Hello. It is @hunhani.
Thank you for your interest and support in the previous posts. I will do my best to meet your expectations.
Last time, We have learned about the current status of technology development for the quantum computer.
Chapter 7. Can Quantum Computers Kill Blockchain? This time, we will deal with how valid the following sentence is. “quantum computer will eventually kill the block chain system.”
Simple Review

Hardware development is the first step for the implementation of quantum computers.
- The theoretical work has been quite advanced to this day. Although it is necessary to derive the quantum algorithms for a variety of problems, no matter how good the quantum algorithm is, the quantum computer can be implemented with the hardware to operate it.
- Experimentally, there has been a steady attempt to carry out actual quantum numerical calculations with a very small number of qubits, but there are still many technical steps to overcome.
Increase the number of qubits to handle at once!
- Unlike the bit, the efficiency increases exponentially as the number of qubits increases.
- It is not easy to handle multiple qubits at will.
- The performance will improve exponentially as the number of qubits that quantum computers can handle also grows, just as Moore's law of conventional computers doubles the density of integration in 18 months.
Global companies compete with quantum computer technology.
- The most prominent IT companies such as Google, IBM and Microsoft are pouring huge amounts of money into research for the development of quantum computers and are competing for the launch of commercially available quantum computers.
Korea still lags behind quantum computer technology.
- The level of quantum computer technology in Korea is only half of the developed countries. The technology gap with developed countries is about 7.6 years.
- However, the technology in Korea that controls the phenomena necessary for quantum computers is also competitive in the world, so there is a need for domestic large companies to invest with interest.
Korea company in the field of quantum cryptography communication.
- Quantum cryptography communication is a perfectly secure communication method against eavesdropping using the non-reproducible nature of quantum mechanics.
- Recently, in June 2017, SK Telecom overcame the distance limit of quantum cryptographic communication and laid a foundation for long distance communication.
Arrival of age of quantum information!
- The Technology Review published in February 2017 by the Massachusetts Institute of Technology (MIT) predicted the arrival of the age of quantum computers in the 'Ten Innovative Technologies of the Year'.
- The age of quantum information is approaching faster than we thought.
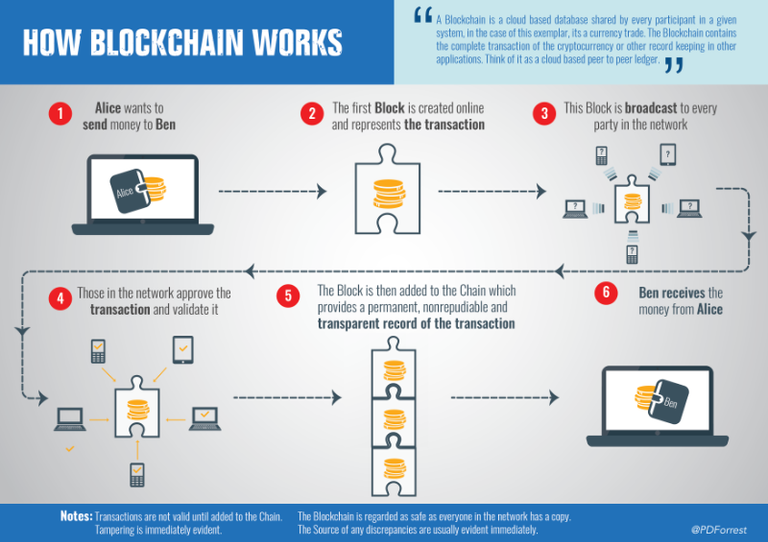
Blockchain system
This is what many people already know, but I will keep it up. Blockchain is a chain-like structure of blocks, which are the books on Peer to Peer (P2P) transaction data are recorded, and connected in sequence according to time. Once every 10 minutes, the transaction specifications were bundled into a single block and then make each block into a public record, like a chain. The entire block of the transaction book are exposed and distributed to all network participants using the blockchain to be managed. 51% of blockchain network must agree that each block is a valid transaction through consensus so that new blocks can be linked to the existing blockchain and the transaction records which are once connected blockchain is permanently stored in an unmodifiable state. If someone wants to manipulate the transaction details, it is necessary to unrealistically operate the whole blockchain by hacking all the network participants' computers within 10 minutes of forming one block. Therefore, in principle, this is not possible. Transparency, fairness and safety are guaranteed at the same time. In addition, without the need for a third party intervention, the blockchain system itself authorizes direct inter-personal transactions in real time through autonomous delegation, thus realizing transaction authorization and decentralization of information.
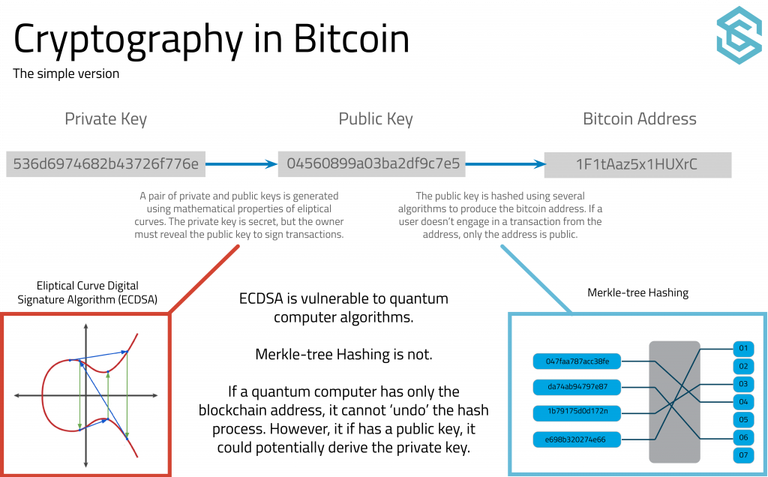
The end of cryptocurrency?
As you all know, the cryptocurrency uses a block chain system. Let's take bitcoin for example. The bitcoin receiver shares the public key with the sender. The public key corresponds to a wallet address, which is generally not a problem when it is exposed to others. To use bitcoin, the bitcoin holder must use the private key. If someone else finds out their private key, they can use that bitcoin. Private keys are protected from algorithms that use the difficulty of a large number of prime factorization. Existing super computer can not even dream to solve them, but quantum computer can calculate a private key from a public key in just a few minutes. If someone find out the private key of the address, it is instantaneous that the balance will be stolen. Theoretically, if the quantum computer finds out all the private keys, it can access all the bitcoins. For this reason, when the quantum computer is commercialized, it is considered that the current blockchain system can collapse by destroying both the public key and private key.
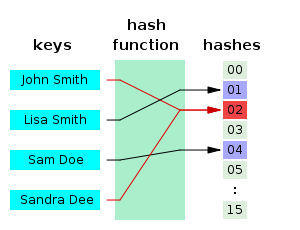
Algorithm used by bitcoin
Bitcoin uses the Secure Hash Algorithm (SHA) designed by the USA National Security Agency (NSA). A hash is a value obtained by a function that converts data of arbitrary length into data of fixed length (which finds the actual physical address from the virtual address). Since the hash function is deterministic, the original input data is different if the two hash values are different. At the same time, the hash function is not a one-to-one function, so even if it has the same hash value, it does not guarantee that the original input data will match 100%. Therefore, even if the input data changes slightly, the hash value greatly changes. Hashing makes it easy to find duplicated records in a large repository, which not only accelerates database searches, but also makes it easier to structure the ste of data. Because of this, hash is widely applied to computer software capable of very fast data retrieval. Furthermore, the cryptographic hash function has been applied to the cryptocurrency as well as the bitcoin, based on the fact that the integrity of the transmitted data can be verified and the hashing value alone makes it difficult to determine the original input data.
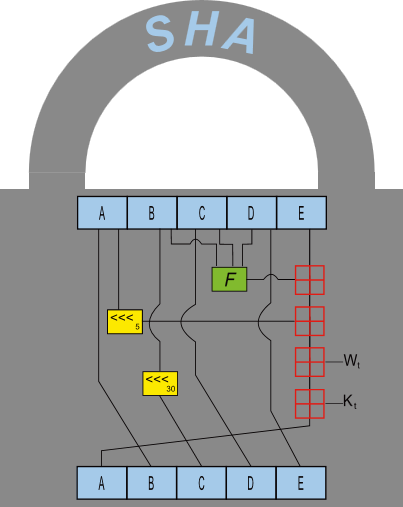
SHA? ECDSA? What is that?
Returning to the SHA again, the SHA function represents a set of cryptographic hash functions related to each other. The first function in the SHA function family is officially called SHA, but it is also called SHA-0 to distinguish it from later designed functions. Two years later, SHA-1, a variant of SHA-0, was announced, and four variants of SHA-224, SHA-256, SHA-384 and SHA-512 were announced in succession. SHA-1 is the most used of SHA functions and is used in many security protocols and programs such as TLS, SSL, PGP, SSH, and IPSec. Current bitcoin also depends on SHA-256. Although SHA-256 is now very safe, one day, if a quantum computer is commercialized, we must use a much stronger encryption algorithm than the SHA series.

It can also be used for mining instead of hacking!
Bitcoin key generation is managed by ECDSA (elliptic curve digital signature algorithm). The public key is created by multiplying the randomly generated private key by the points of the predetermined elliptic curve. With elliptic curve multiplication, the private and public keys are paired with each other and protected by a set of non-reversible hashing functions. Miners must find a solution to a specially designed hash problem to authenticate transactions in the block chain and be rewarded with the newly generated bit coin. The quantum computer can use Grover's algorithm to find a unique input value with a high probability in the black box function that generates the measured output value, thereby improving the second speed in the hash function and reducing the length of the generated key by half. Therefore, a miner using a quantum computer can significantly improve the speed at which a hash problem solution can be found. On the other hand, the length of the generated key may be reduced and the security effect may also be reduced. This can be solved by artificially doubling the length of the key. Of course, this approach can cause controversy regarding block size limitations, and above all, the fork implementation can be much more difficult.

Cryptocurrencies against a quantum computer
There are some cryptocurrencies developed for the purpose of countering quantum computers, such as QRL (Quantum Resistant Ledger) and Byteball (GBYTE). They use a totally new block chaining system designed to be particularly secure for quantum computers. In particular, unlike blockchain systems used by other cryptography, QRL can apply a pre-quantum secure signature for transactions using a hash-based signature scheme called the eXtended Merkle Signature Scheme (XMSS). In addition, QRL uses a proof-of-stake algorithm with low power consumption through iterative hash-chains and provably secure hash-based pseudo-random number functions. It is possible to operate a signature that is 25% smaller than the cryptocurrencies using a conventional signature scheme vulnerable to a quantum computer, so that QRL can run the node even in a low-power device such as a laptop, and is based on the most secure and verifiable practical blockchain system.

Conclusion
At a time when a quantum computer is not commercially available, if some forces own a quantum computer and exploit it, it will pose a huge threat to all industries of modern technology based on IT as well as cryptocurrency. Furthermore, it will have unimaginable adverse effects throughout the military, financial and administrative security sectors. The computing power of a quantum computer can be used to disrupt the cryptocurrency market by hacking the blockchain system, but it can also be used to enhance the security of a blockchain network and mine the cryptocurrency. Ultimately, to protect cryptocurrency from quantum computers, we must incorporate a new cryptographic standard into existing cryptographic protocols that can stand up to quantum computers. There are already a number of cryptographic developers developing technologies against quantum computers, and the basic technology already exists. But it would take time for such technology to be introduced and used throughout the cryptocurrency community. We still have enough time to prepare. My personal opinion is that, even if the threat of a quantum computer is realistic, we expect to adopt a new, appropriate standard that can handle quantum computers in a block-chain network.
I finally reached the end of the long story, [Quantum Computer & Blockchain Security]. Thank you for reading the difficult and long story. I want to deliver it as easily as possible, but this topic is very difficult for everyone. If you comment your question, I will reply to you as easily and concisely as I can.
Previous Story
- [Quantum Computer & Blockchain Security] Chapter 0. Introduction
- [Quantum Computer & Blockchain Security] Chapter 1. Quantum computer! What the hell is different with ordinary computer?
- [Quantum Computer & Blockchain Security] Chapter 2. Magical phenomena of nature, Quantum Superposition & Entanglement.
- [Quantum Computer & Blockchain Security] Chapter 3. Janus-faced quantum computer Quantum Parallelism and Quantum Communication Security
- [Quantum Computer & Blockchain Security] Chapter 4. Quantum Information Processing using Qubits
- [Quantum Computer & Blockchain Security] Chapter 5. Technological Challenges to Overcome for Quantum Information World
- [Quantum Computer & Blockchain Security] Chapter Chapter 6. Current Status of Technology Development for Quantum Computer
- [Next-generation Transportation] Hyperloop! Why is it so special?
- [Review] 18 Stories to See “Interstellar” Movie More Fun with Physics
- Engineer Dream Diodes with a Graphene Interlayer
- All images used in this post are from Google Images.

I got frightened after reading this article. What will happen to the crypto world with the invasion of quantum computers? I wish the collapse of quantum computers.
Hey great article! I love quantum computing and the amount of funding behind quantum computing has exploded the last few years.
However, wouldn't quantum computing based cyber attacks pose a much greater threat to everything else before cryptocurrency? I mean just think... how much damage can a team of hackers with a quantum computer do to the stock exchanges of the world? To the Department of Defense? To all Global Banks and Financial institutions? Governments, National Reserves, Military Installations and anything else connected to the internet in some way are much more vulnerable than blockchains.
Cryptocurrency is the most protected market in the world and I think we should all be more concerned about the possibility of just about everything else getting hacked first...
Regardless, thanks for the awesome breakdown. Your information is spot on and it looks like you spent a lot of time working on this. Well done. Followed!
Great catch. Therefore, I have already said that "it will have unimaginable adverse effects throughout the military, financial and administrative security sectors." Surely, the impact of quantum computers on cryptocurrency market may not be more significant. But I want to answer to the question "Can Quantum Computers Kill Blockchain?" and deliver this particular topic in a general way. Thanks for reading and following!
Congratulations @hunhani! You have completed some achievement on Steemit and have been rewarded with new badge(s) :
Click on any badge to view your own Board of Honor on SteemitBoard.
For more information about SteemitBoard, click here
If you no longer want to receive notifications, reply to this comment with the word
STOPEOS baby!!!!!!
Very good ! I am repost you story!
Thanks.
To be honest, I have no idea what the heck I even read, but, thanks for the share anyway. You gave me something to think about, learn about, research about. Will come here for more.. Cheers ;)
Your comment gave me a great motivation. Thank you.
Aww, that's so nice to hear. I'm glad :) Keep up with good stuff @hunhani
Thanks for your support!
You will be amazed to read, about how BCH bitcoin cash got to 3rd position,
https://steemit.com/cryptocurrency/@ronaldmcatee/bitcoin-cash-bch-bubble-or-real-thing
Thanks.
Quantum Computers will bring us advantages but also disadvantages. Good things can always be used for good and bad things. Anyways your post is awesome !. I can see the effort you putted in this article. Keep it up :).
Thanks for your evaluation. It feels really good when someone knows the effort I have written.