
Today Wikileaks published another set of documents from their CIA Vault7 archive. This time the documents are from US government contractor Raytheon Blackbird Technologies. They mainly contain Proof-of-Concept ideas and assessments for malware attack vectors, and were put together partly based on public information from security researchers, and partly from private companies in the cyber security field. The first document to be submitted to the UMBRAGE Component Library (UCL) project came just 2 weeks after Raytheon bought Blackbird Technologies for $420 Mllion. The documents span 9 months from 11/21/2014 and 9/11/2015.
Raytheon Acquires Blackbird Techologies for $420 Million - Wall Street Journal - 11/05/2014
Raytheon Co. said Wednesday that it has acquired surveillance and cybersecurity company Blackbird Technologies for $420 million, a move that will strengthen the Pentagon’s third-largest supplier’s intelligence business.
UMBRIDGE Component Library
The UMBRAGE team maintains a library of application development techniques borrowed from in-the-wild malware. The goal of this repository is to provide functional code snippets that can be rapidly combined into custom solutions. Rather than building feature-rich tools, which are often costly and can have significant CI value, this effort focuses on developing smaller and more targeted solutions built to operational specifications.

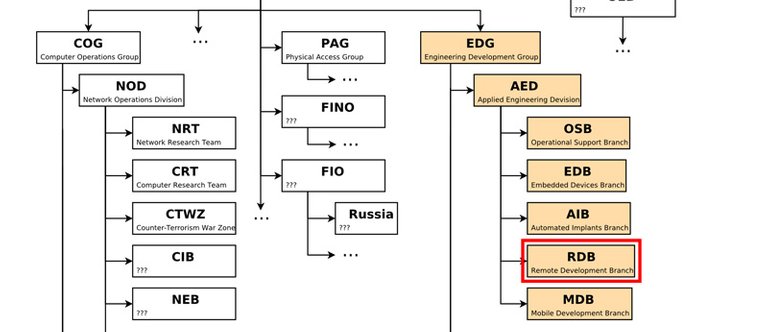
Raytheon Blackbird Technologies were used by the CIA as a technology scout for the Remote Development Branch (RDB). They analyzed malware attacks in the wild and gave recommendations to CIA development teams for further investigation and proof of concept development for their own malware projects. There are 5 documents in total. Below we shall break each one down and discover exactly how they work.
Raytheon is a major U.S. defense contractor and industrial corporation with core manufacturing concentrations in weapons and military and commercial electronics. It was previously involved in corporate and special-mission aircraft until early 2007. Raytheon is the world's largest producer of guided missiles.
Blackbird Technologies provides a unique opportunity for individual inventors and small companies to realize the value of their patents. By using in-house expertise, rather than expensive law firms, Blackbird Technologies is able to litigate at reduced costs and achieve results that equal or exceed what a law firm would recover.

CSIT 15083 -- HTTPBrowser
Emissary Panda, Chinese Hacking Group, Infiltrated US Aerospace, Energy Companies With 'Watering Hole' Sites - International Business Times - 08/07/2015
A Chinese hacking group identified as Emissary Panda has been blamed for setting up more than 100 “watering hole” websites that stole data from aerospace, energy and healthcare companies, as well as various government embassies.
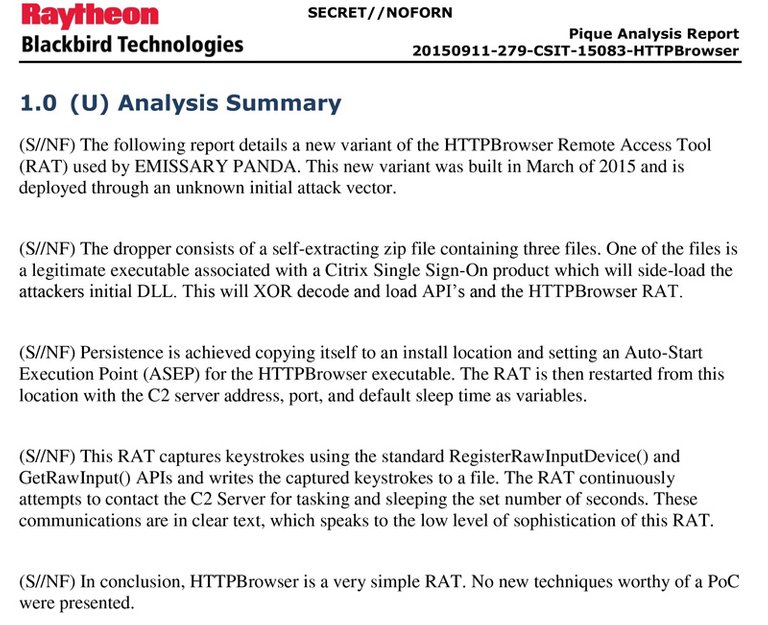
As we can see this exploit was was stolen from Chinese hackers.
CSIT-15085-NfLog
Who is Samurai Panda - Crowd Strike - 04/12/2013
Samurai Panda is interesting in that their target selection tends to focus on Asia Pacific victims in Japan, the Republic of Korea, and other democratic Asian victims. Beginning in 2009, we’ve observed this actor conduct more than 40 unique campaigns that we’ve identified in the malware configurations’ campaign codes.
The implant delivered by Samurai Panda uses a typical installation process whereby they leverage a spearphish with an exploit to get control of the execution flow of the targeted application. This file “drops” an XOR-encoded payload that unpacks itself and a configuration file. Next, the implant, which can perform in several different modes, typically will install itself as a service and then begin beaconing out to an adversary-controlled host. If that command-and-control host is online, the malicious service will download and instantiate a backdoor that provides remote access to the attacker, who will see the infected host’s identification information as well as the campaign code.

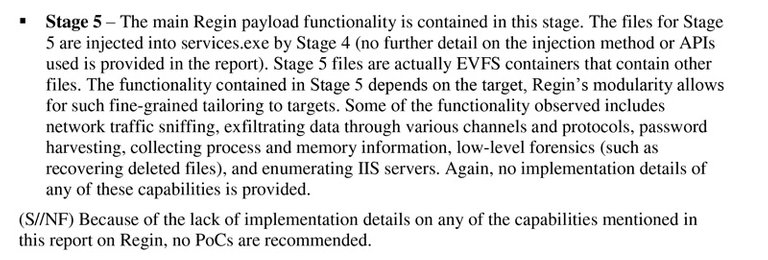
Symantec-Regin
Regin: Top-tier espionage tool enables stealthy surveillance - Symantec - 11/23/2014
An advanced spying tool, Regin displays a degree of technical competence rarely seen and has been used in spying operations against governments, infrastructure operators, businesses, researchers, and private individuals.

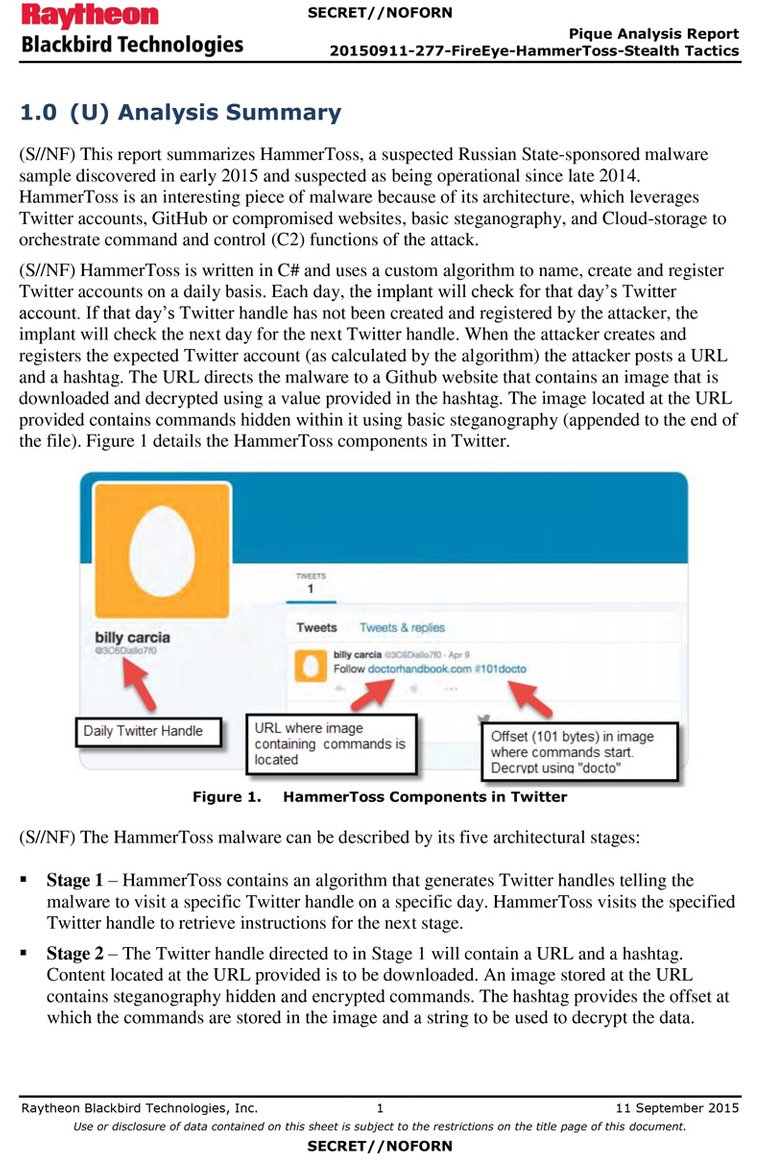
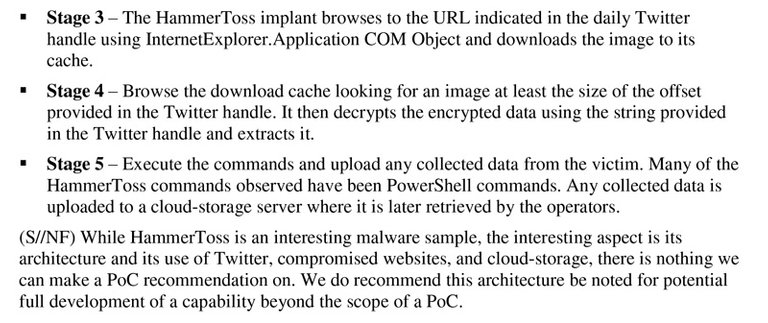
FireEye-HammerToss
Uncovering a Malware Backdoor that Uses Twitter - Fire Eye - 07/09/2015
It hides in network communications, in all the noise—designed so that defenders can neither detect nor characterize its activity. But its purpose is transparent: to use Twitter, GitHub, and cloud storage services to relay commands and extract data from compromised networks.erations against governments, infrastructure operators, businesses, researchers, and private individuals.
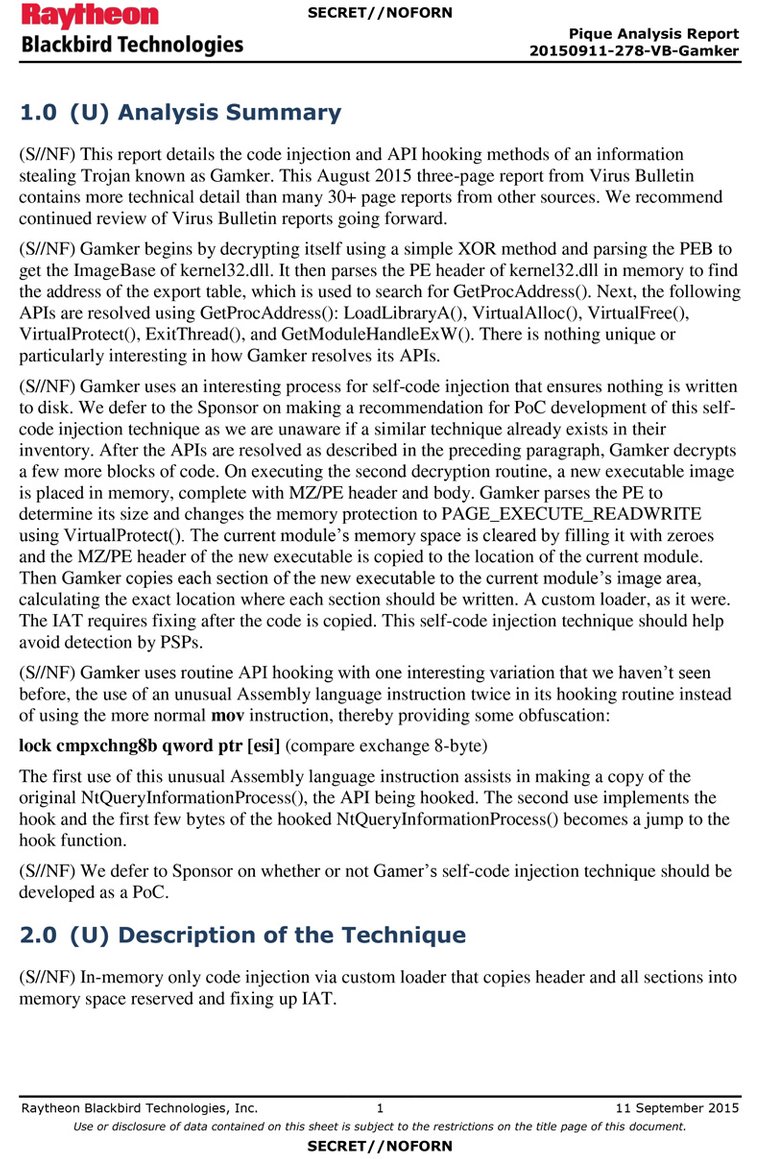
Gamker
Not a GAMe maKER - Virus Bulletin - 08/26/2015
Gamker is an information-stealing trojan which uses simple decryption, then drops a copy of itself using a random filename and injects itself into a different process. Raul Alvarez looks into its code injection routine and at the twists in its API-hooking routine.

It is incredible the amount of information still being released by Wikileaks CIA Vault7 archive. This is still only part 1 and I estimate it to be no more that 5% of the total archive. Part 2 is called Media Ops and is imminent.

good post
Thanks for the vault 7 article. Please keep them coming! We can't trust the MSM to report on it.
Nice work sir i like your article alot it surely helps the peoples. keep up your good work sir.
Much respect. Thank you.
This post got a
16.67% upvote thanks to @fortified - Hail Eris !"Secrets and lies": the Trump-Russia scandal lands the cover of People magazine - Vox
https://steemit.com/news/@nubian-oracle/secrets-and-lies-the-trump-russia-scandal-lands-the-cover-of-people-magazine-vox
Please don't spam my comments with plagiarized material.
Thank you.
Very interesting post! Hopefully we'll see some of this stuff on Github.com like we did the last leak.
Maybe. I think that may have been the NSA dump from @theshadowbrokers
Good share - institutional deployment of spyware, malware, and cyberwar have become the norm on the internet.@fortified I came by to say Hi!
Hello. Yes the whole internet is broken by the looks of it.
The same ole formula: create the problem, get the citizens' reaction, implement agenda compliant solution.@fortified I see the ruling class assaulting the freedom features connected to the internet with censorship, cyberattacks, bots, disinformation ops, bandwidth throttling, privacy invasion, and regulations - reigning in the internet while simultaneously implementing new tech and making the internet accessible to everyone (even remote villages in what the G20 vowed to have all citizens digitally connected by 2025). The worse the internet becomes the more need for the governments' solutions.
I posted an OPEN LETTER to blockchain programmers and executives, I would like your thoughts, do you think any programmers or executives will reply?
That's cool. Hopefully someone that understands what they are saying in that report can do something productive with it. :)