A firewall is a system or device to allow network lines to be set up to be safe when over the network and also to prevent network lines that are considered unsafe. in essence, the firewall device is deployed to a dedicated machine, and works on the gateway between the local network and the other network. Firewalls are basically used to control access to people who have access to private networks from foreign parties. today, firewalls are the generic meanings leading to systems for managing communications between two different networks. and for now most companies have access to the network or the Internet and of course the corporate network is in it, therefore the protection of the company's digital assets against hacker attacks is essential.
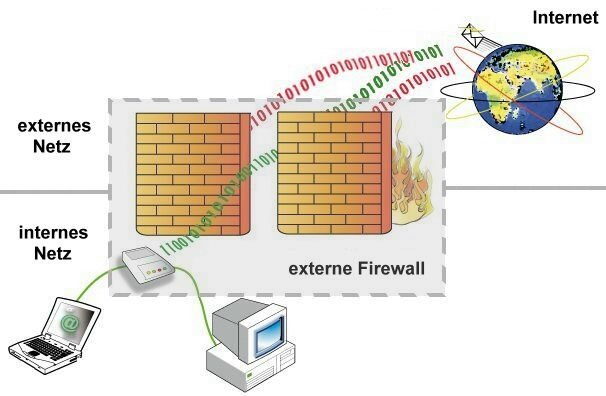
then the firewall is a system or device to protect the security of a network on the computer by filtering incoming and outgoing data on the network. data that is considered good to allow to pass the network as for data that is considered evil is not allowed to pass through the network. Firewalls can be software and hardware installed software to filter data packets. Firewalls can also be such a rule and are planted to be taught to IT staff in a company not to leak data of a company to another company. to prevent the type of social hacking enggeneering.
can also like to provide security on computer or network devices, such as putting the server in a special room and then locked. The key room is held by IT staff and then allowed to use the room because of the IT staff permission. this way works in addition to keeping computer or network devices physically lost by thieves or robberies, and also serves to keep lost data already stored in the computer device.
Firewall Function
-to Control or supervise data coming in on the network
a Firewall must be able to manage, filter and control data activities to be allowed to access private networks that have been protected by the firewall. Firewalls must be able to check the data packets going through the private network. as for the criteria of data that the firewall to allow data packets may pass or not, are:
-The IP address of source computer / clear IP address
- TCP / UDP ports are sourced from a clear source.
- The IP address of the destination computer must also be clear.
- TCP / UDP port destination data on the destination computer is clear
- The information from the stored headers into the data packet is clear.
- Authentication of access.
Proxy Application Firewall should be able to perform checks beyond just headers against data, as for this ability to sue firewalls to be able to detect against specific application protocol specifications.
-to Record any event transaction events occurring on the firewall. This is to Allow help as early detection of network hacking.
"Thank you for your attention"