It really amazes me sometimes how likely people can take internet security, in this day and age you would think that just about everywhere a computer network is setup people would do all they can to protect themselves from cyber-attacks… But often times as I have come to realize that is not the case. You really would be surprised just how vulnerable a lot of places you would not suspect actually are.
Case in point, I was at the airport recently and decided to spend some time taking advantage of the open Wi-Fi they made available, doing some internet surfing.

Well it did not take long before that part of my mind that harbours the hacker in me starts to tingle… and I think to myself how vulnerable is this place?
Well, since I have some free time why not find out for yourself I thought. So that is just what I did.
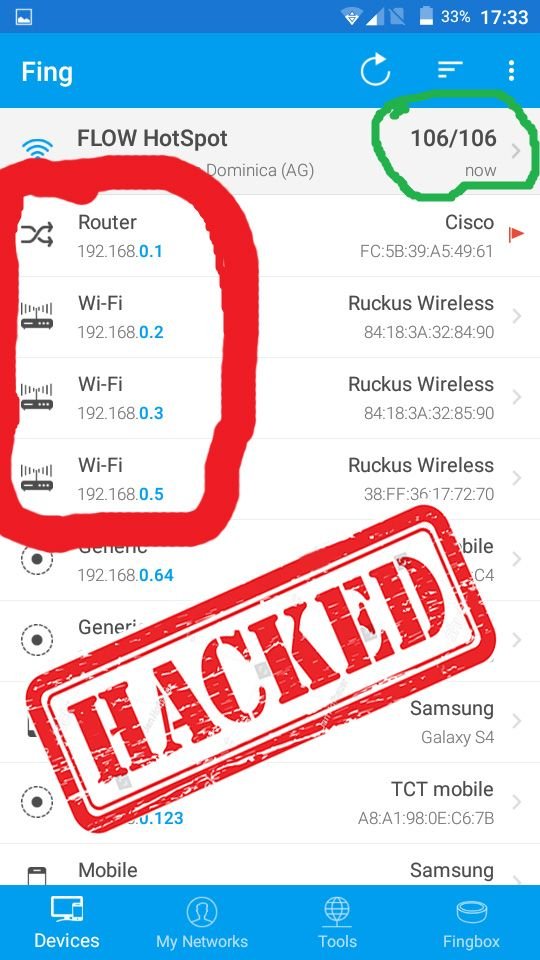
Already having access to the free network I might as well run a network scan to see who else is on it I thought. So I fired up a port scanner and mapped out the network to see who else was on it…
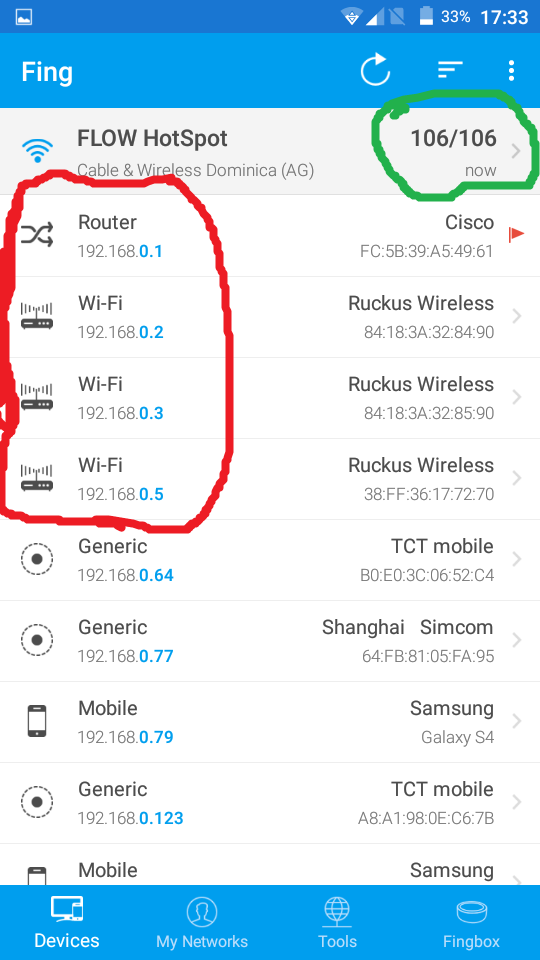
Well as you can see highlighted in the green circle it is quite a busy network… Which is to be expected it is an open Wi-Fi at an airport. 106 active devices on the network. Wow, the traffic capturing possibilities were tantalizing I must say. But for now the object of my attention shall be what’s in the red circle. We have a router and three access points well that has intrigued, so I decide to pick a target and make my move. I pick a device and scan it for open ports.

Well, well, well…. Yes, I find numerous open ports on the device including http on port 80. Now it is time to see if I can exploit that so I open the web browser and type in the ip address of the device.

At this point I am thinking I must be out of luck, this must be protect by a heavily fortified and complicated password. Who knows how long it could take me to brute force this? Hours? Days perhaps? Well I have come this far might as well give it a try, while I have time I tell myself… I decide to start the brute force attack and to my surprise I am able to gain access in a short amount of time.
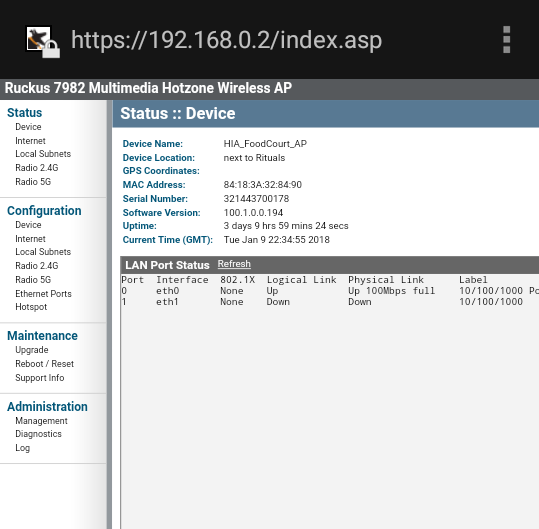
As it turns out they are still on the default user name and password. This is a practice that I see happen a lot. People apparently are not that informed when it comes to Cyber Security. It happens… So basically I was able to get full access to the access point and do whatever I wanted to the network. In a show of demonstration over my newly acquired power over their network I decided to hi-jack the Wi-Fi and make it my own.



Yes… It is good to be in control of your network, you should try to make sure you keep it that way.


Note Well this entire hack was done with nothing but an android cell phone...
I eventually returned everything back to the way I found it, but not before having my way with the network and seeing all the ways I could exploit it. Which reminds me DISCLAIMER this is for educationally purposes.
To recap the lessons learned here lets go over them:
If you have an open Wi-Fi, make sure it is on a segregated network from your main one… make use of Guest Networks they make life easier and keep you safe.
VERY IMPORTANT always change default passwords on network equipment… That is an absolute must if you want to protect yourself from cyber attackers. Avoid simple passphrases like words found in a dictionary. A good password should be at-least 8 characters long, contain Upper scale and lower scale letters, numbers and special characters.
That is it for part 1 trust me the rabbit hole of hacking goes deep. There is a lot more hacking that I did will I was there. So if you want to know more stay tuned for part 2.
If you liked this blog please be sure to upvote, comment and follow me for more great hacking, tips and tricks tutorials.
Until next time stay safe everyone, @kahdafy out… .. .

!originalworks
The @OriginalWorks bot has determined this post by @kahdafy to be original material and upvoted it!
To call @OriginalWorks, simply reply to any post with @originalworks or !originalworks in your message!
thank you very much original, good looking out
This post has gratitude of 0.51 % from @appreciator thanks to: @kahdafy.
thanks alot
Sneaky Ninja Attack! You have been defended with a 1.60% vote... I was summoned by @kahdafy! I have done their bidding and now I will vanish...Whoosh
I am very grateful for your support, thank you very much sneaky-ninja
Thank you @kahdafy for making a transfer to me for an upvote of 0.85% on this post! Half of your bid goes to @budgets which funds growth projects for Steem like our top 25 posts on Steem! The other half helps holders of Steem power earn about 60% APR on a delegation to me! For help, will you please visit https://jerrybanfield.com/contact/ because I check my discord server daily? To learn more about Steem, will you please use http://steem.guide/ because this URL forwards to my most recently updated complete Steem tutorial?
great news, thank you very much
This post has received a 0.79 % upvote from @booster thanks to: @kahdafy.
I am grateful for the gesture , that is excellent... thank you very much