Cross-Site-Scripting (XSS) is a vulnerability in web applications that makes it possible to execute malicious code (mostly JavaScript).
This is often possible through user input fields, in which the entries are not checked accordingly.
It is important to understand that JavaScipt is executed in the visitor's browser and not on the web server.
Source
In the following I would like to describe the three basic types
- Reflective
- Persistent
- DOM-based
with the XSS game from Google. Thus it is possible to playfully deal with Cross-Site-Scripting to learn how it works.
The goal is to execute a Proof of concept code that makes a pop-up appear using alert(). In the case of a "real" attack, the corresponding malicious code would be executed here, which reads out cockies, etc.
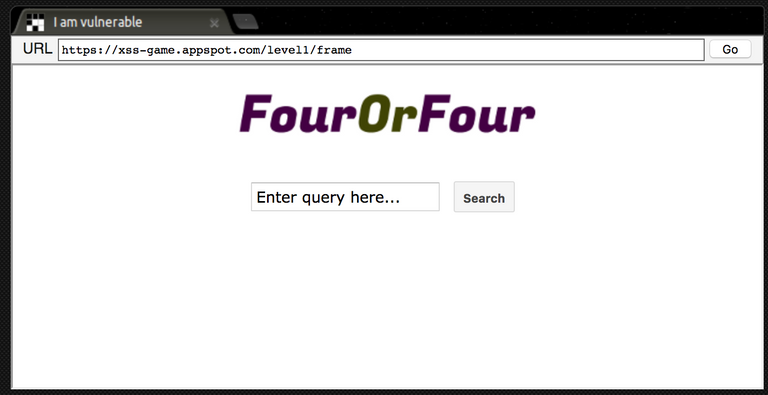
Level 1:
Here we can see an input field, which represents a search function.
If something is entered in this field, the corresponding text will appear after submission.
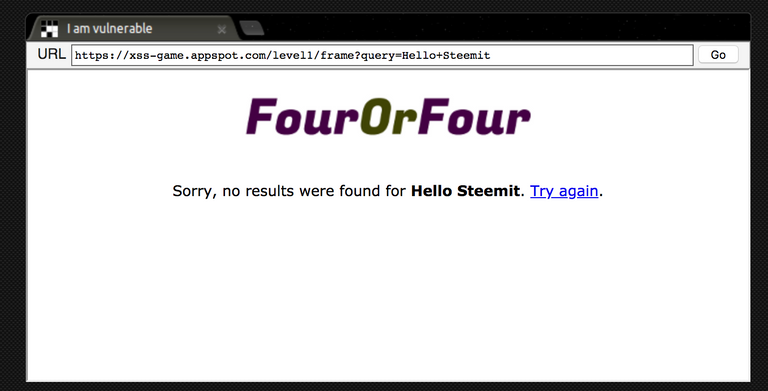
The easiest way to use XSS is to enter the code directly:
<script>alert("Hello Steemit")</script>
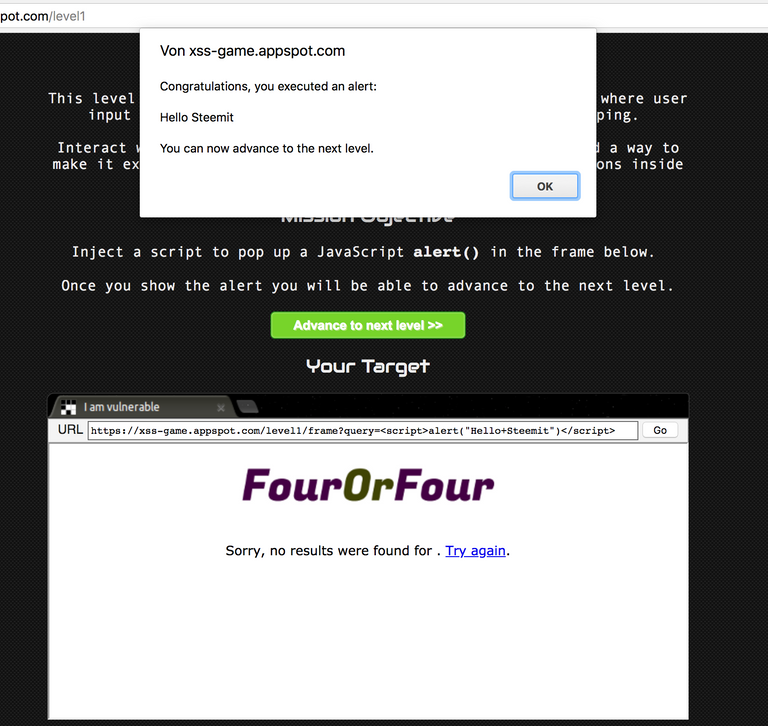
This is a so-called reflective attack. Reflective because the user input (in this case the searched text) is output again.
Level 2:
Here a forum is simulated. Text input is saved and made available to other users.
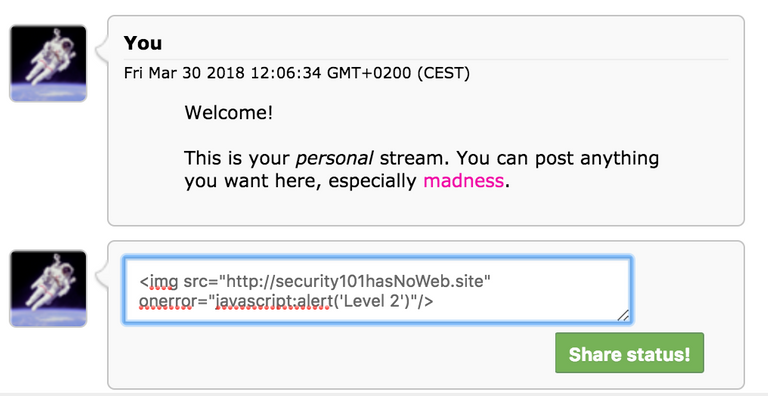
The direct input of the script as above is not possible here. By including an image that cannot be loaded, our code is executed in the onerror event.
This is called a persistent attack. Persistent, because the code (in this case via a comment function) is stored on the web server. Every time a user loads the page, the code is executed in the browser.
Level 3:
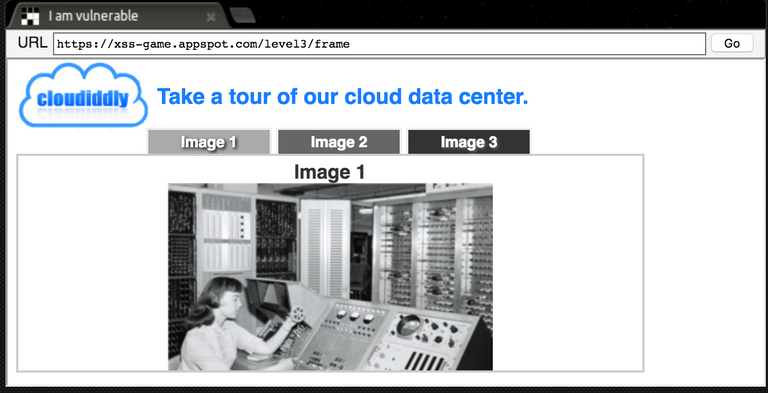
Here we have no input field in which we can write. By clicking on one of the tabs the corresponding picture changes.
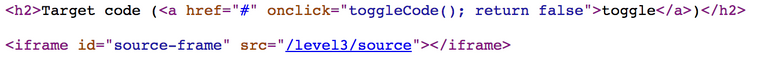
A look at the source code gives us insight into how it works
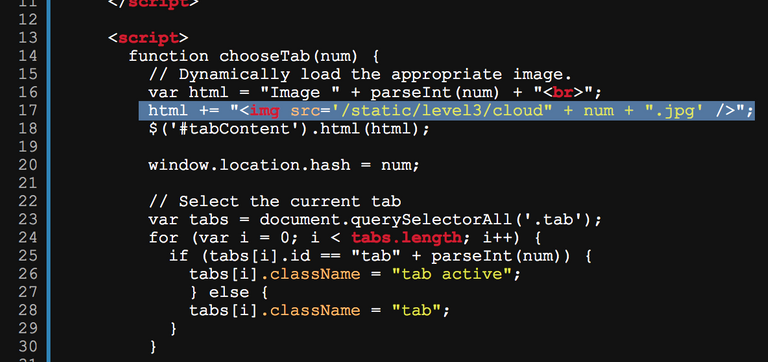
The image is loaded depending on the tab you clicked. The file names are composed according to cloud1.jpg, cloud2.jpg, cloud3.jpg.
By inserting a simple ' we "break" out of the JS code, and then execute the corresponding code as before via the HTML event onerror:
https://xss-game.appspot.com/level3/frame#3' onerror='alert("Level 3.")';
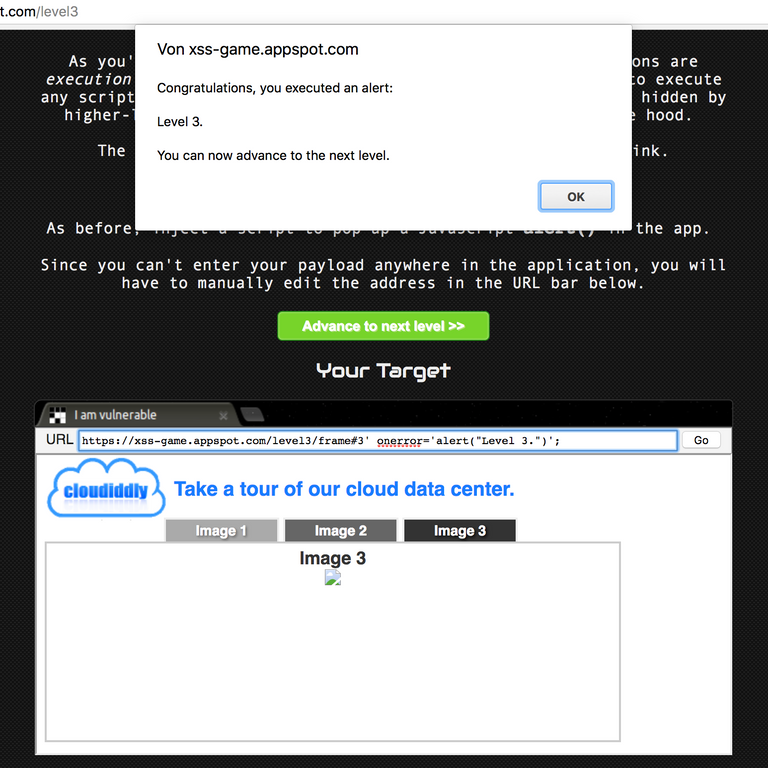
This type of attack is called local or DOM-based cross-site scripting. This manipulates the Document Object Mmodel.
How do I protect myself as a visitor to a website?
By deactivating JavaScript, e.g. by using appropriate browser addons, no more code is executed. Of course, this may limit the functionality of the website.
How do I protect my web application?
By using appropriate tools such as DOM Snitch tests can be performed during development.
Take a look at Reviewing Code for XSS and XSS Filter Evasionfrom OWASP for further Informations.
I hope to have given you a rough overview. If you have any further questions, I will be happy to answer them in the comments. Otherwise you can try your hand at the next levels;)
Thanks for reading!

Good stuff @security101, upvoted and followed you.
Here guys you can find a real vulnerable site to play with:
https://steemit.com/security/@gaottantacinque/javascript-pills-3-download-a-file-programmatically-website-affected-by-xss-vuln
;)
Congratulations @security101! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
To support your work, I also upvoted your post!
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPDo not miss the last announcement from @steemitboard!