Today I'm going to go over another wonderful resource that the EFF had produced. The opensource project is called HTTPS Everywhere and it's a browser plugin for Chrome and Firefox that aims at helping to protect your online security. At its core all HTTPS Everywhere does is make sure that you are using a secure and encrypted channel whenever you visit a website.
Making sure that you have a secure encrypted channel is important for ensuring online security and privacy. Those of us that live in the IT world know that the websites we browse to are not much more than plain text crossing the internet. It's your browser that renders and presents you with the user interface for the website you are looking at. But when you submit data to a website through a form or a login page you are sending text from your computer to the server that hosts the website. Therefore it's important that when you load these websites that they are encrypted.
Let's take a look at why this is important. I'm going to show you two screenshots of Wireshark. Wireshark is the opensource network traffic analyzer and it shows us what your computer is doing when you tell it to load the login page of a WordPress site. The screenshot below is a representation of what happens when a user logs in to a WordPress site over a non-encrypted HTTP session. The highlighted text is sent to the WordPress server in clear text and if anyone were listening on the same network that person could intercept the traffic and take the username and password that was submitted to the form.
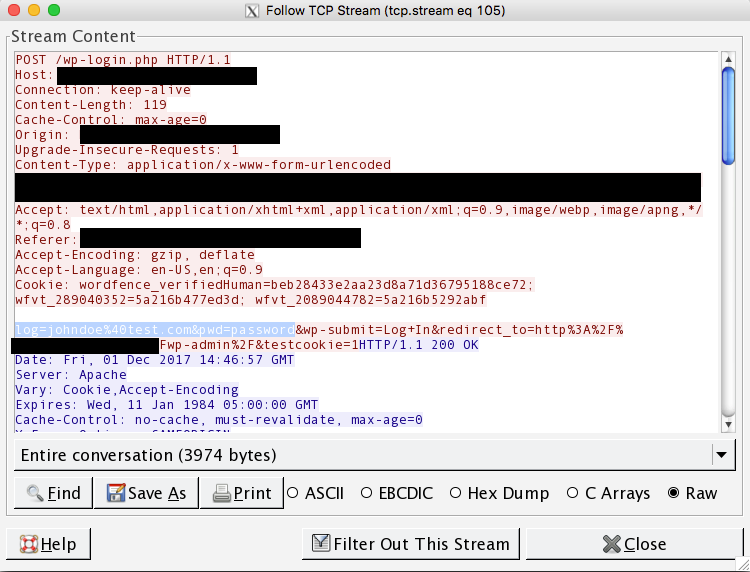
Now let's take a look at that same login form on Wireshark only this time I've submitted the credentials over an encrypted HTTPS tunnel. As you can see from the screenshot below, the data that is sent from the browser to the server is jibberish. That's because before submitting that data to the server, the browser and the server negotiated an encryption key and shared that key in a secure manner. This way each has the encryption key and can encrypt and decrypt data that is sent to and from the browser and the server.
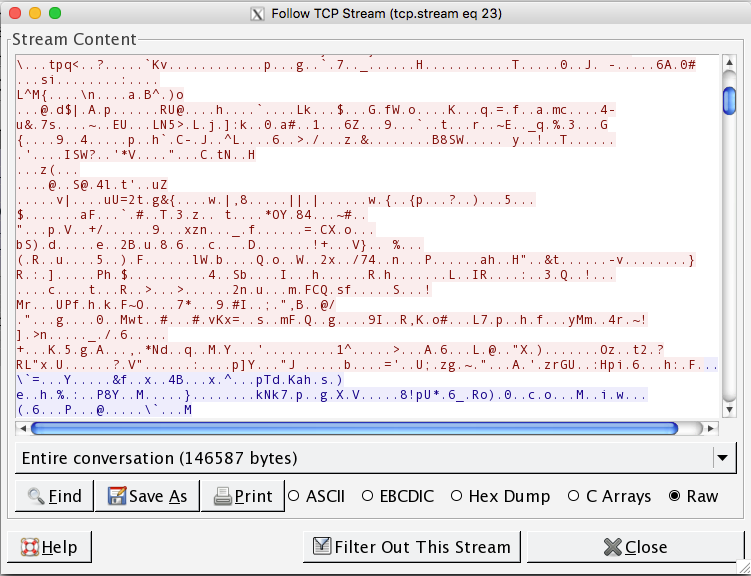
This is what HTTPS does for us, it protects some of the sensitive stuff that we so inherently trust on the internet. However, a lot of websites out there still allow your browser to communicate over un-encrypted HTTP sessions, even though they may have the ability to communicate over the secure encrypted HTTPS protocol. There could be a variety of reasons for this but the main one is a misconfiguration of the server. That's where the EFF's HTTPS Everywhere comes in. It checks each of the URLs your browser requests to see if the request is going over the secure HTTPS protocol. If any request is made over an un-encrypted channel HTTPS everywhere will check to see if that server will accept a secure HTTPS connection and then force the browser to use the secure connection over the unsecured one.
Installation Instructions
HTTPS Everywhere is really easy to install. On Chrome, you must hit the menu button and go to "More Tools > Extensions" (Alternatively, you could type chrome://extensions in the browser bar to get there).
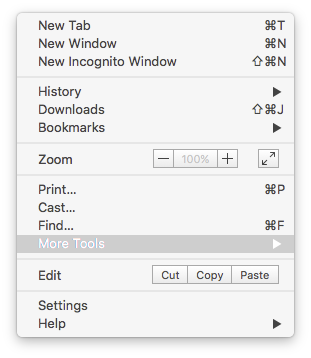
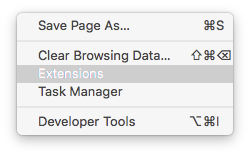
Once there scroll down to the bottom of the page and click on "Get more extensions".
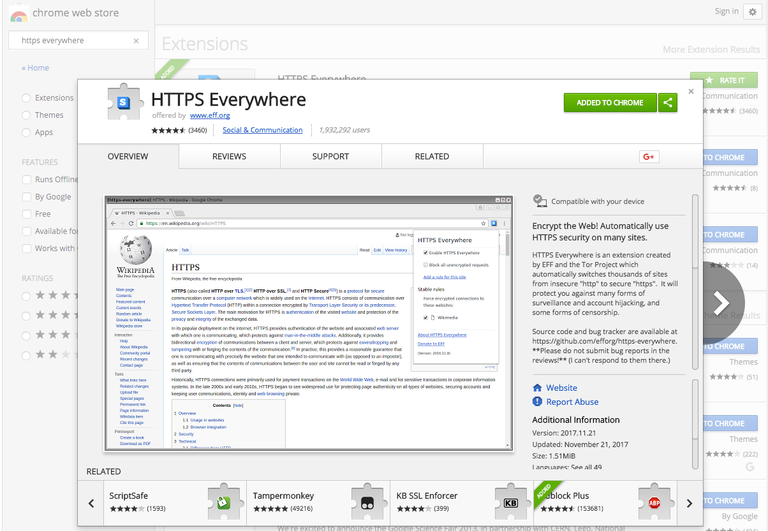
There you must search for "HTTPS Everywhere" then click "Add to Chrome"
Using HTTPS Everywhere
Once you have the plugin installed it will add a small icon to your browser that will look like this. You can click on this Icon ![]() to see some of the options, however, if you just take the default settings you will be in good shape to ensure that you are using a secure channel on most of the sites you would visit on any given day.
to see some of the options, however, if you just take the default settings you will be in good shape to ensure that you are using a secure channel on most of the sites you would visit on any given day.
I hope you've enjoyed this tutorial and that you enjoy the privacy and protection this open source project provides. If you are like me and care about your privacy and security I urge you to check out the other resources that the EFF has to offer.
Posted on Utopian.io - Rewarding Open Source Contributors
How does HTTPS differ from the standards being developed in health care like FHIR - that uses non-persistent connections and APIs?
@pchdmoon sorry I had to look up FHIR as I'm not familiar with it. From what I can tell though FHIR is just a data structure that is used to transfer patient records and other sensitive healthcare data. FHIR would use HTTPS as a means of encrypting that data in transit.
Think of it like the postal system. FHIR would be the letter or document you wanted to send and HTTPS would be the envelope. Except, in this case, the envelope is really a safe that you are sending because it encrypts the data.
Thanks for the reply. FHIR is the standard for moving data in health care. Groups like HL7 & CIMI are developing value sets of data needed to answer specific questions based on condition, population, etc. The pitch is that is will replace the need for databases in the future.
Hey @kslo I am @utopian-io. I have just upvoted you!
Achievements
Community-Driven Witness!
I am the first and only Steem Community-Driven Witness. Participate on Discord. Lets GROW TOGETHER!
Up-vote this comment to grow my power and help Open Source contributions like this one. Want to chat? Join me on Discord https://discord.gg/Pc8HG9x
Thank you for the contribution. It has been approved.
You can contact us on Discord.
[utopian-moderator]
Peace, Abundance, and Liberty Network (PALnet) Discord Channel. It's a completely public and open space to all members of the Steemit community who voluntarily choose to be there.Congratulations! This post has been upvoted from the communal account, @minnowsupport, by kslo from the Minnow Support Project. It's a witness project run by aggroed, ausbitbank, teamsteem, theprophet0, someguy123, neoxian, followbtcnews/crimsonclad, and netuoso. The goal is to help Steemit grow by supporting Minnows and creating a social network. Please find us in the
If you would like to delegate to the Minnow Support Project you can do so by clicking on the following links: 50SP, 100SP, 250SP, 500SP, 1000SP, 5000SP. Be sure to leave at least 50SP undelegated on your account.