Now, the use of cryptographic algorithms is very modern, the encryption process is done already based bits instead of the letter again, as used steemit namely using a length of 256 bits.
https://steemit.com/steemit/@ibnu/nice-selection-of-steemit-in-choosing-256-as-hash-algorithm
https://steemit.com/steemit/@ibnu/security-of-digital-signature-algorithm-used-by-steemit-continued-of-my-post-about-security-of-hash-algorithm-used-by-steemit
Even the use of algorithms currently has the size bit long, even up to 2048 bits. But the whole thing came from the classical algorithms such as caesar system. And here i want to explain what is caesar system and how about the encryption process
Caesar Cipher is one the oldest cipher algorithm and most known in the development of the science of cryptography. Caesar cipher is a substitution cipher types that make up the cipher by way of exchange of characters in plaintext into exactly one character in chiperteks. This technique is also known as a single cipher alphabet.
Caesar Cipher cryptography algorithm is very easy to use. The core of these cryptographic algorithms is shifting towards all the characters in plaintext with the same shift value.
As for the steps taken to establish chiperteks with Caesar Cipher is:
1.Determine the magnitude of the shift characters used in forming the ciphertext to plaintext.
2.Replace characters in plaintext into ciphertext with based on a predetermined shift.
Here is an example of the use of algorithms caesar
A.Basic Caesar
Suppose that the key used is A = C, then A = C, B = D, C = E and so on with a plaintext = BITCOIN, then the resulting ciphertext is DKVEQKP. However, the use of these keys is less secure, so the development of algorithm formed by replacing the key with keywords.
B.Caesar by keyword
Keywords used as a series of letters to replace the letters in plaintext. The resulting series of letters of a keyword followed by the alphabetical order that have not been found in a keyword.
Examples of the use of keywords STEEMIT
If the plaintext is used BITCOIN then the resulting ciphertext is TDRELDK
However, the use of keywords is still considered unsafe since the middle to late letters are not changed or are still in the order. So, we need the randomization in a series of letters

C.Caesar with random keywords with fixed column order
Suppose keyword used is STEEMIT
Here are the steps to form a series of letters.
- Remove the same letters in keyword used
Then it will be a STEMI - These keywords determine the number of columns used
In STEMI said there are five letters so that the resulting 5 column - Sort the alphabet that has not been used on these keywords
4.This is the result series of letters
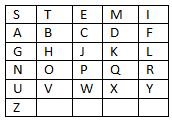

5.If used plaintext BITCOIN then the resulting ciphertext is AHQGPHJ
6.However, the use of the column still felt less secure because it can be easily analyzed by the attacker. Thus formed caesar system with random columns
D.Caesar with random keywords with fixed column order
Suppose keyword used is STEEMIT
Here are the steps to form a series of letters.
- Remove the same letters in keyword used
Then it will be a STEMI - These keywords determine the number of columns used
In STEMI said there are five letters so that the resulting 5 columns - Sort the alphabet that has not been used on those keywords, and provide the serial number on the keywords that begin near the letter A

4.Sort letters in each column starting from column on keywords that begin near the letter A

5.If used plaintext BITCOIN then the resulting ciphertext is CRUJXRQ
I got some information from this
https://sholeh012.wordpress.com/2011/10/03/caesar-cipher-dan-cipher-key/
And this is my facebook account
https://www.facebook.com/ibnu.tryrosadi