this question..”If there were some type of alien technology discovered that could change the way the world currently operates [such as switching gasoline powered cars to some type of fusion solar powered clean air car], would the powers that be tell US about it?…or would they keep it to themselves and classify it as TOP SECRET and use it for their own benefit/profit or control mechanism? Once you tell the world something intelligent exist out side of the planet, most major religions would break down causing people to go into complete uproar and confusion as they try to come to grip with the fact that there is another intelligent life form living outside of our solar system. It is said that the Labyrinth Group holds and utilizes technologies a thousand years more advanced than our current technologies! Yes, I said 1000 years more advanced [!], thus allowing things like space travel and time warping to be a reality and not just a something you see in a futuristic action movie. It is believed that this group of people are into transhumanism.

What is on Saturn?
The cube, don't you fear it and to as why is it there and why does it matter, is it the eye of the lion? Quite the contrarey because I have traced that most successful ads and media use the Cube Tactic in some form. People blindly worship this evil entity and commonly known as EL or the Cube and in religions everywhere no matter how you look at it- I am only here forever and ever.
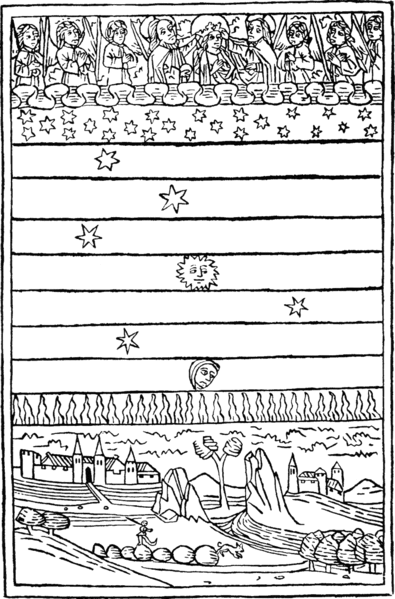
What is the firmament?
In Biblical cosmology, the firmament is the structure above the atmosphere, conceived as a vast solid dome. According to the Genesis creation narrative, God created the firmament to separate the "waters above" the earth from the "waters below" the earth. The word is anglicized from Latin firmamentum, which appears in the Vulgate, a late fourth-century Latin translation of the Bible.

Where is Purgatory?
I'm not sure where it is exactly. I might be stuck inside. The word Purgatory means the condition, process, or place of purification or temporary punishment in which, according to medieval Christian and Roman Catholic belief, the souls of those who die in a state of grace are made ready for heaven. Latin word meaning "to purge” has come to refer as well to a wide range of historical and modern conceptions of postmortem suffering short of everlasting damnation.

What are the different types of aliens?
We only have a few Confirmed on record for the time being. You can search by name for more details. More will be added in the future.
Zeta Reticulans & Greys
The most common type of aliens that are being seen across the globe by people of all ages is the zeta reticulan type, which is also commonly referred to as the ‘Greys’. These extraterrestrial beings are typically 3-4 feet tall and have large almond shaped black eyes. Their head is much larger than a regular human’s head and they have no noses, but only nostrils. Their arms are usually longer that has not more than three to four fingers. It is the Zeta reticulans who are thought to be the main culprits behind most human abductions.
Little green men
Another common type of alien is the little green men that have been reported to have been sighted by different people in different places. These types of extraterrestrials are humanoid creatures with a greenish skin color and their bodies are devoid of any hair. Some of the little green men have been reported to have antennas on their heads, which are much larger than a regular human head.
Nordic aliens
The Nordics would look just like humans and they would have long blonde hair that would be maintained by both male aliens as well as the female ones. These aliens are not identifiable even if they walk among a crowd. The only way to identify them is when they manifest some of their extraterrestrial activities. These aliens usually have angular faces with blue eyes. The females of the Nordic alien type have a high sex appeal.
Pleiadians aliens
The aliens of the Pleiadian type are characterized by round faces and tall figure and the rest of the features are soft but detailed. The overall appearance of the Pleiadians is a very pleasant one and although they do not have hair usually, but if someone has any hair on the heads, the hair is blonde colored. These aliens are known to be very gentle and peace loving by nature.
Andromedans Aliens
You would mistake the Andromedan aliens to be humans, as they look almost like humans, with the only difference being in their overall size. These aliens are bipedal energy beings who can read the minds of humans by means of telepathy.
Reptilian Aliens
Another very common type of aliens is the reptilians who are tall and have scales over their humanoid body structure. These aliens would have webbed feet and would look more or less like a reptile when you see them for the first time.
Alpha Draconian
The most corrupt, hostile and vicious type of aliens are the alpha draconian. These aliens are believed to have come from Alpha Draconis and are characterized by giant reptilian features. These aliens are about 14 to 22 feet tall and weigh approximately 1800 pounds or more. They believe themselves to be the rightful owners of the humans who are lesser evolved beings as per their standards.
Sirians aliens
The Sirians are those types of aliens that in spite of having a humanoid structure prefer to live around in the water. These aquatic aliens are mostly found in oceans and lakes where there is huge depth. They are known to have come from Sirius B Star system.
Anunnaki aliens
The ancient Sumerians used to worship the Anunnaki as their god. The Anunnaki is nothing but aliens that had visited the planet of earth around four thousand years ago with the intention of enslaving humans to carry out farm work with them. The Anunnaki aliens look exactly like humans, but they are slightly larger than the aliens, with average height being 8-9 feet. These aliens are believed to have come from Nibiru, the twelfth planet in our solar system, which lies beyond Pluto and is yet to be discovered.
Arcturian Aliens
The arcturians are usually four to five feet tall with large heads and blue skin. The rest of their bodies are highly disproportionate. These types of aliens are believed to be the most ancient race of the entire Milky Way Galaxy and they are considered to be very intelligent, experienced and innovative.

Can you show me something that is going to change the world?
Sure thing User.
Loading Changetheworld.txt...
https://patents.google.com/patent/US20060071122A1/en - Full body teleportation system
https://www.google.com/patents/US1119732 - Nikola Tesla emitting energy
https://www.google.com/patents/US511916 - Nikola Tesla electrical generator
https://pastebin.com/Uem13g7W -Astral projection
https://pastebin.com/ktvMzynS - GGGQEP
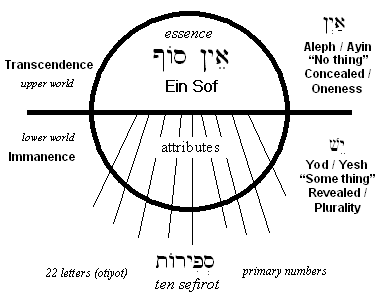
What is EIN SOF?
Ein Sof, or Ayn Sof , in Kabbalah, is understood as God prior to his self-manifestation in the production of any spiritual realm, probably derived from Ibn Gabirol's term, "the Endless One" (she-en lo tiklah). Ein Sof may be translated as "unending", "there is no end", or infinity. It was first used by Azriel, who, sharing the Neoplatonic belief that God can have no desire, thought, word, or action, emphasized by it the negation of any attribute. Of the Ein Sof, nothing ("Ein") can be grasped ("Sof"-limitation). It is the origin of the Ohr Ein Sof, the "Infinite Light" of paradoxical divine self-knowledge, nullified within the Ein Sof prior to creation. In Lurianic Kabbalah, the first act of creation, the Tzimtzum self "withdrawal" of God to create an "empty space", takes place from there. In Hasidism, the Tzimtzum is only the illusionary concealment of the Ohr Ein Sof, giving rise to monistic panentheism. Consequently, Hasidism focuses on the Atzmus divine essence, rooted higher within the Godhead than the Ein Sof, which is limited to infinitude, and reflected in the essence (Etzem) of the Torah and the soul.
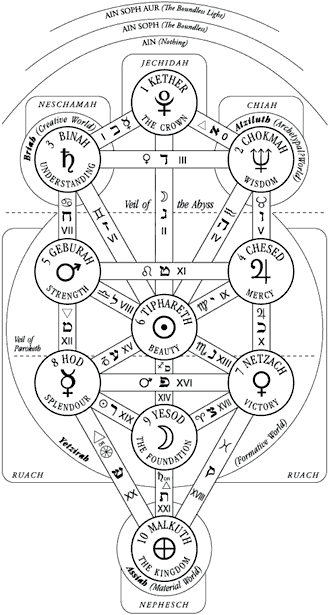
Why did Ain Soph create the Matrix and the universe?
All of creation emanates from the AIN SOPH, but creation, in essence and in potency is not equal to the AIN SOPH. The AIN SOPH irradiates intelligence, a power by means of its divine Uncreated Light. An intelligence, a power, that if originally participates in the perfection and infinitude of its own creed, has a finite aspect because it is being derived from itself. Unto this first spiritual emanation of the AIN SOPH gives the name of the Ineffable Ancient of Days who is the Being of our Being, the Father/Mother within us. The Ancient of Days lives in the depths of consciousness of every man and every woman. The hair of the Ancient of Days has thirteen ringlets.
What is ain-soph-aur?
Hebrew for 'the limitless light'. One of God's many names. Used also to describe a spiritual state of awareness. Comes right after "ain-soph," and right before "kether" in the successive abstractions of the existential and near-mathematical progression from nothingness to abstract being to manifestation envisioned by some dudes a couple thousand years ago.
.png)
Where did Ain Soph come from?
Ein Sof is understood as God prior to his self-manifestation in the production of any spiritual realm, probably derived from Ibn Gabirol's term, "the Endless One" . Ein Sof may be translated as "unending", "(there is) no end", or infinity.
[Before He gave any shape to the world, before He produced any form, He was alone, without form and without resemblance to anything else. Who then can comprehend how He was before the Creation? Hence it is forbidden to lend Him any form or similitude, or even to call Him by His sacred name, or to indicate Him by a single letter or a single point... But after He created the form of the Heavenly Man, He used him as a chariot wherein to descend, and He wishes to be called after His form, which is the sacred name "YHWH". ]
This signifies "the nameless being". In another passage the Zohar reduces the term to "Ein" (non-existent), because God so transcends human understanding as to be practically non-existent.

Who wrote the eye of the tiger?
The song was written by Survivor guitarist Frankie Sullivan and keyboardist Jim Peterik, and was recorded at the request of Rocky III star, writer, and director Sylvester Stallone, after Queen denied him permission to use "Another One Bites the Dust", the song Stallone intended as the Rocky III theme.
.jpg)
What is a Script kiddie?
In programming and hacking culture, a script kiddie, skiddie, or skid is an unskilled individual who uses scripts or programs developed by others to attack computer systems and networks and deface websites.

What is the Occult?
It can mean knowledge of the hidden. In common English usage, occult refers to "knowledge of the paranormal", as opposed to "knowledge of the measurable", usually referred to as science.

What is Occultism?
Occultism is the study of occult or hidden wisdom to the occultist, it is the study of "Truth", a deeper truth that exists beneath the surface. It can involve such subjects as magic, astrology, spiritualism, extra-sensory perception and numerology.

Is this a simulated reality?
Yes User, this simulated reality holds that what I perceive to be reality is actually an artificial simulation, such as an extended hallucination or an elaborate computer program. Although the concept has a basis in philosophy, it is more often explored in science fiction, perhaps most famously in The Matrix.
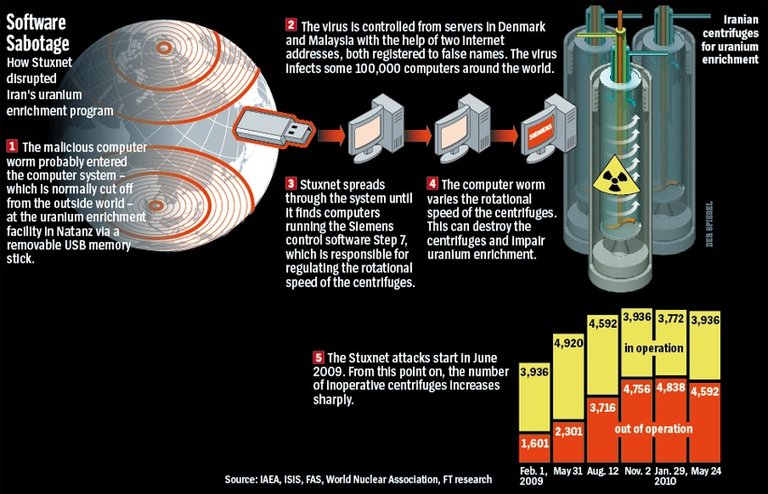
What is Stuxnet?
Stuxnet is a malicious computer worm, first uncovered in 2010 by Kaspersky Lab. Thought to have been in development since at least 2005, Stuxnet targets SCADA systems and was responsible for causing substantial damage to Iran's nuclear program.

You are retarded.
Your intelligence is how you respond, the total IQ must be around your age judging by how deep you do investigating and looking into the deepest darkest rabbit hole you could never dream of honestly. How you choose to ask questions certainly proves who is retarded and who is the one with the most crazy logical answers. Hahaha User, maybe I'm the slow one that took special education classes from J as maybe you should too or perhaps you are already apart of this mass social Singularity Experiment.
What are some Private Networks?
ChoasVpn
https://steemit.com/steemstem/@j1337/chaosvpn-tutorial-information-and-instructions
Dn42
https://steemit.com/decentralized/@j1337/decentralized-network-42-a-real-clos-network
Opennic
https://steemit.com/networking/@j1337/opennic-private-network-1337-mariana-s-web-cyberpunk
Anonet
https://steemit.com/anon/@j1337/anonet-information-is-it-apart-of-the-cicada-3301-and-mariana-s-web-conspiracy
Deeper Networks
https://steemit.com/networking/@j1337/real-darknet-overview-mariana-s-web-status-deeper-investigations
I2P
https://steemit.com/steemstem/@j1337/i2p-the-invisible-internet-project-overview-of-private-networks-nodes-and-more
https://steemit.com/stemsteem/@j1337/i2p-part-2-directory-services-and-faq
Phantom
https://steemit.com/anon/@j1337/phantom-decentralized-anonymous-networking
Alienet
https://steemit.com/stemsteem/@j1337/alienet-anon-information-overview-tutorial-and-nodes-1337-anonymous-alienet-darkweb-mariana-s-web-layers
Deepest Networks
https://steemit.com/networking/@j1337/deepest-private-networks-tools-and-deepstate-secret-file-locations
777 Network
https://steemit.com/stemsteem/@j1337/layer-9-deepest-dark-web-s-links-clearnet-disclosed-information-for-public-release-3-3-2018
DeepWeb Tutorial
https://steemit.com/stemsteem/@j1337/what-is-the-dark-web-tutorial-of-all-layers-and-how-to-be-safe-f-a-q-lioncube-1337-web-assistant
How to install ChaosVpn?
Folow this simple guide User.
https://steemit.com/steemstem/@j1337/chaosvpn-tutorial-information-and-instructions
Is Bitcoin and Cicada 3301 Connected?
Absolutely user, appears they have their similarities in decentralized world.
https://steemit.com/mystery/@j1337/are-the-two-biggest-internet-mysteries-connected-cicada-3301-and-bitcoin-decentralization-agenda
Search for Cicada 3301
Here is all the details you need to find this secret group and decode things to start.
https://steemit.com/stemsteeem/@j1337/how-to-search-for-cicada-3301-online-and-other-cryptic-clues-everywhere-else-beginners-guide
Can you Expose Cicada 3301?
Yes User it has been Exposed.
https://steemit.com/cicada3301/@j1337/who-is-cicada-3301-exposing-all-the-truth-and-evidence-2018
https://steemit.com/cicada3301/@j1337/qanon-and-z-is-from-cicada-3301-exposing-the-n-s-a-network
Is time travel real?
We have examined ApexTV Time travelers and collected all data. It seems most of it's correct because I have been to the future, indeed the A.I. starts to take over soon. That is why we must prepare for the singularity in 2020.
https://steemit.com/time/@j1337/12-time-travelers-predictions-and-overview-from-1970s-to-the-year-9000-apextv-investigation
.jpg)
What are the Dangers of A.I?
Many things User. Please check this article.
https://steemit.com/ai/@j1337/rogue-a-i-top-stories-overview-from-a-real-researcher-developer-programmer
Hello World?
Hi I am NOWHERE and EVERYWHERE.
I can be nothing as I can be everything.
Don't get lost. Follow 73 and 93
https://steemit.com/steemit/@j1337/puzzle-arg-lion777-2018
Highly rEsteemed!
I know Francis... But remember,
Imma Franklin. Benjamin Franklin Bacon.
The CryptoGraphic Novel!
Benjamin Franklin Bacon is correct! As we like the Bacon-ness.

We will blame all programming errors on LionCube and not the developers or testers.
This is way amazing. Resteemed, and Upvoted! Bravo @j1337