One common technique of attack involves saturating the target machine with external communications requests, such that it cannot respond to legitimate traffic, or responds so slowly as to be rendered effectively unobtainable. Such outbreaks generally lead to a server overload. In general terms, DDoS attacks are implemented by either forcing the targeted computers to reset, or consuming its resources so that it can no longer run its intended service or obstructing the communication media between the intended users and the victim so that they can no longer communicate adequately.
A typical DDoS attack where a hacker begins by exploiting a vulnerability in unique computer system and making it the DDoS master. It is from the master system that the intruder recognizes and communicates with other systems that can be compromised. The intruder loads cracking tools available on the Internet on multiple - sometimes thousands of compromised systems. With a single command, the intruder instructs the controlled machines to launch one of many flood attacks against a specified target. The inundation of packets to the target causes a denial of service. Cyber criminals launch low-threshold DDoS attacks, also known as“Dark DDoS” because they are a low-cost and easy way to intrude and map a network. Because the attacks are so short, typically less than five minutes in duration. for the sake of the question, you should start troubleshooting from the router. Try Closing all unused ports, use shields up! https://www.grc.com/shieldsup to check and see what other people can see from your connection.Some routers have a DDOS prevention/mitigation option,turn that on obviously.Turn off "respond to WAN ping"A DDoS attack attempts to push you off the internet by literally flooding you with data. A more powerful system can cope with the load better.
Now, I doubt this will happen, but if you do come under a serious DDoS attack, start logging the requests coming in. If it goes on for long enough you can get your ISP involved and have them ban certain IP ranges.
actions to protect your devices from becoming bots:
. Create and use strong passwords for all your devices. Do not use the default. This is especially important for smart devices, routers, and other devices with which you may not interact directly.
. Update your devices! Frequent Software update is often patched to remove known vulnerabilities, greatly strengthening your defenses.
. Monitor your devices. If a device is acting strangely, investigate it. One example is bounced email messages. If email messages are not reaching their destination, your device could be infected and sending spam as a part of a botnet.
. Run anti-virus scans and use other security tools to find and remove malicious software.
. Be careful to avoid infecting your devices. Avoid opening suspicious emails, attachments, or risky websites. Some anti-malware services include website security checks.

The above image is a cisco 1900 series that has high security enterprise-class management application and designed to configure firewall,
VPN, and IPS security services on Cisco network and security devices. You can use this cisco router in
networks of all sizes—from small networks to large networks consisting of thousands of devices. Cisco Security Manager Release 3.3.1 adds support for the Cisco
1900, 2900, and 3900 Series Integrated Services Routers.
REFERENCES
ddos attack-techperiod
router-cisco
Denial-of-service attack-Wikipedia

)
)
Nice one, keep it up.
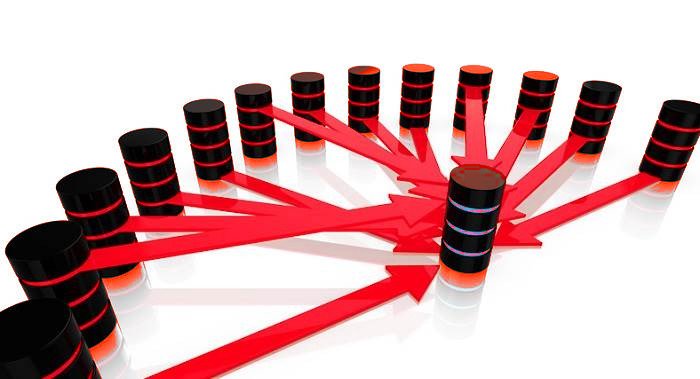
Typical Ddos Attack
Thanks boss, you really understand how it works.