A new Ransomware dubbed as Petya wreaked havoc Tuesday 6/27 across Europe and has spread to North America. Barely 7 weeks from the last WannaCry ransomware outbreak, users are again faced with the same threat that demands payment of $300 worth of Bitcoins.
However Kaspersky calls the malware "NotPetya" as their research results showed that the ransomware was a totally different variant and has never been seen before.
https://mobile.twitter.com/kaspersky/status/879749175570817024
Big companies like DLA Piper, Maersk and global pharmaceutical Merck have been hit causing hundreds of machines to be locked out. The last reports indicate more than two thousand machines have been infected.
The original Petya that hit in 2016 looks like this:

This is the ransom note for the latest variant:
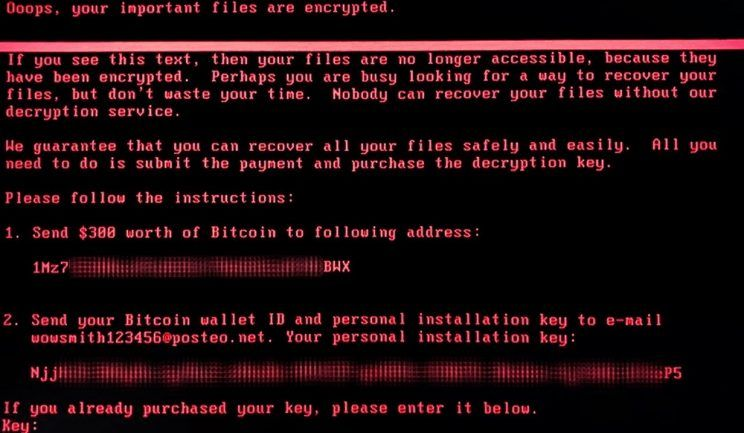
It uses the same Microsoft vulnerability EternalBlue to infect machines. The malware arrives on the user's system via email (clicking on malicious URLs/links).
Microsoft has released a patch MS17-010 to address the vulnerability but many companies have put off in patching their systems. The latest malware was reportedly deployed to millions of machines and programmed to spread via local area network shares.
With the surging prices of Bitcoin and other Cryptocurrencies, it is possible that this has fueled the increase in malware attacks demanding BTC payments. This article reports that companies have been stockpiling on Bitcoin to pay off cybercriminals. The report says a survey in 2016 of 250 IT professionals, a third of them are storing Bitcoins to be able to payoff the ransom in case their companies get infected.
DO NOT PAY
However best practices recommend that you do not pay. You are not sure that you will actually get the decryption keys to unlock your files, and you will probably set up yourself for a bigger attack once the criminal knows you are willing to pay.
For this variant, if you have been infected, and even willing to pay, there is apparently no way to contact the bad guy as the email address indicated in the ransom note had been blocked by the provider.
wowsmith123456 @ posteo [.]net
PROTECT YOURSELF
If you are a Windows user, there are several ways to protect yourself.
1.) If you bring your own laptop, do not connect it to your company's network (until patches have been placed).
2.) Do not click links in emails (even if you think the email is safe -- unless you are absolutely 100% sure.)
3.) Do not insert unknown USBs or USBs that you do not own, or have been connected to other machines.
4.) Change your passwords regularly
Check out my first two posts about personal information security:
I'll be posting updates on this malware.
Thanks for reading!
Congratulations! This post has been upvoted from the communal account, @minnowsupport, by cryptokash from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, theprophet0, and someguy123. The goal is to help Steemit grow by supporting Minnows and creating a social network. Please find us in the Peace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.
If you like what we're doing please upvote this comment so we can continue to build the community account that's supporting all members.
This post received a 0.8% upvote from @randowhale thanks to @cryptokash! For more information, click here!