⚠️ Digital viruses go airborne: BlueBorne vulnerability is cross platform and device, exposing almost everything Bluetooth connected ⚠️
Computer viruses, like their organic counterpart pathogens, are constantly evolving, and thanks to BlueBorne can now spread wirelessly, silently, without user involvement or knowledge, or even an internet connection.

TL;DR:
| Key details |
|---|
| • Attack vector exploits a bluetooth weakness |
| • Targets any vulnerable device that has bluetooth |
| • Can attack phones, printers, computers, smart TVs, watches, car audio, and IoT devices |
| • Requires no user interaction, Bluetooth pairing/'discoverable', or internet connection |
| • Require no preconditions/configurations aside from active Bluetooth |
| • No indication of compromise on afflicted devices |
| • Cross platform attack: Android, iOS, Windows, and Linux |
| Mitigation Currently: none, other than keeping Bluetooth disabled on all vulnerable devices, enable only when absolutely needed, or never if you can do without Bluetooth service. Await news of patch or other mitigation steps for your device/platform. |
The folk at Arimis Labs responsible for the discovery have produced this warning videos, concisely illustrating the danger of BlueBorne:
"It spreads locally over the air, via Bluetooth and the hacker does not need pair with the target device,"
"A comprehensive and severe threat"
Read on for further details and attack demonstration videos.
Researchers from Armis Labs discovered BlueBorne in April 2017, they then alerted tech companies in the hope that security patches and upgrades could be created before hackers could exploit the vulnerability.
Armis has also disclosed eight related zero-day vulnerabilities, four of which are classified as critical. An attacker using BlueBorne could take control of devices, access private/corporate data, penetrate secure “air-gapped” networks housing Bluetooth enabled devices, perform Man-in-the-Middle attacks, and spread BlueBorne malware to adjacent devices.
"You could be simply walking down the street [and] you walk past someone who is vulnerable and suddenly they are infected,"
"It's estimated to potentially affect up to 8 billion around the world, and that's because it's got the capability to infect Window, Linux, Android and iOS devices prior to iOS 10,"
"And that's a critical attack because it's airborne and can spread just by being near someone, and it affects most of the major operating systems and devices that are on the internet."
- Ty Miller, Threat Intelligence managing director
As yet, no malware exploiting this vulnerability is known to exist.
Patches for various platforms and devices are being developed and released. But, as yet, there is no comprehensive mitigation for vulnerabilities in this vector either. Airborne peer-to-peer vulnerabilities are beyond most current methods of endpoint or network protection.
The race is on.
"Current security measures, including endpoint protection, mobile data management, firewalls, and network security solution are not designed to identify these type of attacks, and related vulnerabilities and exploits, as their main focus is to block attacks that can spread via IP connections."
- Arimis Labs
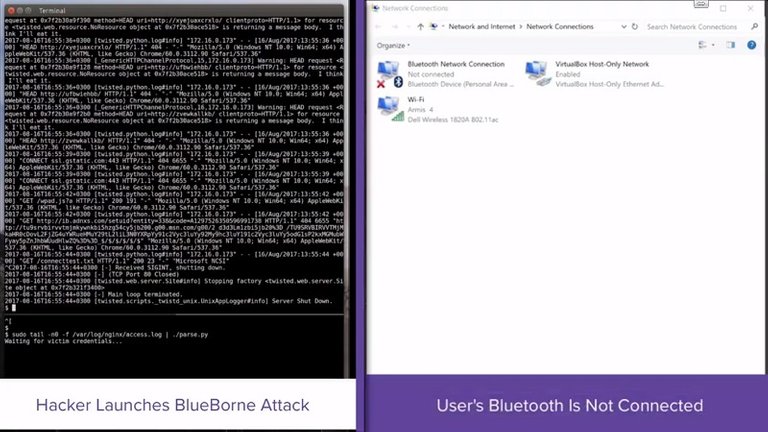
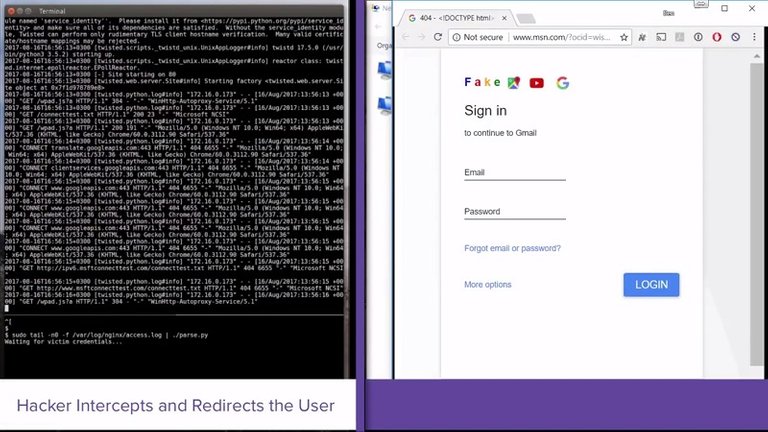
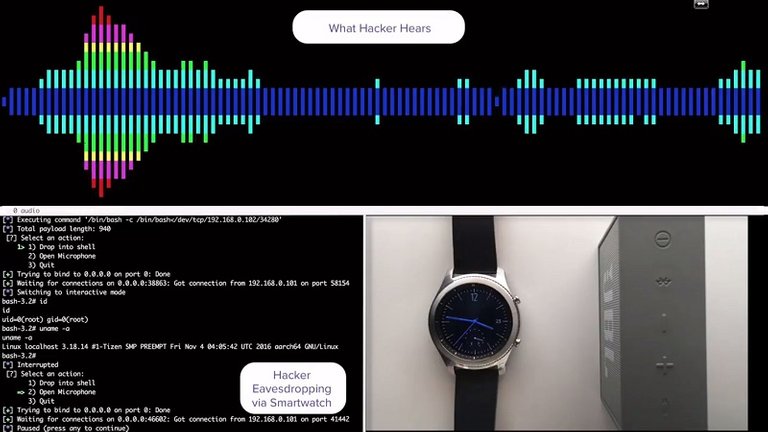
Arimis Labs have conducted tests using BlueBorne to stage successful attacks against Android, Windows, and Linux, as proof of capability. They documented these processes and produced the demonstration videos listed below by platform.
| Android: |
|---|
| Windows MiTM: |
|---|
| Linux: |
|---|
"If this was weaponised and turned into a self-propagating virus then you would see the initial infection point, you would see it spreading from there,"
-Ty Miller
Miller said risks of BlueBorne spread infections are still a possibility due to the lax attitude many people have about updating their security software and operating systems.
"Or when you start looking at your printers, the new TV's, new watches, home system, the medical appliances — they don't tend to get updated because they just sit there and people forget about them,"
There can also be reluctance on constraints on modifying software on bluetooth enabled engineering, plant, or medical equipment due to potential risks of impacting the operation of the device.
BlueBorne is the first significant airborne malware vector, there may be more to come. Hopefully @ausbitbank, @an0nkn0wledge, and others can help me keep an eye on this issue and post updates as they arise.
View Arimis Labs BlueBorne white paper here: http://go.armis.com/blueborne-technical-paper
All rights of names, logos, graphics, and research findings remain the property of their respective holders.
^vote, resteem, and comment below. Considerable effort has gone into researching, testing, and formatting for this article.
Hello, MAP23 has started! Please go to "Six of the Best" MAP23 Minnow Contest [Vote Now - Win Upvotes]. As a participant, please look at the suggestions to get the most out of the contest, especially creating a comment showcasing your best recent work. Good luck!
And don't forget, you are now a MAP Member and you can get further inspiration and assistance at the MAP Members Only Discord chatroom.
Thank you for considering me for inclusion, I'll reply to the MAP post with a selection of articles & resteem soon as I finish my current work tasks.
Wow... this actually reminded me of a manga called Chobit (by CLAMP) that spoke about something that can connect mobile devices (smart phone / smart pc even) without user's permission. This will let the hacker know exactly where the device is and send messages (or even commands too)
And from that manga, the smart devices are ACTUALLY android robots, and imagine that, if blue borne is malicious on that era, what will happen to smart bots?
I suddenly have the thought of the Terminator
upvotedGreat warning insights @neuromancer !
Great comment, thank you. There is much here that is very worth reflection:
Be safe, LNT (great moniker, BTW), eyes open and cognitive function in FULL STEEM!
Yes Patlabor was one of my favourite anime to watch when I was a lot younger.
And before I was awake the potential security threats, I thought it was really a cool thing.
Guess those who take the red pill will notice. These days, I keep my bluetooth on my mobile disabled unless I am doing some quick synchronising. Otherwise, it is not only an open security threat, it also drains my phone's battery power. lol.
Both true.
Patches for Bluetooth software, OS's, and devices are being developed and released, check regularly for updates on each Bluetooth enabled device. But, some devices and distros of 'Droid just become abandonware if the manufacturer/developer decides to move on and not look back, or if they go out of business.
Obsolescence is the only future for these poor minions.
You just scared the crap out of me with this post. lol I feel like Big Brother is watching me now through my laptop camera. Not a good feeling to have at all. lol How do you protect yourself from it? I mean what do you use on your devices to limit the risks of getting infected by this virus?
Snowden (based on a true story)?
BIG BROTHER IS watching
@awakentolife , have you watched the movie
I know he is, but this post just reminded me of it. lol
I have masking tape on my webcam, have done so for some time.
Thanks for your reply, apologies for alarming you but I'm glad you're alert now ;)
BlueBorne is a vulnerability (aka Attack Vector) in the Bluetooth standard that can be exploited by malicious code/actors. As yet no such malware is known to exist, but the attack vector definitely exists.
In light of this it is best to be prudent and exercise caution (see below).
As well as watching for device/software/OS patches I would also consider disabling Bluetooth on all devices, until absolutely needed, then disabling again after use, until such time as each device has ben patched and confirmed as no longer vulnerable.
Security is a practice.
Basically, I have to watch my Bluetooth usage and make sure I turn it off when I am finished. I usually don't use a lot of Bluetooth expect when I connect my wireless speaker to my phone or laptop. Besides that, I am not using it really.
Thank you for the tips brother. Have an amazing day. :)
That's the way, keep Bt disabled until needed, or if there's another means like stereo 3.5mm cable use that instead, but don't forget to look for news of patches for your device(s)/OS(s)/software and apply them if/when available.
Congratulations @neuromancer! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPPeace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.Congratulations! This post has been upvoted from the communal account, @minnowsupport, by neuromancer from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, theprophet0, someguy123, neoxian, followbtcnews/crimsonclad, and netuoso. The goal is to help Steemit grow by supporting Minnows and creating a social network. Please find us in the
Oh my goodness this is very scary thank you for making us aware of this as scary as it is, it shows technology has gone to new heights again.
It's what it does, because we make it so, because we want it so. Technology is an arms race, it can be beneficial or destructive, swords to ploughshares, it is all in how you play the game, and you must play. So play with those who do you no harm, take heed of those who give caution, trust few, obey none, question all. Nevertheless;
Disable Bluetooth on all devices if you do not use it, if you do then keep it disabled whenever not in use, or choose to do without it. Keep checking for news of patches and mitigation for each device/platform/software you use Bluetooth with for any developments or releases, apply them when available, but continue to be skeptical instead of lax.
And remember the most important rule:
STEEM ON!
This is a very interesting post. I was unaware of such a vulnerability.
Thanks for the informative summaries and videos. They make a compelling argument. I suppose the main lesson is to always keep things up to date, and hope that device makers can come up with a patch soon!
Thanks for your reply, I'm glad the article was informative for you.
As well as watching for device/software/OS patches I would also consider disabling Bluetooth on all devices, until absolutely needed, then disabling again after use, until such time as each device has ben patched and confirmed as no longer vulnerable.
Stay safe.
Thank you so much for this information. I've actually heard of it before but not as detailed as the way you put and d video u uploaded also help for easy understanding..
Thanks for your reply, I'm very glad the article was useful to you.